Leaderboard
-


lovejoy226
Full Member+94Points1,434Posts -

CodeExplorer
Team Member84Points4,532Posts -

X0rby
Full Member19Points344Posts -

ledlou
Full Member19Points46Posts
Popular Content
Showing content with the highest reputation since 01/01/2026 in all areas
-
Compiling Unlicense
 5 pointsThis is a very bad thing to add! Grabbing this personal information from a user without mentioning that is a terrible act to do !! Now you have ip @ of @CodeExplorer did you ask him if he agreed to that or not?? No! So that's why everyone must run any garbage from the internet on an isolated machine!5 points
5 pointsThis is a very bad thing to add! Grabbing this personal information from a user without mentioning that is a terrible act to do !! Now you have ip @ of @CodeExplorer did you ask him if he agreed to that or not?? No! So that's why everyone must run any garbage from the internet on an isolated machine!5 points -
Themida & VMProtect (Same Virtualized Code Sections)
(1) I never accused you of lying (2) I don't care about your "tools" My point is crystal clear: this site will continue to die if we allow such "solutions" (which are 9/10 just people using public tooling and therefore can't provide any novel contributions). Go ahead, feel free to discuss the "internals", which was arguably the bare minimum you should have provided in the original response to this challenge.4 points
-
Themida & VMProtect (Same Virtualized Code Sections)
Wow, very helpful 🙄 Every "solution" on this site is the most Cleo like response ever. I swear in almost every challenge, someone throws the .exe into public tooling, uploads the output, and provides zero explanation -- likely with the hope that people view them in awe. In my opinion, such solutions should result in consequences for the poster. This site will continue to die if people continue with these dull answers. For those interested in tackling such protection schemes, I would recommend: (1) https://github.com/NaC-L/Mergen (2) https://github.com/Colton1skees/Dna (3) https://whereisr0da.github.io/blog/posts/2021-02-16-vmp-3 (4) https://secret.club/2021/09/08/vmprotect-llvm-lifting-1.html4 points
-
Themida v3.1.4 (x32 & x64) - Impossible
This one is an interesting sample. Code is really small, so it was stolen completely, thus it's hard to tell app code from protector code. Functional code is quite simple, just MessageBoxA. And that's it, it does nothing more. After showing the message box it starts freeing memory that definitely isn't app code. But for the sake of completeness let's get to the bottom of this. We have 8 more code bytes. And we have 1 reloc pointing there, meaning ExitProcess should perfectly fit in. Unpacked file attached with code, import and relocs restored and sections cut. unpacked.exe3 points
-
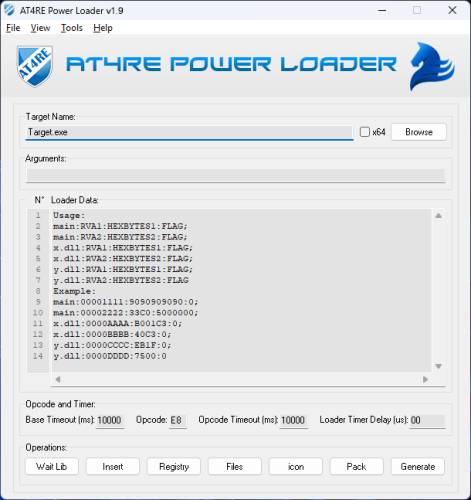
AT4RE Power Loader
 3 pointsSome times to make patch to DLL file with our tool you need to understand when dll target get unpacked firstly this is the most important, and for that you need to understand the best moment of pointer position in main exe while debugging, our Loader able to detect Static Opcode in Static Stack, if you use this way you can Creat a Strong Loader for your Target EXE or DLL.3 points
3 pointsSome times to make patch to DLL file with our tool you need to understand when dll target get unpacked firstly this is the most important, and for that you need to understand the best moment of pointer position in main exe while debugging, our Loader able to detect Static Opcode in Static Stack, if you use this way you can Creat a Strong Loader for your Target EXE or DLL.3 points -
Compiling Unlicense
 3 pointsIf you don’t care about “random forum users”, then don’t publish things publicly. You posted it here on purpose, so a public post means public criticism. You don’t get to choose who is allowed to comment... The website example is bullshit. A website logging IPs during an HTTP request is not the same as an executable secretly making outbound connections. The protocol forces one; the other is a decision you coded yourself. Acting like they’re the same is dishonest. Running a program does not mean permission for hidden network activity.3 points
3 pointsIf you don’t care about “random forum users”, then don’t publish things publicly. You posted it here on purpose, so a public post means public criticism. You don’t get to choose who is allowed to comment... The website example is bullshit. A website logging IPs during an HTTP request is not the same as an executable secretly making outbound connections. The protocol forces one; the other is a decision you coded yourself. Acting like they’re the same is dishonest. Running a program does not mean permission for hidden network activity.3 points -
Please help to reverce an ASM function.
