Leaderboard
-

Skarz
Full Member25Points96Posts -

whoknows
Full Member+19Points1,975Posts -

kruzco
Full Member16Points46Posts -

LordCoder
Full Member14Points191Posts
Popular Content
Showing content with the highest reputation since 07/20/2009 in Files
-
Lena's Reversing for Newbies
 48 points
48 points- 86,388 downloads
A collection of tutorials aimed particularly for newbie reverse engineers. 01. Olly + assembler + patching a basic reverseme 02. Keyfiling the reverseme + assembler 03. Basic nag removal + header problems 04. Basic + aesthetic patching 05. Comparing on changes in cond jumps, animate over/in, breakpoints 06. "The plain stupid patching method", searching for textstrings 07. Intermediate level patching, Kanal in PEiD 08. Debugging with W32Dasm, RVA, VA and offset, using LordPE as a hexeditor 09. Explaining the Visual Basic concept, introduction to SmartCheck and configuration 10. Continued reversing techniques in VB, use of decompilers and a basic anti-anti-trick 11. Intermediate patching using Olly's "pane window" 12. Guiding a program by multiple patching. 13. The use of API's in software, avoiding doublechecking tricks 14. More difficult schemes and an introduction to inline patching 15. How to study behaviour in the code, continued inlining using a pointer 16. Reversing using resources 17. Insights and practice in basic (self)keygenning 18. Diversion code, encryption/decryption, selfmodifying code and polymorphism 19. Debugger detected and anti-anti-techniques 20. Packers and protectors : an introduction 21. Imports rebuilding 22. API Redirection 23. Stolen bytes 24. Patching at runtime using loaders from lena151 original 25. Continued patching at runtime & unpacking armadillo standard protection 26. Machine specific loaders, unpacking & debugging armadillo 27. tElock + advanced patching 28. Bypassing & killing server checks 29. Killing & inlining a more difficult server check 30. SFX, Run Trace & more advanced string searching 31. Delphi in Olly & DeDe 32. Author tricks, HIEW & approaches in inline patching 33. The FPU, integrity checks & loader versus patcher 34. Reversing techniques in packed software & a S&R loader for ASProtect 35. Inlining inside polymorphic code 36. Keygenning 37. In-depth unpacking & anti-anti-debugging a combination packer / protector 38. Unpacking continued & debugger detection by DLL's and TLS 39. Inlining a blowfish scheme in a packed & CRC protected dll + unpacking Asprotect SKE 2.2 40. Obfuscation and algorithm hiding48 points -
Themida + WinLicense 2.x (Unpacking)
 19 points
19 points- 6,831 downloads
I want to release a new tutorial about the popular theme Themida - WinLicense. So I see there seems to be still some open questions mostly if my older unpack script does not work anymore and the unpacked files to, etc. So this time I decided to create a little video series on how to unpack and deal with a newer protected Themida target manually where my older public script does fail. A friend of mine did protect unpackme's for this and in the tutorial you will see all steps from A-Z to get this unpackme successfully manually unpacked but this is only one example how you can do it, of course. So the tutorial [videos + text tutorial] is very long and has a run-time of more than three hours and of course it will be necessary that you also read the text parts I made at the same time if possible but if you are already a advanced user then you will have it easier than a newbie. So I hope that you have enough patience to work through the whole tutorial. So the main attention I set on all things which happen after normal unpacking so the unpack process is the simplest part and all what comes after is the most interesting part and how to deal with all problems that happen. It's more or less like a live unpack session. I also wrote some small basic little helper scripts which you can also use for other targets to get valuable information if you need. Short summation: Unpacking Exception analysing VM analysing with UV plugin AntiDump's find & fixing & redirecting "after fix method" Testing on other OS My Special Thanks goes to Lostin who made this unpackme and others + OS's tests. (I want to send a thank you to Deathway again for creating this very handy and helpfully UV plugin). So this is all I have to say about the tutorial so far, just watch and read and then try it by yourself. Oh! and by the way I record ten videos and not only one. If something does not work or you have any problems with this tutorial, etc. then ask in the support topic only. Don't send me tons of PM's, OK! Thank you in advance. PS: Oh! and before someone has again something to complain because of my tutorial style [goes to quickly or is bad or whatever] then I just want to say, maybe you're right so normally I don't like to create and write tutorials. This is really not my thing so keep this in your mind.19 points -
Tuts 4 You UnpackMe Collection (2016)
 18 points
18 points- 5,467 downloads
Password: tuts4you .NET .NET Reactor 2.5.0.0.rar CliSecure 3.2.rar CliSecure 4.5.rar CodeVeil 1.2.rar DNGuard (Standard) 2.6.rar DNGuard HVM 2.6.2.0.rar dotNET Reactor 2.0.0.1.rar dotNET Reactor 2.1.5.3.rar dotNETZ 0.2.7.rar Maxtocode 3.2.rar MPress 0.71.rar MPress 0.75.rar MPress 0.77.rar MPress 2.12.rar NsPack 3.6.rar Phoenix Protector 1.7.0.1.rar Sixxpack 2.2.rar Skater .NET Obfuscator Light 2.6.rar Smart Assembly 1.3.rar Smart Assembly 2.0.rar Themida .NET 1.9.3.0.rar FoxPro KONxiSE 1.0.rar vfp&exeNc 6.20.rar PE32 x32 !EP (EXE Pack) 1.0.rar !EP (EXE Pack) 1.2.rar !EP (EXE Pack) 1.4.rar !EProt 0.01.rar 1337 Exe Crypter 1.rar 1337 Exe Crypter 2.rar 12311134.rar Aase 1.0.rar ABC Crypter.rar ACProtect 1.09g.rar ACProtect 1.32.rar ACProtect 1.41.rar ACProtect Pro 2.1.0.rar ACProtect Standard 2.0 2006.03.10.rar Advanced UPX Scrammbler 0.5.rar AffilliateEXE 1.0.rar Again Nativity Crypter.rar AHTeam EP Protector 0.3.rar AlexProt 1.0 Beta2.rar Alloy 4.3.21.2005.rar Alloy 4.10.9.2006.rar ANDpakk2 0.18.rar Anskya Polymorphic Packer 1.3.rar AnslymPacker.rar Anti007 2.5.rar AntiCrack Protector.rar AntiDote 1.4.rar AntiDote_1.2.rar antiOllyDBG.rar AR Crypt.rar AREA51 Cryptor 1.1.rar ARM Protector 0.1.rar ARM Protector 0.3.rar Armadillo 1.84.rar Armadillo 1.90.rar Armadillo 1.91c.rar Armadillo 2.00.rar Armadillo 2.52.rar Armadillo 3.70a.rar Armadillo 4.00.0053.rar Armadillo 4.10.rar Armadillo 4.20.rar Armadillo 4.30.rar Armadillo 4.30a.rar Armadillo 4.40.rar Armadillo 4.42.rar Armadillo 4.44.rar Armadillo 4.54 (Beta 1).rar Armadillo 4.66.rar Armadillo 6.0.0.rar Armadillo 6.2.4.624.rar Armadillo 6.40.rar Armadillo 6.60.0140.rar Armadillo 7.0 Beta 3.rar AsCrypt 0.1.rar ASDPack 2.0.rar ASPack 2.2.rar ASPack 2.12.rar ASPack 2.12_.rar ASProtect 1.2.rar ASProtect 1.23 RC1.rar ASProtect 1.33.rar ASProtect 1.35.rar ASProtect 1.40.rar ASProtect SKE 2.4 Build 09.11.rar ASProtect SKE 2.10.rar ASProtect SKE 2.11.rar ASProtect SKE 2.20.rar ASProtect SKE 2.30.rar Ass Crypter 1.0.rar AT4RE aSm Protecter 1.0.rar AT4RE Protector 1.0.rar AverCryptor 1.0.rar AverCryptor 1.02.rar AZProtect 0001.rar Backdoor PE Compress Protector 1.0.rar BamBam_0.04.rar Bastards Tools 1.1.rar Beria 0.07.rar Berio 1.0 Beta.rar Berio 1.02.rar BeRoEXEPacker 1.00.rar Biohazard Crypter.rar Bleeding Rose Crypter 1.0.rar BoxApp Packer 2.2.0.9.rar Break Into Pattern 0.1.rar C.I. Crypt 0.1.rar C.I. Crypt 0.2.rar CDS SS 1.0 Beta 1.rar Celsius Crypt 2.0.rar Celsius Crypt 2.1.rar CExe1.0b.rar ChinaProtect 0.3.rar