- 813 downloads
- Version v1.9
============================ AT4RE Power Loader v0.1 (Release Date: 26/03/2025) ============================
[+] Console interface
[+] Loader Coded in C++ with CRT (big Size: 85 KB when compressed about 190 KB uncompressed).
[+] Supports patching single or multiple Relative Virtual Addresses (RVAs).
Root Folder Contents:
[+] ATPL.EXE (AT4RE Power Loader)
[+] Version History.txt
============================ AT4RE Power Loader v0.2 (Release Date: 16/04/2025) ============================
The most powerful loader against strong and hard protectors.
It also works with medium-level protectors, packers, compressors, and even unprotected executable files.
Main Features:
[+] GUI Coded in Borland Delphi 7
[+] From the GUI, you can browse to select the target file (maximum filename length is 255 characters).
[+] You can also copy and paste the file name into the input field.
[+] Choose between x32 and x64 loader versions.
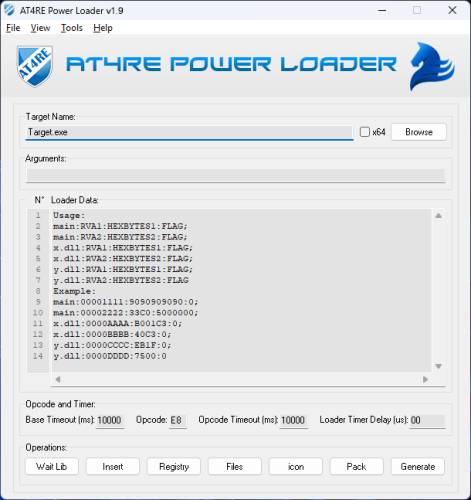
[+] Loader data can be entered only in the format shown in filed or in the screenshot.
[+] Set a base timeout in milliseconds (Minimum: 00, Maximum: 9999 — i.e., 9.99 seconds).
[+] Set 1-byte opcodes in the Opcode field using HEX characters (Opcode is the Original First Byte of RVA1).
[+] Configure Opcode Timeout in milliseconds (Minimum: 00, Maximum: 9999 — i.e., 9.99 seconds).
[+] Set the Loader Timer Delay in microseconds (Min: 00, Max: 9,999,999 — i.e., 9.99 seconds).
[+] Configure the loader to start as Administrator.
[+] Directly pack the loader with UPX.
[+] Generate Loader.exe
[+] Save or open projects for future use from File menu.
[+] Set the GUI to "most on top" from the View menu.
[+] Access the official website, report bugs, and find more information via about in the Help menu.
Loader Details:
[+] Coded in C++ using the Windows Pure API.
[+] Loader size is 10 KB uncompressed, and 5 KB when compressed.
[+] Supports Windows 7, 8, 10, and 11 (both x32 and x64).
Features include:
[+] Anti-ASLR
[+] Anti-Anti-Debug
[+] Anti-CRC Check
[+] Automatically detects the base address.
[+] Detects when the protector unpacks code into memory.
[+] Can apply temporary patches after a specified delay in microseconds (Patch and restor original bytes).
[+] Can apply permanent patches only with 00 Flag
[+] Supports patching single or multiple Relative Virtual Addresses (RVAs).
[+] Capable of patching up to 2048 bytes.
[+] Can run as Administrator or Normal user mode.
Root Folder Contents:
[+] Project folder (Save or open projects for future use)
[+] UPX folder (includes upx32.exe and upx64.exe)
[+] ATPL.EXE (AT4RE Power Loader)
[+] Version History.txt
============================ AT4RE Power Loader v0.3 (Release Date: 10/05/2025) ============================
The most powerful loader against strong and hard protectors.
It also works with medium-level protectors, packers, compressors, and even unprotected executable files.
Main Features:
[+] Added Support Patching DLLs (Only DLLs Loaded by Target.exe).
[+] Added Drag Drop Feature: For .EXE, .REG, .ICO Files.
[+] Added Insert Loader Data feature (For Respect the Correct Format).
[+] Added Registry Keys Manager (Max size: 1 KB / 1024 characters).
[+] Added Delete Files feature (Max size: 1 KB / 1024 characters).
[+] Added Icon Changer.
[+] Added New Project option from File menu (Clears all fields).
[+] Added Commands Shortcut Ctrl+N, Ctrl+O, Ctrl+S in File menu.
[+] Added Contact Us section from Help menu.
[+] Updated About from Help menu from box to a form.
[+] Updated display fonts for Loader Data, Registry, and Files.
[-] Removed "My Target run as admin".
Loader Details:
[+] Size is now 17 KB uncompressed, 7 KB when compressed.
[+] Loader now Support Patching DLLs (Only DLLs Loaded by Target.exe).
[+] Loader can now add or delete registry keys.
[+] Loader can delete files.
[+] Automatically requests Run as Administrator when needed
(e.g.,Target need administrator privilege, modifying registry or deleting files from protected folders).
[+] Icon support added.
Root Folder Contents:
[+] Icons folder (includes 5 icons).
[+] Lib folder (includes bass.dll).
[+] Project folder (Save or open projects for future use).
[+] ResH folder (includes ResHacker.exe).
[+] UPX folder (includes upx32.exe and upx64.exe).
[+] ATPL.EXE (AT4RE Power Loader).
[+] Version History.txt
============================ AT4RE Power Loader v0.4 (Release Date: 16/05/2025) ============================
The most powerful loader against strong and hard protectors.
It also works with medium-level protectors, packers, compressors, and even unprotected executable files.
Main Features:
[+] Added Import menu.
[+] Added Support .1337 patch files exported by x64dbg.
[+] Set Opcode automatically when Load .1337 file.
[+] Added OpenDialog when Double Click on:
- Target Name field.
- Loader Data field.
- Registry field.
- Custom icon field.
Loader Details:
[+] Fixed bug with registry feature.
[+] Default icon changed.
[+] Compressed Loader with Default icon 8 KB.
Root Folder Contents:
[+] Icons folder (includes 5 icons).
[+] Lib folder (includes bass.dll).
[+] Project folder (Save or open projects for future use).
[+] ResH folder (includes ResHacker.exe).
[+] UPX folder (includes upx32.exe and upx64.exe).
[+] ATPL.EXE (AT4RE Power Loader).
[+] Version History.txt