 #include <stdint.h> #include <string.h> #include <stdio.h> #ifndef _WIN32 #define __stdcall #endif int __stdcall ted(uint8_t* input_buf, uint8_t* output_buf, uint8_t arg_8) { uint8_t permuted_input[10]; permuted_input[0] = input_buf[6]; // var_10 permuted_input[1] = input_buf[9]; // var_F permuted_input[2] = input_buf[1]; // var_E permuted_input[3] = input_buf[4]; // var_D permuted_input[4] = input_buf[8]; // var_C permuted_input[5] = input_buf[3]; // var_B permuted_input[6] = input_buf[7]; // var_A permuted_input[7] = input_buf[0]; // var_9 permuted_input[8] = input_buf[5]; // var_8 permuted_input[9] = input_buf[2]; // var_7 uint8_t var_24[4] = {0, 0, 0, 0}; uint8_t key_string[] = { 0x6F, 0x6D, 0x65, 0x64, 0x4F, 0x4D, 0x45, 0x44, 0x45, 0x44, 0x4F, 0x4D }; uint8_t var_1D = 0xEA; for (int i = 0; i < 10; i++) { uint8_t val = permuted_input[i]; uint16_t product1 = (i + 1) * val; uint8_t p1_low = (uint8_t)product1; var_24[0] += p1_low; var_24[1] -= p1_low; uint16_t product2 = (i + 0x38) * val; var_24[2] += (uint8_t)product2; } uint8_t al = var_24[0] * permuted_input[0]; uint8_t bl = var_24[1] ^ al; var_24[2] = ((bl + 1) ^ var_24[2]) & 3; uint8_t current_dl = var_1D; for (int i = 0; i < 12; i++) { uint8_t key_char = key_string[i]; - // The original assembly does: mov al, [ebp + key_char + var_10] // This reads outside the 'permuted_input' array. uint8_t magic_byte = *( (&permuted_input[0]) + key_char ); uint8_t calculated = magic_byte ^ current_dl; uint8_t add_val = (uint8_t)(i * 5); calculated += add_val; output_buf[i] = calculated; current_dl = calculated + 0x22; } uint8_t final_byte = ((arg_8 * 4) & 0x0C) | var_24[2]; output_buf[12] = final_byte; return 1; } int main() { uint8_t input[] = {0,1,2,3,4,5,6,7,8,9}; uint8_t output[13]; ted(input, output, 0x10); return 0; }3 points
#include <stdint.h> #include <string.h> #include <stdio.h> #ifndef _WIN32 #define __stdcall #endif int __stdcall ted(uint8_t* input_buf, uint8_t* output_buf, uint8_t arg_8) { uint8_t permuted_input[10]; permuted_input[0] = input_buf[6]; // var_10 permuted_input[1] = input_buf[9]; // var_F permuted_input[2] = input_buf[1]; // var_E permuted_input[3] = input_buf[4]; // var_D permuted_input[4] = input_buf[8]; // var_C permuted_input[5] = input_buf[3]; // var_B permuted_input[6] = input_buf[7]; // var_A permuted_input[7] = input_buf[0]; // var_9 permuted_input[8] = input_buf[5]; // var_8 permuted_input[9] = input_buf[2]; // var_7 uint8_t var_24[4] = {0, 0, 0, 0}; uint8_t key_string[] = { 0x6F, 0x6D, 0x65, 0x64, 0x4F, 0x4D, 0x45, 0x44, 0x45, 0x44, 0x4F, 0x4D }; uint8_t var_1D = 0xEA; for (int i = 0; i < 10; i++) { uint8_t val = permuted_input[i]; uint16_t product1 = (i + 1) * val; uint8_t p1_low = (uint8_t)product1; var_24[0] += p1_low; var_24[1] -= p1_low; uint16_t product2 = (i + 0x38) * val; var_24[2] += (uint8_t)product2; } uint8_t al = var_24[0] * permuted_input[0]; uint8_t bl = var_24[1] ^ al; var_24[2] = ((bl + 1) ^ var_24[2]) & 3; uint8_t current_dl = var_1D; for (int i = 0; i < 12; i++) { uint8_t key_char = key_string[i]; - // The original assembly does: mov al, [ebp + key_char + var_10] // This reads outside the 'permuted_input' array. uint8_t magic_byte = *( (&permuted_input[0]) + key_char ); uint8_t calculated = magic_byte ^ current_dl; uint8_t add_val = (uint8_t)(i * 5); calculated += add_val; output_buf[i] = calculated; current_dl = calculated + 0x22; } uint8_t final_byte = ((arg_8 * 4) & 0x0C) | var_24[2]; output_buf[12] = final_byte; return 1; } int main() { uint8_t input[] = {0,1,2,3,4,5,6,7,8,9}; uint8_t output[13]; ted(input, output, 0x10); return 0; }3 points -