CI Crypt 0.1.rar Cigicigi Crypter 1.0.rar CliSecure 4.5.rar CodeVeil 1.2.rar COOLcryptor 0.9.rar Crunch 5.0.0.rar CrypKey SDK 5.7.rar Crypt R.roads 1.0.rar Cryptable Seduction 1.0.rar Cryptic 2.1.rar CrypToCrack Pe Protector 0.9.2.rar CrypToCrack Pe Protector 0.9.3.rar CRyptOZ 3.rar CryptX 1.0.rar CSDSJKK Protector.rar CuBe Crypt0r.rar DalKrypt 1.0.rar DCrypt Private 0.9b.rar dePack.rar DeX-Crypt 2.0.rar DexCrypt 2.0.rar DirTy Cryptor.rar dotFakeSigner.rar DotFix NiceProtect 2.2.rar DotFix NiceProtect 2.3.rar DotFix NiceProtect 2.5.rar DotFix NiceProtect 2.9.rar DotFix NiceProtect 3.6.rar DragonArmour.rar Drony Application Protect 3.0.rar Eagle Protector.rar EmbedPE 1.13.rar EnCryptPE 2.2006.7.10.rar EnCryptPE 2.2007.4.11.rar Enigma 1.12.rar Enigma 1.55.rar Enigma 1.68.rar eS304.rar Escargot 0.1.rar Excalibur1.03.rar ExE Evil 1.0.rar Exe32Pack 1.42.rar EXECrypt 1.0.rar ExeCryptor 1.5.30.rar ExeCryptor 2.1.20.rar ExeCryptor 2.1.70.rar ExeCryptor 2.2.50.rar ExeCryptor 2.4.1.rar ExeCryptor Official Crackme.rar ExeFog 1.1.rar EXESafeguard 1.0.rar ExeSax 0.9.1.rar ExeShield 3.6.rar ExeShield 3.7.rar ExeShield Cryptor 1.3RC.rar ExeShield Deluxe 1.2.21.rar ExeShield Deluxe 1.3RC.rar ExeShield Ultra Edition 1.40.rar ExeShield Ultra Edition 1.41.rar EXESmasher 1.0.rar ExeStealth 2.75a.rar ExeStealth 2.76.rar eXPressor 1.2.0.rar eXPressor 1.3.0.1.rar eXPressor 1.5.0.1.rar eXPressor 1.6.0.1.rar EZIP 1.0.rar EZIP 1.1.rar Fakus Cryptor 1.4.rar Fast File Crypt 1.6.rar FastPack32 1.2.rar FatMike 0.1.rar fEaRz Crypter 1.0.rar fEaRz Packer 0.3.rar FileShield 1.0.rar FishPE 1.02.rar FishPE 1.16.rar FishPE 1.17.rar FishPE Packer 1.03.rar FishPE Packer 1.04.rar FishPE Shield 2.0.1.rar Flame Packer II.rar Flashback Protector 1.0.rar Free Joiner Small 0.15.rar Freex64 1.0.rar FSG 2.0.rar fornication_U 0.1.5.rar Fusion 4.0.00.rar G!X Protector 1.2.rar GhaZza CryPter 1.0.rar GHF Protector.rar Gie Protector 0.2.rar GKripto 1.0.rar Goats PE Mutilator 1.6.rar H4ck-y0u.org Crypter.rar HAC Crew-Crypter.rar HaLV Crypter.rar HaspSRM 3.4.rar Hexalock DVD Copy Protection System 2.3.rar Hide & Protect 1.016.rar HidePE.rar HidePX.rar Hmimys Packer 1.0.rar Hmimys Packer 1.2.rar Hmimys Packer 1.3.rar Hmimys PE-Pack.rar Hound Hack Crypter 1.0.4.rar Hyings PE-Armour CCG.rar ICrypt 1.0.rar ID Application Protector 1.2.rar iNF Cryptor.rar James Crypter 2.0.rar JDPack 1.01.rar JDPack 2.00.rar JDProtect 0.9.rar JDProtect 0.90b.rar JeyJey UPX Protector.rar Joker Protector 1.0.8.rar Joker Protector 1.1.3.rar K!Cryptor 0.11.rar KaOs PE-DLL eXecutable Undetecter.rar KGB Crypter 1.0.rar KiAms Cryptor 1.4.rar Kkrunchy 0.17.rar Kkrunchy 0.23.rar Kratos Crypter.rar Krypton 0.5.rar Kur0k.X2.to.rar LameCrypt 1.0.rar LCG 1.0.rar Lightning Crypter Private 1.0.rar Lightning Crypter ScanTime 1.0.rar Luck007 2.7.rar LuCypher 1.1.rar Mal Packer 1.2.rar MarCrypt 0.01.rar MaskPE 2.0.rar MEW 1.1.rar Mimoza 0.86.rar Minke 1.01.rar MKFPack.rar Molebox 2.2.4.rar Molebox 2.3.rar MoleBox 2.5.13.rar MoleBox Pro 2.6.0.2375.rar MoleBox Pro 2.6.1.2387.rar MoleBox Pro 2.6.4.2534.rar MoleBox Pro 2.6.5.2570.rar MoleBox Ultra 4.1900.rar MoleBox Ultra 4.1900_.rar Money Crypter 1.0.rar Morphine 1.9.rar Morphine 2.7b.rar Morphine 3.3.rar Morphine 3.5.rar Morphnah 0.2.rar Mortal Team Crypter.rar Mortal Team Crypter 2.rar MoruK creW Crypter Private.rar mPack 0.0.2.rar mPack 0.0.3.rar MPress 0.77.rar MPress 1.27.rar MPress 2.01.rar MPress 2.05.rar MPress 2.12.rar Mr Undectetable 1.0.rar MSLRH 0.32a.rar Muckis Protector.rar Muckis Protector II.rar My PE Packer 0.1.rar MZ0oPE 1.0.6b.rar N-Code 0.2.rar NakedPacker 1.0.rar NeoLite 2.0.rar Nidhogg 1.0.rar NME 1.1.rar NOmeR1.rar NoNamePacker.rar NoobyProtect 1.1.8.0.rar NoobyProtect 1.6.8.0.rar NoobyProtect 1.6.40.rar NoobyProtect SE Public 1.0.9.6.rar NoodleCrpyt 2.rar Nova Cipher 1.0.rar noX Crypt 1.1.rar nPack 1.1.250.2006.rar nPack 1.1.300.rar nPack 1.1.800.2008.rar NsPack 2.3.rar NsPack 2.4.rar NsPack 2.9.rar NsPack 3.0.rar NsPack 3.3.rar NsPack 3.4.rar NsPack 3.5.rar NsPack 3.6.rar NsPack 3.7.rar NsPack Scrambler.rar NTkrnl Protector 0.1.0.0.rar NTkrnl Protector 0.15.rar NtPacker 1.0.rar Obsidium 1.2.rar Obsidium 1.2.5.rar Obsidium 1.3.4.2.rar Obsidium 1.3.5.5.rar Obsidium 1.3.6.1.rar Obsidium 1.4.0.9.rar Obsidium 1.30.rar Open Source Code Crypter 1.0.rar Orien 2.11.rar OSC-Crypter.rar p0ke Scrambler 1.2.rar Pack 4.0.rar PackMan 0.0.0.1.rar PackMan 1.0.rar Pain Crew Protector 1.1.rar Pandora.rar Password Protect UPX 0.30.rar PC Shriner 0.71.rar PcGuard 4.06c.rar PcGuard 5.0.rar PE-Armour 0.765.rar PE Lock NT 2.04.rar PE Pack 1.0.rar Pe123 2006.4.4.rar PeBundle 3.20.rar PeCancer 1.0 (Demo).rar PeCancer 2007 07 11.rar PeCompact 1.30.rar PeCompact 1.50.rar PeCompact 1.84.rar PeCompact 2.55.rar PeCompact 2.57.rar PeCompact 2.64.rar PeCompact 2.68.rar PeCompact 2.70.rar PeCompact 2.78a.rar PeCompact 2.79.rar PeCompact 2.98.4.rar PEDiminisher 0.1.rar PELock 1.06.rar PEncrypt 4.0p.rar Pepsi 2.0.rar Perplex PE-Protector 1.01.rar PeSpin 1.0.rar PeSpin 1.1.rar PeSpin 1.3.rar PeSpin 1.3 (Private).rar PeSpin 1.32.rar PeSpin 1.304.rar Pestil 1.0.rar PeStubOEP 1.6.rar Petite 1.2.rar Petite 1.3.rar Petite 1.4.rar Petite 2.3.rar PeX 0.99.rar PFE CX 0.1.rar Phoenix Protector 1.4.0.1.rar PI Cryptor 3.0.rar PKLite32 1.1.rar PlutoCrypt.rar Pohernah 1.0.1.rar Pohernah 1.0.2.rar Pohernah 1.0.3.rar Poisen Ivy Crypter.rar Poke Crypter.rar Poly!Crypt 2.8.rar PolyBox 1.0.rar PolyCrypt PE 2.00.rar PolyCrypt PE 2.1.5.rar PolyEnE 0.01.rar Private EXE Protector 1.7.rar Private EXE Protector 1.8.rar Private EXE Protector 1.9.rar Private EXE Protector 1.95.rar Private Exe Protector 2.25.rar Private EXE Protector 2.30.rar Private EXE Protector 2.40.rar Private Exe Protector 2.71.rar Private Personal Packer 1.0.2.rar PrivateKrypt 1.0.rar Protect Shareware 1.1.rar Pub Crypter.rar Punisher 1.5.rar PussyCrypter 1.0.rar QrYPt0r.rar QuickPack NT 0.1.rar RCryptor 1.1.rar RCryptor 1.3.rar RCryptor 1.4.rar RCryptor 1.5 (Private).rar RCryptor 1.6c.rar RCryptor 1.6d.rar RCryptor 2.0.rar RDG Poly Pack 1.1.rar RDG Tejon Crypter 0.1.rar RDG Tejon Crypter 0.8.rar ReCrypt 0.15.rar ReCrypt 0.74.rar ReCrypt 0.80.rar ReWolf x86 Virtualizer.rar RLP 0.7.2.rar RLPack 1.0.rar RLPack 1.1 BasicEdition.rar RLPack 1.11 BasicEdition.rar RLPack 1.15 BasicEdition.rar RLPack 1.16.rar RLPack 1.17.rar RLPack 1.18.rar RLPack 1.20.1.rar RLPack 1.21.rar RoguePack 1.1.rar RoguePack 3.3.1.rar ROR Packer 0.3.rar RPolyCrypt 1.0b.rar RPolyCrypt 1.4.rar Russian Cryptor 1.0.rar SDProtector 1.12.rar SDProtector 1.16.rar Secure Shade 1.5.rar SEH Protector 1.0.5.rar SEH Protector 2.5.0.rar Sentinel Hardware Key 7.5.0.rar Sexe Crypter 1.1.rar Sh4DoW.rar Shergerd Exe Protector 4.87.rar Shrinkwrap 1.4.rar Sim Crypter.rar SimbiOZ.rar SimbiOZ 2.1.rar Simple Crypter 1.2.rar Simple Pack 1.0.rar Simple Pack 1.2.rar Simple Pack 1.11.rar Simple Pack 1.21.rar Simplicity.rar SkD Undetectabler 3.rar SkD Undetectabler Pro 2.0 (Special_Edition).rar SLVc0deProtector 0.61.rar Small Polymorphic Crypter 0.1.rar SmokeScreen Crypter 2.0.rar Smon v0.2b.rar Snoop Crypt 1.0.rar Soft Defender 1.12.rar softSENTRY 3.00.rar Software Compress LITE 1.4.rar Sopelka 1.5.rar SPEC b3.rar SPLayer 0.08.rar StarForce 3.xx.rar StarForce 4.7.rar StasFodidoCrypter 1.0.rar Ste@lth PE 1.01.rar Ste@lth PE 2.10.rar SuperCrypt 1.0.rar SuperPacker 1.2.rar SVK Protector 1.43.rar tElock 0.98.rar tElock 0.99.rar TGR Crypter 1.0.rar TGR Protector 1.0.rar The Best Cryptor.rar The Zone Crypter.rar Themida 