Obsidium v1.6.9
 2 pointsInteresting 🌝 this is reminded me to the old days, is it possible to create a tutorial video I don't see good unpacking tutorials theses days2 points
2 pointsInteresting 🌝 this is reminded me to the old days, is it possible to create a tutorial video I don't see good unpacking tutorials theses days2 points -
Themida v3.1.4 (x32 & x64) - Impossible
 Themida v3.1.4 (x32 & x64) - Impossible Two files are protected with an old version Themida (3.1.4) Entry Point is virtualized Just find and restore OEP, recover the IAT and unpack if it possible Virustotal detects it as a virus, but my AV software is not File Information Submitter fReestYler Submitted 05/10/2025 Category UnPackMe View File2 points
Themida v3.1.4 (x32 & x64) - Impossible Two files are protected with an old version Themida (3.1.4) Entry Point is virtualized Just find and restore OEP, recover the IAT and unpack if it possible Virustotal detects it as a virus, but my AV software is not File Information Submitter fReestYler Submitted 05/10/2025 Category UnPackMe View File2 points -
AT4RE Power Loader
 2 pointsHere is an Example: DLL Protected By: ASProtect v2.x Static Opcode in Static Stack: Result: Test Files With ATPL Project & Loader: https://mega.nz/file/HZwxhA7J#aTuTBmfXkWbuGiMWaBhPTJpOfcoJsIB9jGDBkycilww Greetings AT4RE2 points
2 pointsHere is an Example: DLL Protected By: ASProtect v2.x Static Opcode in Static Stack: Result: Test Files With ATPL Project & Loader: https://mega.nz/file/HZwxhA7J#aTuTBmfXkWbuGiMWaBhPTJpOfcoJsIB9jGDBkycilww Greetings AT4RE2 points -
Compiling Unlicense
 2 pointsThat’s a weak excuse. “Reverse engineering forum” is not a reason to steal personal data. Running unknown binaries in a VM is indeed a good practice, not a license for you to silently collect IPs or any identifying info without disclosure. The problem isn’t whether it’s legal, it’s that you did not inform the user, If your app contacts a license server and logs IPs that must be stated explicitly ! Saying “it only collects minimal data” after the fact doesn’t change anything. Consent is obtained before, not justified after and “statistics” doesn’t magically make undisclosed data collection acceptable. Reverse engineering is about analyzing protections and behavior not normalizing shady practices and then hiding behind assumptions.2 points
2 pointsThat’s a weak excuse. “Reverse engineering forum” is not a reason to steal personal data. Running unknown binaries in a VM is indeed a good practice, not a license for you to silently collect IPs or any identifying info without disclosure. The problem isn’t whether it’s legal, it’s that you did not inform the user, If your app contacts a license server and logs IPs that must be stated explicitly ! Saying “it only collects minimal data” after the fact doesn’t change anything. Consent is obtained before, not justified after and “statistics” doesn’t magically make undisclosed data collection acceptable. Reverse engineering is about analyzing protections and behavior not normalizing shady practices and then hiding behind assumptions.2 points -
Revteam Reverse Engineering Collection
 2 points
2 points -
Go Figure!!!