1.1.1.0.rar Themida 1.2.3.0.rar Themida 1.3.0.0.rar Themida 1.5.0.0.rar Themida 1.8.2.0.rar Themida 1.9.1.0.rar Thinstall 2.521 A.rar Thinstall 2.521 B.rar Thinstall 2.628.rar Thinstall 2.736.rar Thunderbolt 0.02.rar TPPpack.rar Trojka Crypter 1.1.rar TsT Crypter 1.0.rar Tubby Crypt 1.1.0.rar Turkish Cyber Signature 1.0.rar Turkojan Crypter 1.0.rar UnderGround Crypter 1.0.rar Undetector 1.2.rar UnDo Crypter 1.0.rar unkOwn Crypter 1.0.rar unnamed Scrambler 1.1C.rar unnamed Scrambler 2.0.rar unnamed Scrambler 2.1.1.rar unnamed Scrambler 2.5.2.rar UnOpix 1.10.rar UnOpix Scrambler 1.10.rar uPack Mutanter 0.1.rar uPolyX 0.4.rar uPolyX 0.5.rar UProtector 2.1.rar UPX-Scrambler RC1.x.rar UPX 1.25.rar UPX 1.91.rar UPX 1.92.rar UPX 2.00.rar UPX 2.01.rar UPX 2.02.rar UPX 2.90.rar UPX 3.00.rar UPX 3.01.rar UPX 3.03.rar UPX 3.04.rar UPX Lock 1.0.rar UPX$hit 0.0.1.rar UPXMutanter.rar UPXScramb 2.2.rar USSR 0.31.rar VB-PE-Crypt 1.0.rar VB-PowerWrap 4.1.rar VB-PowerWrap 4.3.rar VBOWatch Protector 2.0.rar VBOWatch Protector 3.0.rar VCasm.rar VCrpyt 0.9b.rar Virogen Crypt 0.75.rar Visual Protect 3.4.5.rar VMProtect 1.1.rar VMProtect 1.2.rar VMProtect 1.8.rar VMProtect 1.21.rar VMProtect 1.22.rar VMProtect 1.24.rar VMProtect 1.52.rar VMProtect 1.53.rar VMProtect 1.70.4.rar VPacker 0.02.10.rar VProtector 1.0.rar VProtector 1.1.rar VProtector 1.2.rar VXPack 1.1.3.rar Werus Crypter 1.0.rar Whitell Crypt.rar Wind of Crypt 1.0.rar WingsCrypt 1.0.rar WinKrypt 1.0.rar WinLicense 1.1.1.0.rar WinLicense 1.4.0.2.rar WinLicense 1.8.9.0.rar WinLicense 2.0.1.0.rar WinLicense 2.0.6.5.rar WinLicense 2.0.8.0.rar WinUpack 0.30.rar WinUpack 0.32.rar WinUpack 0.35.rar WinUpack 0.38.rar WinUpack 0.39.rar WL-Crypt 1.0.rar WL-Group Crypter.rar WouThrs EXE Crypter 1.0.rar WWPack32 1.x.rar X-Crypter 1.2.rar X-Crypter 2.0.rar x86 Virtualizer.rar XComp 0.98.rar XcR 0.13.rar XXPack 0.1.rar Yoda Crypter 1.3.rar Yoda Protector 1.02b.rar Yoda Protector 1.03.2.rar Yoda Protector 1.0b.rar YZPack 1.1.rar YZPack 2.0b.rar ZeldaCrypt 1.0.rar ZipWorxSecureEXE 2.5.rar ZProtect 1.3.rar ZProtect 1.4.rar ZProtect 1.4.4.0.rar ZProtect 1.4.8.0.rar ZProtect 1.4.9.0.rar ZProtect Enterprise 1.3.1.rar PE64 x64 lARP64 Pro 1.0.3.rar lARP64 Pro 1.0.3_old.rar lARP64 Pro 1.0.3_update.rar MPress 1.07 x64.rar MPress 2.12 x64.rar NsPack 3.6 x64.rar PeSpin Pre-Alpha x64.rar PeSpin x64 0.3a.rar PeSpin x64 1.1.rar18 points -
Enigma Protector 1.90 - 3.xx Alternativ Unpacker v1.1

- 8,676 downloads
Today I release an unpacker script for Enigma Protector. Maybe you know that I created another unpacker script for Enigma in the past which no-longer works for protected Enigma files greater than 3.70+ and this is the reason why I wrote a new script, Enigma Alternativ Unpacker 1.0. So what is new in this script? This script will unpack your Enigma protected files and dump the used outer virtual machine. This means you do not need to use the DV / Enigma plugin which is used in my other script. Of course the virtual machine will be still virtualized but your unpacked files will work. It is not the best solution but for the moment it is a good "alternativ" and a working solution. Features of the script: ( 1.) Unpacking of ENIGMA 1.90 - 3.130+ ( 2.) RegSheme Bypass & HWID Changer ( 3.) Enigma CheckUp Killer ( 4.) VirtualMemory Dumper 1.90 - 3.x+ & SC Fixer M1 ( 5.) UIF Tool Necessary Sometimes! ( 6.) Enigma Intern Export & VM Scan + Log ( 7.) Improved Import Emulation Fixer ( 8.) Supports Exe & Dll Files [dll at EP!] This new script again covers almost all the protection features of Enigma Protector like my other script but it has been improved and I have added some extra things that you will see when you get to use it. I have created four video tutorials for you where you can see what you have to do in some of the different situations you may experience. Be sure that you "watch the videos" before you use the script to prevent some unnecessary questions where you can already find the answers if you watch them and then read my added text files. I also made an UnpackMe set with six different protected files (watch videos how to unpack all of them). If something does not work for you or if you get any trouble or have any questions then just post a reply on the topic (linked above) to get an answer.11 points -
ARTeam Tutorials
 10 points
10 points- 1,888 downloads
A collection of legacy tutorials from ARTeam covering multiple aspects; unpacking, cracking, inline patching, dongles, DRM, keygenning, debugging, serial fishing, loaders, etc. MD5: ARTeam Tutorials Collection.rar : ca10cf1c85b12f6f9d0b2998c2356e7f10 points -
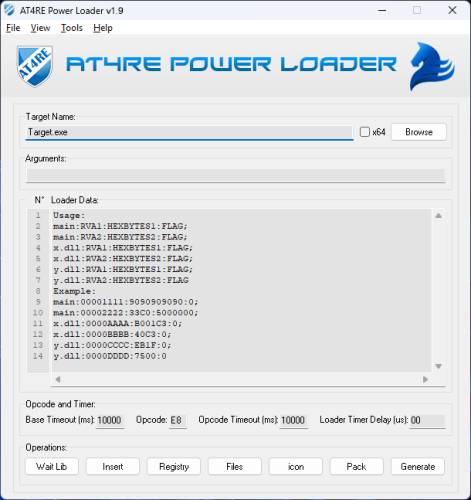
AT4RE Power Loader
 9 points
9 points- 774 downloads
- Version v1.9
============================ AT4RE Power Loader v0.1 (Release Date: 26/03/2025) ============================ [+] Console interface [+] Loader Coded in C++ with CRT (big Size: 85 KB when compressed about 190 KB uncompressed). [+] Supports patching single or multiple Relative Virtual Addresses (RVAs). Root Folder Contents: [+] ATPL.EXE (AT4RE Power Loader) [+] Version History.txt ============================ AT4RE Power Loader v0.2 (Release Date: 16/04/2025) ============================ The most powerful loader against strong and hard protectors. It also works with medium-level protectors, packers, compressors, and even unprotected executable files. Main Features: [+] GUI Coded in Borland Delphi 7 [+] From the GUI, you can browse to select the target file (maximum filename length is 255 characters). [+] You can also copy and paste the file name into the input field. [+] Choose between x32 and x64 loader versions. [+] Loader data can be entered only in the format shown in filed or in the screenshot. [+] Set a base timeout in milliseconds (Minimum: 00, Maximum: 9999 — i.e., 9.99 seconds). [+] Set 1-byte opcodes in the Opcode field using HEX characters (Opcode is the Original First Byte of RVA1). [+] Configure Opcode Timeout in milliseconds (Minimum: 00, Maximum: 9999 — i.e., 9.99 seconds). [+] Set the Loader Timer Delay in microseconds (Min: 00, Max: 9,999,999 — i.e., 9.99 seconds). [+] Configure the loader to start as Administrator. [+] Directly pack the loader with UPX. [+] Generate Loader.exe [+] Save or open projects for future use from File menu. [+] Set the GUI to "most on top" from the View menu. [+] Access the official website, report bugs, and find more information via about in the Help menu. Loader Details: [+] Coded in C++ using the Windows Pure API. [+] Loader size is 10 KB uncompressed, and 5 KB when compressed. [+] Supports Windows 7, 8, 10, and 11 (both x32 and x64). Features include: [+] Anti-ASLR [+] Anti-Anti-Debug [+] Anti-CRC Check [+] Automatically detects the base address. [+] Detects when the protector unpacks code into memory. [+] Can apply temporary patches after a specified delay in microseconds (Patch and restor original bytes). [+] Can apply permanent patches only with 00 Flag [+] Supports patching single or multiple Relative Virtual Addresses (RVAs). [+] Capable of patching up to 2048 bytes. [+] Can run as Administrator or Normal user mode. Root Folder Contents: [+] Project folder (Save or open projects for future use) [+] UPX folder (includes upx32.exe and upx64.exe) [+] ATPL.EXE (AT4RE Power Loader) [+] Version History.txt ============================ AT4RE Power Loader v0.3 (Release Date: 10/05/2025) ============================ The most powerful loader against strong and hard protectors. It also works