1 pointTutorial (Short version): The kgm does the following: 1) Looks for the file "duh!!.syk" in the same directory (folder), if not found, it loads showing one field only (badboy), else: 2) Reads the text line inside the file "duh!!.syk" & by using a simple (xor 0x40) with each character, result should read "TestingOurSync???", else (badboy) 3) Loads the full form showing both text fields (i.e: name & serial) & a check button. Now try: name: Chilling serial: o!h.$kLB[2E{(,YV;+X/]thj}H.(uCFT~1Wx2iWM;4T*)Y$S"1B.$wcS@J Click the check button & the kgm will: 4) Trims both strings, Base91 decodes the serial into: "26734308-=`~<-YAGAIV-2090603021-2C51325133CEA38" Checks to see if it has 5 parts (separated by "-"), else (badboy). More checks follow. 5) part1 must be 8 characters from "0123456789" 6) part2 must be 4 characters from "$+<=>|~" 7) part3 must be 6 characters from "ABCDEFGHIJKLMNOPQRSTUVWXYZ" 8) Build & check part4: a) Uppercase the constant "If I Only Knew" & add a null byte at start then SDBM Hash (Ozan Yigit) it (in reverse order): 0x57454E4B20594C4E4F204920464900 = 0x7D0BFCAF b) math: 0x7D0BFCAF xor 0x46 (a constant) = 0x7D0BFCE9 c) math: 0x7D0BFCE9 xor StrToInt(p1) 0x0197EEE4 = 0x7C9C120D d) IntToStr(0x7C9C120D) = "2090603021" <> p4 = "2090603021" 9) Check if trimmed name is 4 or more characters (kind of late), else bb 10) Let s1 be the result of joining: name + ' ' (space) + constant "Jalolo" ... "Chilling Jalolo" 11) Let s2 be the result of joining: s1 + constant "WhoamI?" ... "Chilling JaloloWhoamI?" 12) Generate a seed by applying same SDBM Hash method on s2 (uppercase, add a null byte at start, ...) to get: 0x3F494D414F48574F4C4F4C414A20474E494C4C49484300 = 0x0BE39B81 ... seed 13) Build & check part5: Using xxHash64 (Yann Collet), perform xxHash64(WideString(s1), Integer(seed)) = "2C51325133CEA38" <> to p5 If all goes well then (goodboy). Let me know if I've missed anything :) Other combinations: name: XorRanger's Go Figure Fixed!!! serial: Rz;aAkGuG3Xtlk>V;+/zV0Tj|H.(~*AShw`EwnLdR2<:9[ZXjDhb|v1X;Lc name: Happy New Year! serial: E2wbCkcMh2E{(v$M)L!cgvY0|HS*SCBSn!IbLm?R$J+BD+gSzwIzml&M7Ia kg.7z1 point
-
Please help to reverce an ASM function.
var_2C= dword ptr -2Ch var_25= byte ptr -25h var_24= dword ptr -24h var_1E= byte ptr -1Eh var_1D= byte ptr -1Dh var_1C= dword ptr -1Ch var_18= dword ptr -18h var_14= dword ptr -14h var_10= byte ptr -10h var_F= byte ptr -0Fh var_E= byte ptr -0Eh var_D= byte ptr -0Dh var_C= byte ptr -0Ch var_B= byte ptr -0Bh var_A= byte ptr -0Ah var_9= byte ptr -9 var_8= byte ptr -8 var_7= byte ptr -7 var_6= byte ptr -6 var_5= byte ptr -5 arg_0= dword ptr 8 arg_4= dword ptr 0Ch arg_8= byte ptr 10h push ebp mov ebp, esp sub esp, 2Ch push ebx push esi push edi mov eax, [ebp+arg_0] movzx ecx, byte ptr [eax] movzx edx, byte ptr [eax+1] mov [ebp+var_9], cl movzx ecx, byte ptr [eax+2] mov [ebp+var_E], dl movzx edx, byte ptr [eax+3] mov [ebp+var_7], cl movzx ecx, byte ptr [eax+4] mov [ebp+var_B], dl movzx edx, byte ptr [eax+5] mov [ebp+var_D], cl movzx ecx, byte ptr [eax+6] mov [ebp+var_8], dl movzx edx, byte ptr [eax+7] mov [ebp+var_10], cl movzx ecx, byte ptr [eax+8] mov [ebp+var_A], dl movzx edx, byte ptr [eax+9] mov al, [ebp+arg_8] mov esi, [ebp+arg_4] add al, al add al, al mov [ebp+var_2C], esi mov [ebp+var_C], cl mov [ebp+var_F], dl mov [ebp+var_25], al mov [ebp+var_1C], 64656D6Fh mov [ebp+var_18], 44454D4Fh mov [ebp+var_14], 4D4F4445h mov [ebp+var_1D], 0EAh mov eax, 0 mov [ebp+var_24], eax