with medium-level protectors, packers, compressors, and even unprotected executable files. Main Features: [+] Added Support Patching DLLs (Only DLLs Loaded by Target.exe). [+] Added Drag Drop Feature: For .EXE, .REG, .ICO Files. [+] Added Insert Loader Data feature (For Respect the Correct Format). [+] Added Registry Keys Manager (Max size: 1 KB / 1024 characters). [+] Added Delete Files feature (Max size: 1 KB / 1024 characters). [+] Added Icon Changer. [+] Added New Project option from File menu (Clears all fields). [+] Added Commands Shortcut Ctrl+N, Ctrl+O, Ctrl+S in File menu. [+] Added Contact Us section from Help menu. [+] Updated About from Help menu from box to a form. [+] Updated display fonts for Loader Data, Registry, and Files. [-] Removed "My Target run as admin". Loader Details: [+] Size is now 17 KB uncompressed, 7 KB when compressed. [+] Loader now Support Patching DLLs (Only DLLs Loaded by Target.exe). [+] Loader can now add or delete registry keys. [+] Loader can delete files. [+] Automatically requests Run as Administrator when needed (e.g.,Target need administrator privilege, modifying registry or deleting files from protected folders). [+] Icon support added. Root Folder Contents: [+] Icons folder (includes 5 icons). [+] Lib folder (includes bass.dll). [+] Project folder (Save or open projects for future use). [+] ResH folder (includes ResHacker.exe). [+] UPX folder (includes upx32.exe and upx64.exe). [+] ATPL.EXE (AT4RE Power Loader). [+] Version History.txt ============================ AT4RE Power Loader v0.4 (Release Date: 16/05/2025) ============================ The most powerful loader against strong and hard protectors. It also works with medium-level protectors, packers, compressors, and even unprotected executable files. Main Features: [+] Added Import menu. [+] Added Support .1337 patch files exported by x64dbg. [+] Set Opcode automatically when Load .1337 file. [+] Added OpenDialog when Double Click on: - Target Name field. - Loader Data field. - Registry field. - Custom icon field. Loader Details: [+] Fixed bug with registry feature. [+] Default icon changed. [+] Compressed Loader with Default icon 8 KB. Root Folder Contents: [+] Icons folder (includes 5 icons). [+] Lib folder (includes bass.dll). [+] Project folder (Save or open projects for future use). [+] ResH folder (includes ResHacker.exe). [+] UPX folder (includes upx32.exe and upx64.exe). [+] ATPL.EXE (AT4RE Power Loader). [+] Version History.txt9 points -
OllyDbg 1.1.0 Special for Guru LCF-AT's VMProtect API Turbo Tracer 1.1 Script

- 14,130 downloads
Many of you may be amazed at Guru LCF-AT's script "VMProtect API Turbo Tracer 1.2". But for most of the newbies, just like me, you may have a lot of problems in getting the script work properly in your own Ollydbg. LCF-AT already uploaded a lot of Ollydbg setting information togehter with the script to help us fix those Ollydbg problems, but there are too many details. Yes, I suffered a lot at the inital stage when I was trying to use "VMProtect API Turbo Tracer 1.1" by my chinese version "Terminator Ollydbg 1.1.0". Under LCF-AT's kind help, I created this basic version Ollydbg 1.1.0, which is specially for running "VMProtect API Turbo Tracer 1.1". And it works smoothly in my laptop, with Windows XP Professional SP3. If you like, get it and give it a try. Enjoy Cracking!!9 points -
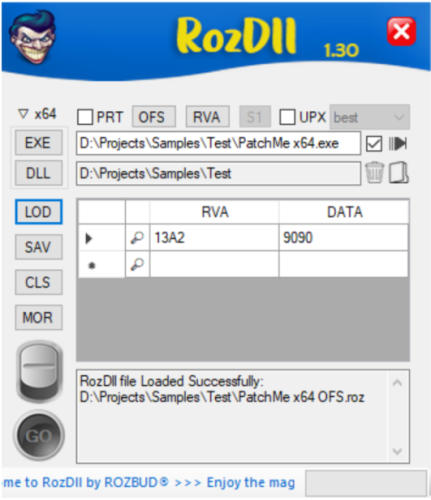
RozDll (Advanced Dynamic Proxy DLL Generator)

- 577 downloads
- Version 5.1
Provision: Create a tiny Proxy DLLs for Personal researches. RozDll Vs Fixit: Fixit is a “Static Load Generator”. Handles Pre-Generated List of DLL's that may be work with your Executable or not (same as ByMax). RozDll is a “Dynamic Load Generator”, runs your Executable in Memory, gets a list of Proxy DLL's which your Executable uses in Memory. RozDll Main Features: Generate Fast, Portable & Small Size Proxy/Hijacked DLL. Integrated with x64dbg. You can load the Patched Data directly from x64dbg exported file (*.1337). Dynamic Loading. Function Selection. Deferent Method of patch Options. Encryption: DLL Function Names are Encrypted. This will make it difficult for Anti-Virus to trace generated DLL. Startup Message: You can personalize your work by writing your name and short info/about. This message will appear only at the first run of target executable. Data Extraction: Upload Registry and other filetypes into target PC. Data Verification: Clicking on the 'Magnifier symbol' is mandatory & it will ensure that you entered the correct data. Created on Windows 10 & Visual Studio 2022. It should work on Windows 10 & Windows 11, but not guaranteed to work in Virtual Windows. Tutorial: RozDll_Advanced.mp4 RozDll_Final_Tutorial_(v1.30).mp49 points -
REPT KeyGen Maker
 9 points
9 points- 5,772 downloads
- Version 1.7
REPT KeyGen Maker is an utility to make keygens easily without having a programming knowledges. Please report any bug/improve to make it better This is currently done in .NET so will need .NET Framework 3.5 or higher. Thanks for download it!9 points -
OllyDBG - AIO
8 points
- 39,378 downloads
- Version v1.1 & v2.0 & Sh
OllyDbg with Plugin + OllyDBG v1.1 + OllyDBG v2.0.1 + OllyDBG Shadow GUI with Vic Plug-In Enjoy !8 points -
EASY SNIFFER CREATOR
 8 points
8 points- 1,774 downloads
- Version v 1.0
hey guys i create a program for serial sniff by vb6 esc features : check crc(automatic) unicode string small size background music bypass packers and ..... sorry for my english (im persian) enjoy it8 points -
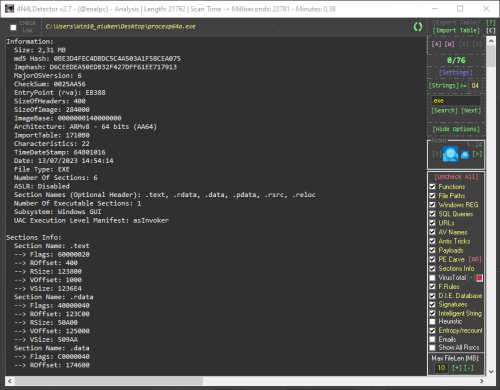
4n4lDetector
 7 points
7 points- 293 downloads
- Version 3.4.0
This is a scan tool for Microsoft Windows executables, libraries, drivers and mdumps. Its main objective is to collect the necessary information to facilitate the identification of malicious code within the analyzed files. This tool analyzes, among other things, the PE header and its structure, the content of the sections, the different types of strings, among many other things. It also incorporates a multitude of its own ideas to recognize anomalies in the construction of files and the detection of mechanisms used by current malware. Using the tool is simple, just configure the options in the drop-down panel on the right and drag the samples into 4n4lDetector. Full support: - 32 bits (8086, x86, ARMv7) - 64 bits (AMD64, x86-64, x64, ARMv8) TI and ET Extraction: Alpha AXP, ARM, ARM Thumb-2 (32-bit Thumb), ARM64, EFI Byte Code, EFI Byte Code (EBC), Hitachi SH3, Hitachi SH3, Hitachi SH4, Hitachi SH5, Intel i860, Intel Itanium (IA-64), M32R, MIPS16, MIPS16 with FPU, MIPS R3000, MIPS R4000, MIPS with FPU, MIPS little-endian, MIPS little-endian WCE v2, x64, x86, x86-64. Buttons code: - Buttons colored green are action buttons that open files and folders or are used to interact with the tool's utilities. - The buttons colored in red perform reconfigurations, deletion of data or reset of functional files. - Purple buttons announce the activation of online interactions. - The pink buttons are shortcut buttons that the tool uses as tabs to navigate between different types of utilities. Shortcuts: - [A] Main analysis tab - [W] Analysis tab in modifiable HTML format for report (WebView) - [S] Viewer of strings extracted from the parsed file - [V] Module with the Virustotal report using its API Detections: - PE Information - Unusual Entry Point Position or Code (Algorithms, Anomalous Instructions... ) - Packers - Compilations - Binders/Joiners/Crypters - Architectures - Possible malicious functions - Registry Keys - Files Access - Juicy Words - Anti-VM/Sandbox/Debug - URLs Extractor - Payloads - AV Services - Duplicate Sections - IP/Domains List - Config RAT (Only In Memory Dumps) - Call API By Name - Unusual Chars In Description File (Polymorphic Patterns) - Rich Signature Analyzer - CheckSum Integrity Problem - PE Integrity Check - SQL Queries - Emails - Malicious resources - PE Carve - Exploits - File Rules for Entry Points and more... 😃 Console Options (Analysis to file): - 4n4lDetector.exe Path\App.exe -GUI (Start the graphical interface parsing a file from the console) - 4n4lDetector.exe Path\App.exe -GREMOVE (Remove binary after scan) - 4n4lDetector.exe Path\App.exe -TXT (Parse a file from the console and the output is written to a TXT file) - 4n4lDetector.exe Path\App.exe -HTML (Parse a file from the console and the output is written to HTML file)7 points -
CrackZ's Reverse Engineering Page (1997-2012)

- 977 downloads
Welcome! on this fine day, you have reached CrackZ's Reverse Engineering Page, on the web for 14+ years, despite many censorship attempts. Amongst these pages you will find what is now a very rare commodity on today's commercialised web; a site where you can acquire all the skills you need to become a competent reverse engineer. This site provides information for analysts and protectionists alike, focusing mainly on the protection schemes of Window's software whilst debunking some of the mystery surrounding the sublime art of 'copy protection'. Everything here is yours for free, I hope you will enjoy taking some time to look around. In the last 15 years commercial profit motives have transformed the nature of web information and searching forever, a bitter irony indeed that in our rush to embrace a world of 'free information', more and more is now hidden, treasure troves of free knowledge have been shunned in the stampede for 'e-commerce' gold, snake oil products to this day provide a false sense of security to software authors. This site is fiercely against these trends, but is also realistic in that it will make not one iota of difference. Upon my pages you will find many teachings that should enable you (with a little work) to reverse engineer most of the software you'll ever encounter or need (probably saving you a considerable amount of money). You will find no dubious advertising banners, irritating pop ups, endless loops of smut site referrals or targeted ads, (they couldn't pay me enough to promote their useless products anyway), much of the material here is at a level where little more than a 'willingness to learn' is assumed, of course if you delve a little deeper you will (I hope) find much more. MD5: CrackZ's Reverse Engineering Page (1997-2012).rar : 834d28a4e6d00abb6b6d007f6b4fd4ed7 points -
Ubbelol .NET Reversing Series
 7 points
7 points- 4,167 downloads
Various collection of reversing tutorials in video covering various aspects of .NET from Ubbelol. Name Size Type Modified Attr MD5 Checksum .NET Cracking 101 #1 - Absolute basics.mkv 21.5 MB Matroska 5/10/2017 5:12 AM -a----- 4c70dc7c9f6b47f39a4cde2c2e172ef3 .NET Cracking 101 #2 - WinDbg basics.mkv 55.8 MB Matroska 29/06/2014 6:55 PM -a----- 56b4f7138fe1dbbdac358d6d8ba6fe5b .NET Cracking 101 #3 - Additional techniques.mkv 26 MB Matroska 9/10/2017 2:20 PM -a----- aefe75ee91f2c2df13522e2084797e27 .NET Cracking 101 #4 - ChewBox crackme.mkv 25.4 MB Matroska 10/10/2017 12:51 AM -a----- 4eee0cae85fe1a85257adf09bd432eef .NET Cracking 101 #5 - 0xDEADDEAD Crackme.mkv 42.5 MB Matroska 29/09/2017 3:32 PM -a----- 665c6e1bfaeb0e531c38b033deaf843a .NET Cracking 101 #6 - WinDbg_.NET Seal 2.mkv 31 MB Matroska 7/10/2017 12:02 AM -a----- 0bd46985e743fe5ab1f72ffa30c7d5dc .NET Cracking 101 #7 - AutoJitPatcher by 0xDEADDEAD.mkv 22.6 MB Matroska 10/10/2017 3:24 PM -a----- 96f125c6966155826b44900ae0c10925 .NET Deobfuscation 101 #1 - Symbol renaming.mkv 52.8 MB Matroska 10/10/2017 7:19 AM -a----- d0485addca7d551af4c423b680574570 .NET Deobfuscation 101 #2 - Phoenix Protector.mkv 48.3 MB Matroska 20/10/2017 11:35 PM -a----- 0a557679daf3444daf86099b4516782a Confuser 1.9 Anti-tamper tool.mkv 12.4 MB Matroska 11/10/2017 2:39 PM -a----- 0990b4977988ac8ff99aaf7313e4364e Confuser 1.9 Deobfuscator WIP - YouTube.mkv 10 MB Matroska 30/09/2017 10:11 AM -a----- 761e56dc774e70417a0cd8a46b5d270e uNet example application.mp4 85.3 MB MP4 16/02/2013 3:21 AM -a----- b9cb5dc6717def0802c7a27affc6b02d7 points -
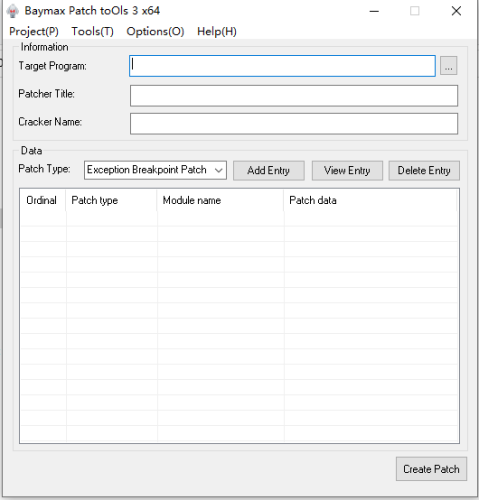
Baymax Patch toOls
 6 points
6 points- 1,794 downloads
- Version 3.1.0
Baymax Patch Tools v3.1.0 Tool description: Baymax Patch Tools is a hijacking patch making tool that releases a hijacking DLL for the target process to load the function module PYG. Two patching functions are supported.search and replace patch supports feature code search and replace memory data, exception breakpoint patch supports simulating the exception breakpoint function of debugger and modifying register, memory and other data after setting and triggering breakpoint to achieve the purpose of modifying program execution flow and so on. The tool is protected, antivirus may misreport the tool and patch files! Due to the use of the shell SDK, all components of the tool (including the generated patches) do not contain networking capabilities! The generated patches will not modify any files on the system when running (except for overwriting patch files). The generated patches will not modify any files on the system when running (except for overwriting patch files). The tool itself has a verification mechanism and will load only after the module is successfully verified at startup, but for security reasons, please be sure to download and use it from the official site. Function introduction: . support hijacking crack, not modify the file itself . support for patching processes with dynamic base addresses (ASLR) . support patching multiple DLL modules of the target process . support patching different EXEs of the same patch . support patching the memory data of a process at a specified address . support for patching processes using feature code matching . support setting API HOOK decoding for shelled programs before patching data . support patching data after setting hardware breakpoint interrupt for the process . support setting exception breakpoints to modify the memory pointed to by registers or registers after interrupting the process . support setting conditional breakpoints for processes to determine whether to execute Patch according to the number of interrupts, . . . . register or memory values . support setting different conditional breakpoints for the same address to perform Patch on the interrupts that meet the conditions . support extracting global variables from assembly instructions to store and modify them . support for storing data and using stored data during process execution . support patching the memory pointed to by the memory marker after interrupt . support basic operations on data after interrupt . support for reading patch data from ini file . support to create memory keymaker . support for creating debug patches to troubleshoot patch problems by yourself Update: 2023.01.18 x86 v3.1.0 1. Support multi-language function 2. adjusted and optimized the UI, text descriptions, etc. to improve the interactive experience Download: https://sourceforge.net/projects/baymax-patch-tools/6 points -
PinMe!