xor ecx, ecx lea ecx, [ecx+0] loc_4011D0: mov dl, [ebp+ecx+var_10] mov bl, byte ptr [ebp+var_24+1] lea eax, [ecx+1] imul dl add byte ptr [ebp+var_24], al sub bl, al mov [ebp+var_1E], al lea eax, [ecx+38h] imul dl add byte ptr [ebp+var_24+2], al inc ecx mov byte ptr [ebp+var_24+1], bl cmp ecx, 0Ah jl short loc_4011D0 mov al, byte ptr [ebp+var_24] imul [ebp+var_10] mov dl, [ebp+var_1D] xor bl, al lea edi, [ebp+var_1C] mov [ebp+var_6], al mov [ebp+var_5], bl lea ecx, [ebx+1] xor cl, byte ptr [ebp+var_24+2] and cl, 3 mov byte ptr [ebp+var_24+2], cl xor ecx, ecx sub edi, esi jmp short loc_401223 jmp short loc_401220 align 10h loc_401220: mov esi, [ebp+var_2C] loc_401223: add esi, ecx movzx eax, byte ptr [edi+esi] mov al, [ebp+eax+var_10] xor al, dl mov dl, cl add dl, dl add dl, dl lea ebx, [edx+ecx] add al, bl inc ecx mov [esi], al lea edx, [eax+22h] cmp ecx, 0Ch jl short loc_401220 mov al, [ebp+var_25] mov ecx, [ebp+var_2C] and al, 0Ch or al, byte ptr [ebp+var_24+2] pop edi mov [ecx+0Ch], al pop esi xor ecx, ebp mov eax, 1 pop ebx mov esp, ebp pop ebp retnHi, is it possible this function to be reversed? The function has 2 parameters - (uint8_t* source, uint8_t* output). Would like to convert it to get the source from the output. Thanks in advance.1 point
-
Please help to reverce an ASM function.
1 point
-
Please help to reverce an ASM function.
 1 point
1 point -
Please help to reverce an ASM function.
X0rby what ai engine used to get this code? Haven't tried your code yet will try it asap. Looks very clean and simple. Fixed my code from Hex-ray and this is the decompiled working ok code: Obfuscate_Data(uint8_t* input, uint8_t* output) { int v2; uint8_t buffer[12]; uint8_t* output_1; int v5; int i; uint8_t v7; uint8_t v8; uint8_t v9; uint8_t n117_1; int n12; uint8_t* v12; uint8_t v13; uint32_t internal_state; uint8_t state; uint8_t table_var; uint32_t table[11]; buffer[0] = input[1]; HIBYTE(table[4]) = *input; buffer[4] = input[2]; BYTE2(table[3]) = buffer[0]; buffer[0] = input[3]; BYTE1(table[5]) = buffer[4]; buffer[4] = input[4]; BYTE1(table[4]) = buffer[0]; buffer[0] = input[5]; HIBYTE(table[3]) = buffer[4]; buffer[4] = input[6]; LOBYTE(table[5]) = buffer[0]; buffer[0] = input[7]; LOBYTE(table[3]) = buffer[4]; buffer[4] = input[8]; BYTE2(table[4]) = buffer[0]; buffer[0] = input[9]; output_1 = output; LOBYTE(table[4]) = buffer[4]; BYTE1(table[3]) = buffer[0]; table[0] = 0x6F6D6564; table[1] = 0x4F4D4544; table[2] = 0x45444F4D; table_var = 0xEA; internal_state = 0; v2 = 0; for (i = 0; i < 10; ++i) { v7 = *((_BYTE*)&table[3] + i); v8 = v7 * (i + 1); LOBYTE(internal_state) = v8 + internal_state; v9 = BYTE1(internal_state) - v8; BYTE2(internal_state) += v7 * (i + 56); BYTE1(internal_state) -= v8; } n117_1 = table_var; BYTE2(table[5]) = LOBYTE(table[3]) * internal_state; HIBYTE(table[5]) = (LOBYTE(table[3]) * internal_state) ^ v9; state = (BYTE2(internal_state) ^ (HIBYTE(table[5]) + 1)) & 3; n12 = 0; while (1) { v12 = &output_1[n12]; v13 = 5 * n12++ + (n117_1 ^ *((_BYTE*)&table[3] + v12[(char*)table - (char*)output])); *v12 = v13; n117_1 = v13 + 34; if (n12 >= 12) break; output_1 = output; } output[12] = state | (4 * v2) & 0xC; return 1; }But i need function that reverses the output of the function. I mean to get the input if i have the output buffer already. PS. Tried X0rby code but no luck it didn't give good result. Only the first byte is encoded ok with this function.1 point
-
Please help to reverce an ASM function.