 6 points
6 points- 4,712 downloads
- Version 2022.09.28
PinMe! allows setting individual windows to TopMost (window always on top) with the following additional features; Setting windows to TopMost / NoTopMost Changing window transparency levels Window captures and region captures Desktop captures (foreground and background) Basic window statistics Window information; dimensions, sizes, styles, etc. Installation As of version 0.8.9 PinMe! runs on Windows 10 (Build 14393) and later, including Windows 11. Extract PinMe! from the archive and copy to a directory from where it can be run. If you want to have PinMe! run at each startup click on the "Run at Start-Up" option in the menu. A copy of PinMe! will be saved to the Windows "Startup" folder. TopMost / NoTopMost A list of all open and visible windows are shown in Z-Order from the click of the tray icon. Selecting a window positions that window to TopMost (always on top/pinned) and now the highest in Z-Order. If you select a window that has already been given TopMost it will set it to NoTopMost (normal). When more than one window is TopMost, the TopMost windows will take hierarchy in the order which you selected them. The first TopMost window will go to the bottom and recent to the top. TopMost windows will show up with a locked icon next to them in the menu. Normal windows will have their default window or system icon. If a window you want to set to TopMost or NoTopMost is not shown in the menu list of windows you can use customised shortcut keys, found in Preferences menu, whilst the window is active. Window Monitor As of version 0.9.3 PinMe! contains a frequently requested feature to "Monitor" certain windows and automagically set them to TopMost. When a window is being monitored PinMe! will remember the window(s) and, for example, after a restart set those windows to TopMost again. One of the caveats with this feature is if you were to monitor a Notepad window all subsequent opened Notepad windows will be set with TopMost. Feedback on this feature is warmly welcome. Window Transparency There are two ways to change the transparency of a window. The first it to find the window in the menu list and from the, "Window Transparency", submenu set the desired level of transparency between 10% to 100% viewable. If the window you want to set the transparency level of is not in the window menu list use the second method. From "Tools Menu..." menu select, "Enable Window Transparency". Once the setting has been activated you should see the same menu option now listed as, "Disable Window Transparency". Move the mouse cursor over the window you would like to change the transparency level of and scroll the mouse wheel until the transparency is at the desired level. Moving the mouse to other windows and scrolling the mouse wheel will change the transparency level of those windows until you go back to the tools menu to disable the feature. Whilst this option is activated mouse scroll wheel messages are not passed to the window until this option is disabled, scrolling through a page in a browser or document for example will not be possible. Capturing Windows You can capture the contents of a window in each windows submenu. PinMe! will try to capture the window image even if it is located behind other windows. If it is unable to do so PinMe! will attempt to bring that window to the front before capturing. Images can be saved in either .PNG, .JPG and .BMP., the image is also copied to the clipboard if you have the option enabled in Preferences. Capturing Screens & Desktops You can capture whole screens, desktop foreground and background. By going to, "Tools Menu...", you will find a submenu titled, "Capture Display Devices...". The submenu will contain a list of all the display devices currently connected and active including two options titled, "Capture Desktop Background", and, "Capture Desktop Foreground". To capture a screenshot simply select the appropriate display device and a save dialogue will appear to allow you to save the captured image to a folder. The following options capture the entire desktop across all monitors/displays: Capture Desktop Background, captures all of the desktop background across all display devices without any of the windows on top. Capture Desktop Foreground, captures all windows on top of the desktop across all display devices. Images can be saved in either .PNG, .JPG and .BMP., the image is also copied to the clipboard if you have the option enabled in Preferences. Region Captures Region capture can be activated by selecting, "Tools Menu...", then, "Enable Region Capture". Once you are in region capture the display will turn a slightly different colour and the mouse cursor will change to a cross hair with a square magnified window next to it. There are two methods for selecting the capture points. The first is to click and hold down the mouse pointer at the start position and drag the mouse pointer to draw a rectangle over the area of screen you would like to capture. You will notice a coloured rectangular box will be created, this is the region that will be captured. The second method is to left mouse click at the first capture point then left mouse click at the second capture point. You will notice the cross hair will stay active at the first location, this helps you correctly size the corners of the rectangle you wish to capture. To help you capture the correct region a magnify window is available. Inside the magnify window information will display the x and y coordinates of the cross hair position. A colour picker in the top right hand corner is displayed. The top left hand side shows the zoom factor which, you can change by scrolling the mouse wheel to zoom in and out of the image. After selecting a capture region the save dialogue automatically appears. Images can be saved in either .PNG, .JPG and .BMP., the image is also copied to the clipboard if you have the option enabled in Preferences. Exiting from region capture can be done by pressing the right mouse button. Depressing the wheel mouse button at any time during a capture will cause the mouse to move at slow speed. This may help in correctly aligning the capture cross hairs. Pressing the "SHIFT" key after the first cross hair has been set will delete it. Power Management There are three settings in the power management menu, these are to prevent the monitor or system from sleeping; 1) Prevent Display Sleeping 2) Prevent System Sleeping 3) Enable Away Mode Window List Window List displays all the windows on the current desktop including child windows in tree like hierarchy. There are options to filter for certain types of windows; Top-Level, Immersive, Store Apps, Children, Threads. Each entry is listed using its window handle and classname. Double clicking on a window allows you to open the Window Information window to view its details. Window Information Provides information on the window details including dimensions and certain capabilities. For Store Apps there is a separate tab detailing basic package information. There is a menu option here that allows you to point at a window using the mouse cursor to view its details. Window Controls Under each windows menu there are options to send messages to the window to; Close Gracefully, Close Forcibly, Restore, Zero, Maximise, Minimise. Shortcut Keys In the Preferences menu you will find two options for customising shortcut keys to start region capture and set an active window between TopMost and NoTopMost. To configure this click in one of the shortcut fields and then select the key combinations you would like to use. If the key combination was successful the shortcut description will be set. An error message will prompt you if PinMe! was unable to do this, likely because the key combination has already been registered by another application. Run At Startup You will only see this menu option if PinMe! is not already running from the Windows startup folder. When selected PinMe! will be copied to: C:\Users\Username\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup To update either; manually copy a new version to the startup folder or, whilst the new version of PinMe! is running (from another folder) select this option to overwrite the existing file. Run As Administrator Introduced in Windows Vista and used with subsequent editions, the Windows OS comes with a security feature called User Account Control - or UAC for short. UAC prevents programs and applications running with elevated (Administrator) privileges to help protect the operating system from being compromised by malicious software. By default PinMe! does not request elevated privileges. Because of this PinMe! may not by able to send messages to communicate a change of window state to a program that is running with higher privileges than PinMe!. This is due to another security technology called User Interface Privilege Isolation (UIPI). If you find that PinMe! is not changing the state of a particular window you can request PinMe! to run in Administrator mode by going to, "Tools Menu...", menu and selecting, "Run As Administrator", which will let PinMe! run with high integrity. Once activated Windows will prompt you with a User Account Control dialogue asking if you want to allow PinMe! to make changes to the computer. Click yes if you do. Once PinMe! is running with high integrity in Administrator mode PinMe! will be able to send messages and communicate with those windows. Preferences Here is a quick overview of other available options, not mentioned above, in the Preferences menu that allow you to enable or disable features: Sounds sound prompts and warnings. Clipboard saving of captures to the clipboard. Save Dialogue save dialogue prompt after captures. Repeat Capture continue to the next region capture after saving. Magnify Window enable or disable the magnify window. Language Files Upon startup PinMe! will try to determine the users interface language then search for that regions language file in the "Language" subfolder where PinMe! executable is located. All language files begin with, "lang_", suffixed by a three letter ISO language name for the region. E.g. for a user in Thailand using Thai language PinMe! will search for, "lang_tha.txt". If a language file is unable to be located PinMe! defaults to it's built in English language. PinMe! conforms to ISO 639-2 three-letter code for the language file suffix name. If you wish to create a language file for your region you can find your language prefix listed at Wikipedia: https://en.wikipedia.org/wiki/List_of_ISO_639-2_codes The language file must be saved in UTF-8. If for some reason your language is displayed incorrectly within PinMe! please try saving the file as UTF-8 with BOM (byte order mark).6 points -
Strong.Name.Helper.v1.7-whoknows-pass-bs.7z

- 3,257 downloads
- Version 1.7
Bundle of .NET tools! The development ended @ 2012 with v1.7. Main reason is to defeat strong name validation, on the other hand third party tools merged! ACorns.Hawkeye Is the only .Net tool that allows you to view, edit, analyze and invoke (almost) any object from a .Net application. Whenever you try to debug, test, change or understand an application, Hawkeye can help. CFF Explorer-NTCore Designed to make PE editing as easy as possible, but without losing sight on the portable executable's internal structure. HwndSpy-dp0 Is an invaluable tool for developers doing maintenance on GUI applications, where they first need to understand the windows hierarchy and how the windows are structured. HxD-Mael Horz Is a carefully designed and fast hex editor which, additionally to raw disk editing and modifying of main memory (RAM), handles files of any size. Mono.Cecil-Evain Is a library to generate and inspect programs and libraries in the ECMA CIL format. Procmon-SysInternals Is an advanced monitoring tool for Windows that shows real-time file system, Registry and process/thread activity. Resource2+4-fish Is a utility to easily refresh embedded resources in a .NET assembly. ResX Schema(*.resX), Embedded Resource(*.resources), Import/Export/View/Edit/Translate embedded resources, Text/Icon/Bitmap/Cursor/String/ImageListStreamer/PinnedBufferMemoryStream (v4)... SysTracer-blueproject Is a system utility tool that can scan and analyze your computer to find changed (added, modified or deleted) data into registry and files. de4dot-0xd4d Is an open source .NET deobfuscator and unpacker written in C#. Assembly_Resigner-CodeCracker HeaderFixer-CodeCracker NR_Bad_Net_Opcode_Remover-CodeCracker StrongName_Killer-CodeCracker Password to extract is bs6 points -
Old School Military for Uppp
 6 points
6 points- 253 downloads
- Version 1.0.1
Hello friends . new uppp interface. do you like it ? try! Respects by SKARZ6 points -
Tuts 4 You - Collection 2011
 5 points
5 points- 3,972 downloads
This is a complete archive (site rip) of all files on Tuts 4 You as of July 2011 except for the malware samples - you will need to download these directly from Tuts 4 You. I have created the torrent as directories and files rather than one archive which gives you the option to download files individually or in categories. The entire collection is 3.69 GB of which some sections may be of little interest to some but you have the option of downloading what you want. This collection will be updated annually so please check at the following link for the official and up-to-date torrent file. Base 32 Hash-ID magnet:?xt=urn:btih:slpgvubkpp4dyhxbaxpmogludkgmw7wi Base 16 Hash-ID magnet:?xt=urn:btih:92DE6AD02A7BF83C1EE105DEC719741A8CCB7EC8 Please remember to seed the torrent and help share the knowledge within the reversing community. I hope this satisfies the leechers, thank you! File/ Directory Listing Tuts 4 You - Collection 2011.md55 points -
Crackmes.de (2011 - 2015)
 5 points
5 points- 2,032 downloads
Crackmes.de, a site for testing reversing skills. Crackmes range from "Very Easy" to "Very Hard" for many operating systems. Archive contains a 2011 release from Malware Ninja... Please find the following linked zip that contains almost 1000 crackmes for all levels. Please enjoy and mirror/spread.5 points -
Joker Italy Manual Unpacking Tutorials

- 809 downloads
A video collection of unpacking tutorials (including unpackme files) by Joker Italy. MD5: Joker Italy Manual Unpacking Tutorials.rar : a2ffc7ec9a0b2e8356ee6c7e0dd247f15 points -
Strong Name Helper
 5 points
5 points- 1,445 downloads
- Version 2.2
Bundle of .NET tools! Main reason is to defeat strong name validation, on the other hand third party tools merged! ACorns.Hawkeye Is the only .Net tool that allows you to view, edit, analyze and invoke (almost) any object from a .Net application. Whenever you try to debug, test, change or understand an application, Hawkeye can help. CFF Explorer-NTCore Designed to make PE editing as easy as possible, but without losing sight on the portable executable's internal structure. HwndSpy-dp0 Is an invaluable tool for developers doing maintenance on GUI applications, where they first need to understand the windows hierarchy and how the windows are structured. HxD-Mael Horz Is a carefully designed and fast hex editor which, additionally to raw disk editing and modifying of main memory (RAM), handles files of any size. Mono.Cecil-Evain Is a library to generate and inspect programs and libraries in the ECMA CIL format. Procmon-SysInternals Is an advanced monitoring tool for Windows that shows real-time file system, Registry and process/thread activity. Resource2+4-fish Is a utility to easily refresh embedded resources in a .NET assembly. ResX Schema(*.resX), Embedded Resource(*.resources), Import/Export/View/Edit/Translate embedded resources, Text/Icon/Bitmap/Cursor/String/ImageListStreamer/PinnedBufferMemoryStream (v4)... SysTracer-blueproject Is a system utility tool that can scan and analyze your computer to find changed (added, modified or deleted) data into registry and files. de4dot-0xd4d Is an open source .NET deobfuscator and unpacker written in C#. Assembly_Resigner-CodeCracker StrongName_Killer-CodeCracker5 points -
Import Reconstructor (ImpREC)
 5 points
5 points- 2,884 downloads
- Version 1.7e
This tool is designed to rebuild imports for protected/packed Win32 executables. It reconstructs a new Image Import Descriptor (IID), Import Array Table (IAT) and all ASCII module and function names. It can also inject into your output executable, a loader which is able to fill the IAT with real pointers to API or a ripped code from the protector/packer (very useful against emulated API in a thunk). Sorry but this tool is not designed for newbies, you should be familiar a bit with manual unpacking first (some tutorials are easy to find on internet).5 points -
cct15k
 5 points
5 points- 111 downloads
- Version 1.0.0
hotkeys: m: (play/stop music) f1: (switch fullscreen/windows) f3: (nfo reader) elite: (hidden part) esc: (quit)5 points -
UndeadFactory(2)dUP2 Skin
 5 points
5 points- 419 downloads
- Version 1.0.0
hi guys, new UNDF. Skin version2 for dUP2 . Long Life Cracking GFX Resource based on World Of Crack D2's Skin Source .psd5 points -
HexRaysCodeXplorer (Recompiled for IDA Pro)

- 312 downloads
- Version 2.1
The Hex-Rays Decompiler plugin for better code navigation in RE process. CodeXplorer automates code REconstruction of C++ applications or modern malware like Stuxnet, Flame, Equation, Animal Farm ... Features: Automatic type REconstruction for C++ objects. To be able to reconstruct a type using HexRaysCodeXplorer one needs to select the variable holding pointer to the instance of position independed code or to an object and by right-button mouse click select from the context menu «REconstruct Type» option. Virtual function table identification - automatically identifies references to virtual function tables during type reconstruction. When a reference to a virtual function table is identified the plugin generates a corresponding C-structure. As shown below during reconstructing struct_local_data_storage two virtual function tables were identified and, as a result, two corresponding structures were generated: struct_local_data_storage_VTABLE_0 and struct_local_data_storage_VTABLE_4. C-tree graph visualization – a special tree-like structure representing a decompiled routine in citem_t terms (hexrays.hpp). Useful feature for understanding how the decompiler works. The highlighted graph node corresponds to the current cursor position in the HexRays Pseudocode window Ctree Item View – show ctree representation for highlighted element Extract Types to File – dump all types information (include reconstructed types) into file. Navigation through virtual function calls in HexRays Pseudocode window. After representing C++ objects by C-structures this feature make possible navigation by mouse clicking to the virtual function calls as structure fields Jump to Disasm - small feature for navigate to assembly code into "IDA View window" from current Pseudocode line position. It is help to find a place in assembly code associated with decompiled line. Object Explorer – useful interface for navigation through virtual tables (VTBL) structures. Object Explorer outputs VTBL information into IDA custom view window. The output window is shown by choosing «Object Explorer» option in right-button mouse click context menu Support auto parsing RTTI objects This plugin is recompiled by disauto UPDATE 29.10.2024 Recompiled for IDA Pro v9.0 Windows x86_644 points -
The Enigma Protector v7.70 (x32 & x64)
- 156 downloads
This is an example program I used to shell The Enigma 7.7. You can shell it, bypass it, PatchHWID, KeyGen to make it run normally. Of course, it would be best if the shell could be peeled off.Have fun! https://workupload.com/file/EGgppWamMA6 Cracked:4 points -
Serial Fishing Tutorials
 4 points
4 points -
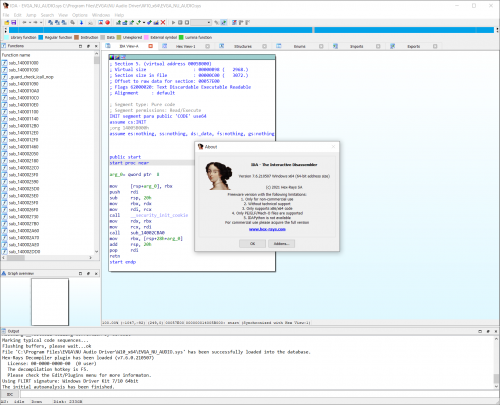
IDA Freeware
 4 points
4 points- 2,187 downloads
- Version 8.3.230608
This (completely!) free version of IDA offers a privilege opportunity to see IDA in action. This light but powerful tool can quickly analyze the binary code samples and users can save and look closer at the analysis results. What’s included in the pack? Analyze both 32-bit and 64-bit applications Cloud-based x64 decompiler Local x86/x64 debugger included Support x86/x64 processors Save your analysis results Perpetual license The freeware version of IDA v7.6 comes with the following limitations: no commercial use is allowed lacks all features introduced in IDA > v7.6 cloud-based decompiler lacks certain advanced commands lacks support for many processors, file formats, etc… comes without technical support4 points -
TiGa IDA Series (1-12)
4 points
- 1,360 downloads
TiGa 01 - Visual Debugging with IDA TiGa 02 - Remote Debugging with IDA Pro TiGa 03 - Debugging a Buggy Application with IDA Pro TiGa 04 - How to Solve CrackMes for Dummies in Video TiGa 05 - x64 Disassembling and Fixing Obfuscated API's TiGa 06 - TLS Callbacks and Preventing Debugger Detection TiGa 07 - Unwrapping a Flash Video Executable TiGa 08 - Stop Fishing and Start Keygenning! TiGa 09 - Alien Autopsy rev. 2008 TiGa 10 - Unpacking Deroko x64 UnPackMe TiGa 11 - Solving Pnluck x64 CrackMe TiGa 12 - Unpacking 4 Simple Packers with IDA4 points -