1 point
-
Please help to reverce an ASM function.
Try AI, grok will give you a much better code but you will need several iterations till it gets a working one1 point
-
Pass Debugger Check in VMprotect 2.x
.thumb.jpeg.2543d876893bc4a3f440e4ab77c7e3f0.jpeg) @boot please can you again sign your titanhide driver (the certificate is revoked) or if possible can you share the method to load latest vmp in xdbg without titanhide? Thanks in Adv!1 point
@boot please can you again sign your titanhide driver (the certificate is revoked) or if possible can you share the method to load latest vmp in xdbg without titanhide? Thanks in Adv!1 point -
create backup(from olly) functionality in x64dbg
My previous video link is dead. Here below you can watch how to use my plugin.1 point
-
HPE Gen10 SmartMemory Authentication Bypass: Need help identifying the secondary Digital Signature
 1 pointTo avoid blind guessing, I suggest you to get old iLO firmware packages and analyze them. See what conditions must be fulfilled in order to get the "SmartMemory" status. If my google-fu is working, Gen10 servers use iLO5, here is it's general spec: https://www.hpe.com/us/en/collaterals/collateral.c04154343.html, and here are the download links https://support.hpe.com/connect/s/softwaredetails?language=en_US&collectionId=MTX-2dc80c4ae4b943fa. It would appear that older firmware packages didn't use any encryption, just some (trivial) compression, making the job so much easier.1 point
1 pointTo avoid blind guessing, I suggest you to get old iLO firmware packages and analyze them. See what conditions must be fulfilled in order to get the "SmartMemory" status. If my google-fu is working, Gen10 servers use iLO5, here is it's general spec: https://www.hpe.com/us/en/collaterals/collateral.c04154343.html, and here are the download links https://support.hpe.com/connect/s/softwaredetails?language=en_US&collectionId=MTX-2dc80c4ae4b943fa. It would appear that older firmware packages didn't use any encryption, just some (trivial) compression, making the job so much easier.1 point -
Compiling Unlicense
1 pointHere compiled unlicense with codeexplorer's fixes: unlicense compiled With pyton 3.09 and 3.11 versions.1 point
-
Lena's Reversing for Newbies
 1 point
1 point- 86,388 downloads
A collection of tutorials aimed particularly for newbie reverse engineers. 01. Olly + assembler + patching a basic reverseme 02. Keyfiling the reverseme + assembler 03. Basic nag removal + header problems 04. Basic + aesthetic patching 05. Comparing on changes in cond jumps, animate over/in, breakpoints 06. "The plain stupid patching method", searching for textstrings 07. Intermediate level patching, Kanal in PEiD 08. Debugging with W32Dasm, RVA, VA and offset, using LordPE as a hexeditor 09. Explaining the Visual Basic concept, introduction to SmartCheck and configuration 10. Continued reversing techniques in VB, use of decompilers and a basic anti-anti-trick 11. Intermediate patching using Olly's "pane window" 12. Guiding a program by multiple patching. 