Silence's Unpacking Tour: The Enigma Protector 1.xx - 3.xx (Vol.1)

- 876 downloads
Today I release - finally - the series of unpacking tutorials about manually unpacking The Enigma Protector. I will discuss all protections of Enigma which are fully detailed as possible. I have to say thanks to LCF-AT, she helped me a lot with this. Introduction ~ 9:28 Unpacking with patterns ~ 33:03 Finding patch-places without patterns ~ 19:56 Dealing with SDK API's & Custom Emulated API's ~ 28:23 Internal & External VM's (Using Plugin) ~ 5:40 Enigma's Registration Scheme ~ 15:37 EN-DE-Cryption ~ 33:21 Inline patching + Final Words ~ 11:564 points -
Enigma Protector 4.10 (Unpacking)
 4 points
4 points- 2,011 downloads
A video tutorial showing a method of unpacking Enigma Protector 4.10.4 points -
Windows Anti-Debug Reference
 4 points
4 points- 588 downloads
- Version 1.0.0
This paper classifies and presents several anti-debugging techniques used on Windows NT-based operating systems. Anti-debugging techniques are ways for a program to detect if it runs under control of a debugger. They are used by commercial executable protectors, packers and malicious software, to prevent or slow-down the process of reverse-engineering. We'll suppose the program is analyzed under a ring3 debugger, such as OllyDbg on Windows platforms. The paper is aimed towards reverse-engineers and malware analysts. Note that we will talk purely about generic anti-debugging and anti-tracing techniques. Specific debugger detection, such as window or processes enumeration, registry scanning, etc. will not be addressed here.4 points -
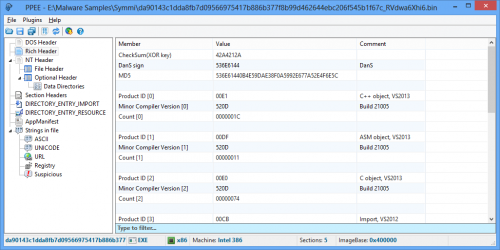
PPEE (puppy)
4 points
- 2,211 downloads
- Version 1.12
This is a professional PE file explorer that lets you dig into all data directories available in the PE/PE64 file and edit them. Export, Import, Resource, Exception, Certificate(Relies on Windows API), Base Relocation, Debug, TLS, Load Config, Bound Import, IAT, Delay Import and CLR are supported. Two companion plugins are also provided. FileInfo, to query the file in the well-known malware repositories and take one-click technical information about the file such as its size, entropy, attributes, hashes, version info and so on. YaraPlugin, to test Yara rules against opened file. Puppy is robust against malformed and crafted PE files which makes it handy for reversers, malware researchers and those who want to inspect PE files in more details. Puppy is free and tries to be small, fast, nimble and friendly as your puppy! Website: https://www.mzrst.com/4 points -
touka_tokyo DuP2 skin
 4 points
4 points- 317 downloads
- Version 1.0.0
hello friends , i hope you're having a good time . i spent all day trying to design a nice skin for DuP2 i've finished my work with a few mistakes . you know am a beginner and that's my first design , hope you like it Regards , Hamid .4 points -
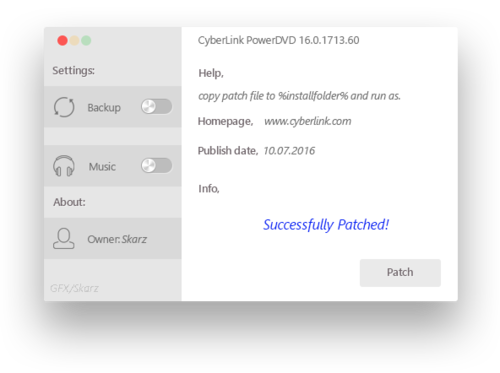
Skin AT4RE patcher - "The Game"
 4 points4 points
4 points4 points -
[URET Metal Skull dup]
 4 points
4 points -
tuts4you Symbolic logo source for GIMP

- 164 downloads
- Version 1.0.0
Hello friends. I try to prepare a classic logo for the forum. -Feel free to use in your projects or documents. I hope you will like it. note:Source file only xcf format. for GIMP. sory for photoshop users. Detailed previw ( click to support button in forum page.)4 points -
MacOSX Style uPPP Skin
 4 points
4 points- 167 downloads
- Version 1.0.0
Hi, Guys Let yourself go, the harmony of classic colors MacOSX Style uPPP interface by.Skarz..4 points -
REPT Patch Engine
 4 points
4 points- 2,025 downloads
- Version 0.2
Hello everyone! I made a new utility for Team Rept called "REPT Patch Engine". As it name says, this patch engine provides you an easy to use interface to make different types of patch in one single executable. Currently it has 3 types of patching method: Hex Editor (Offset Patch) File Export Registry Patch This utility is made on .NET. I did NOT put any credit of "Created with REPT Patch Engine" because I wanted to make a new patch engine useful. Things to update for next versions: Compare files to see the offset of cracked and original file. DONE! Add custom skin If you need another thing to put on the patch tell me I hope you like it and it could be interesting to use. Fell free to use as you want. LordCoder4 points -
The Legend of R4ndom Tutorials
 3 points
3 points- 2,689 downloads
R4ndom’s Beginning Reverse Engineering Tutorials Tutorial #1 - What is reverse engineering? Tutorial #2 - Introducing OllyDBG Tutorial #3 - Using OllyDBG, Part 1 Tutorial #4 - Using OllyDBG, Part 2 Tutorial #5 - Our First (Sort Of) Crack Tutorial #6 - Our First (True) Crack Tutorial #7 - More Crackmes Tutorial #8 - Frame Of Reference Tutorial #9 - No Strings Attached Tutorial #10 - The Levels of Patching Tutorial #11 - Breaking In Our Noob Skills Tutorial #12 - A Tougher NOOBy Example Tutorial #13 - Cracking a Real Program Tutorial #14 - How to remove nag screens Tutorial #15 - Using the Call Stack. Tutorial #16A - Dealing with Windows Messages. Tutorial #16B - Self Modifying Code. Tutorial #16C - Bruteforcing. Tutorial #17 - Working with Delphi Binaries. Tutorial #18 - Time Trials and Hardware Breakpoints. Tutorial #19 - Creating patchers. Tutorial #20A - Dealing with Visual Basic Binaries, Part 1. Tutorial #20B - Dealing with Visual Basic Binaries, Part 2. Tutorial #21 - Anti-Debugging Techniques. Tutorial #22 - Code Caves and PE Sections. Tutorial #23 - TLS Callbacks. Modifying Binaries For Fun And Profit Adding a Splash Screen - Creating a code cave to show a custom splash on an application Adding a Menu Item - Adding a menu item to an existing binary. Making a Window Non-Closeable - Making a Window Non-Closeable. The Never Ending Program - Opening message boxes every time a user tries to close a program. DLL Injection 1 - Adding an opening message box through DLL injection. DLL Injection 2 - Adding a splash bitmap through DLL injection. R4ndom’s Guide to RadASM Installing and setting up - Installing RadASM and configuring the environment. Creating our first project - Creating our first project. Adding an Icon and Menu - Adding an Icon and Menu. Miscellaneous The Reverse Engineer’s Toolkit - Tools every reverse engineer should know about. Shrinking C++ Binaries - Shrinking binaries through Visual Studio. Other Tutorials Author Tutorial XOR06 Cracking DriverFinder nwokiller Unpacking PELock v1.06 XOR06 Bypassing a keyfile XOR06 Bypassing a Serial and server Check XOR06 Bypassing a Serial in a Delphi Binary XOR06 Finding a serial using bitmaps. XOR06 Easy unpacking. XOR06 Where and How to pacth a serial routine. XOR06 Patching a server check, 30 day time trial, and a nag. XOR06 Serialfishing a correct serial. XOR06 Another way of finding the patch. XOR06 Why it’s so important to search for pointers. XOR06 .NET Crackme with tutorial XOR06 .NET Crackme (no tutorial)3 points -
Fravias First Period: Reverse Engineering ("Reality Cracking") (1995 - 1999)

- 895 downloads
My reader, this labyrinth of pages (you'll never be able to count them all) contains many teachings, and will help you gain knowledge that you will not find elsewhere. Please wander slowly inside: sip a good cocktail, take your time and explore at a leisurely pace. You'll find lessons on how to reverse engineer windows, dos, linux and palmtop programs, both in order to protect or to deprotect them (fairly easy, once you learn it); on how to search the Web using advanced techniques like 'combing' and 'klebing' (not so easy); on how to gain real information (pretty difficult), on how to track pseudoanonymous people on the web (fairly difficult), on how to protect your anonymity browsing the Web (quite difficult), on how to reverse the reality around you (very difficult), on how to destroy web sites you do not like (easy... given some conditions), on how to use (and detect) steganographical encryptions, on how to reverse or implement javascript based site protections, on how to annoy spammers, reverse web-agents, trap bots, write your own spiders and much more. I hope you'll enjoy this visit. Your critics and suggestions are welcome.3 points -
RSA Keygenning (1-3)
 3 points
3 points- 180 downloads
RSA Tutorial 01 - Keygenning RSA RSA Tutorial 02 - Serial Fishing RSA RSA Tutorial 03 - How to Find RSA Primes3 points -
HASP HL Envelope 1.x (Unpacking)
 3 points
3 points- 1,035 downloads
This document explains how to unpack the HASP HL Envelope.3 points -
HASP SL - A Deeper Dig
 3 points
3 points- 675 downloads
In my previous tutorial on HASP SL (6.41.95) I demonstrated how to easily find the OEP, dumping and rebuilding of the target application. The main goal of this tutorial is to do a little more in-depth analysis, how to manually bypass the anti-debug feature and finding out what version you are dealing with etc. Also this tutorial includes a flash-movie of the manual handy work described in this tutorial. Dodging the anti-debug, finding OEP, dumping and rebuilding. All done in about 2.5 minutes! Edit: This new version of HASP SL - A Deeper Dig features some new info on the encryption, anti-dumping and how to inline patch it.3 points -
Scylla Imports Reconstruction Source
3 points
- 5,492 downloads
- Version 0.9.8
Scylla - x64/x86 Imports Reconstruction ImpREC, CHimpREC, Imports Fixer... this are all great tools to rebuild an import table, but they all have some major disadvantages, so I decided to create my own tool for this job. Scylla's key benefits are: x64 and x86 support full unicode support written in C/C++ plugin support works great with Windows 7 This tool was designed to be used with Windows 7 x64, so it is recommend to use this operating system. But it may work with XP and Vista, too. Source code is licensed under GNU GENERAL PUBLIC LICENSE v3.0 https://github.com/NtQuery/Scylla https://github.com/x64dbg/Scylla3 points -
Fonts i am most use
 3 points
3 points -
PE Location Calculator
3 points
- 1,210 downloads
- Version 0.1
This is a simple utility to convert between ImageBase, VA, RVA & File offset3 points -
UndeadFactory dUP2 Skin
 3 points3 points
3 points3 points -
700 Olly scripts
3 points
- 7,521 downloads
- Version 700 Olly scripts
I know everyone Knows How To use this.But those hu dont know may goo on first of all download ollydbg script plugin from attachment and paste in olly directory... then extract this 700 scripts to any folder then simply detect any packed/protected file with peid or RDG and goto olly and plugin>run script and simply open the script belongs to any protection or packing...3 points
.thumb.jpg.e41d4991c184d8bb48d24fc4610d7926.jpg)