13. The use of API's in software, avoiding doublechecking tricks 14. More difficult schemes and an introduction to inline patching 15. How to study behaviour in the code, continued inlining using a pointer 16. Reversing using resources 17. Insights and practice in basic (self)keygenning 18. Diversion code, encryption/decryption, selfmodifying code and polymorphism 19. Debugger detected and anti-anti-techniques 20. Packers and protectors : an introduction 21. Imports rebuilding 22. API Redirection 23. Stolen bytes 24. Patching at runtime using loaders from lena151 original 25. Continued patching at runtime & unpacking armadillo standard protection 26. Machine specific loaders, unpacking & debugging armadillo 27. tElock + advanced patching 28. Bypassing & killing server checks 29. Killing & inlining a more difficult server check 30. SFX, Run Trace & more advanced string searching 31. Delphi in Olly & DeDe 32. Author tricks, HIEW & approaches in inline patching 33. The FPU, integrity checks & loader versus patcher 34. Reversing techniques in packed software & a S&R loader for ASProtect 35. Inlining inside polymorphic code 36. Keygenning 37. In-depth unpacking & anti-anti-debugging a combination packer / protector 38. Unpacking continued & debugger detection by DLL's and TLS 39. Inlining a blowfish scheme in a packed & CRC protected dll + unpacking Asprotect SKE 2.2 40. Obfuscation and algorithm hiding1 point -
Need some Tips for this keygen template I made
I commented out that portion of code because transparency works correctly, but if you look closely, it generates artifacts, especially when selecting text. However, I solved the problem just last night by looking at some templates on the forum in asm x86 and making the appropriate changes. Below, I show all the updated code. In attachment you will find image resource and the exe file. #include <windows.h> #include <wingdi.h> #include "ufmod.h" #include "resource.h" #include "song.h" #pragma comment(lib, "Msimg32.lib") #pragma comment(lib, "ufmod.lib") #pragma comment(lib, "winmm.lib") HINSTANCE hInst; HBITMAP hBackground = NULL; HBRUSH hBrushBackground = NULL; HBRUSH hBrush; COLORREF transparentColor = RGB(255, 0, 255); // Magenta color key // Bitmap per il pulsante di chiusura HBITMAP hBtnCloseNormal = NULL; HBITMAP hBtnCloseHover = NULL; // Procedura finestra del dialogo INT_PTR CALLBACK DialogProc(HWND hwndDlg, UINT uMsg, WPARAM wParam, LPARAM lParam) { switch (uMsg) { case WM_INITDIALOG: { HICON hIcon = LoadIcon(hInst, MAKEINTRESOURCE(IDI_ICON1)); SendMessage(hwndDlg, WM_SETICON, ICON_BIG, (LPARAM)hIcon); SetWindowText(hwndDlg, L"Keygen Template by jNe"); // Imposta il testo predefinito SetDlgItemText(hwndDlg, EDIT_username, L"Enter Username"); // play chip-tune <3 uFMOD_SetVolume(20); uFMOD_PlaySong(songData, (void*)sizeof(songData), XM_MEMORY); // BMP in background hBackground = LoadBitmap(GetModuleHandle(NULL), MAKEINTRESOURCE(BMP_form)); hBrush = CreatePatternBrush(hBackground); // set magenta color key SetLayeredWindowAttributes(hwndDlg, transparentColor, 0, LWA_COLORKEY); // --- FINE --- // BMP close hBtnCloseNormal = LoadBitmap(GetModuleHandle(NULL), MAKEINTRESOURCE(BMP_close)); hBtnCloseHover = LoadBitmap(GetModuleHandle(NULL), MAKEINTRESOURCE(BMP_close_hover)); if (hBtnCloseNormal) { HWND hBtnClose = GetDlgItem(hwndDlg, BTN_CLOSE); if (hBtnClose) { BITMAP bm; GetObject(hBtnCloseNormal, sizeof(bm), &bm); SetWindowPos(hBtnClose, NULL, 0, 0, bm.bmWidth, bm.bmHeight, SWP_NOMOVE | SWP_NOZORDER); } } } return TRUE; case WM_ERASEBKGND: return TRUE; case WM_PAINT: { PAINTSTRUCT ps; HDC hdc = BeginPaint(hwndDlg, &ps); if (hBackground) { HDC hdcMem = CreateCompatibleDC(hdc); HBITMAP hOldBmp = (HBITMAP)SelectObject(hdcMem, hBackground); BITMAP bm; GetObject(hBackground, sizeof(bm), &bm); BitBlt(hdc, 0, 0, bm.bmWidth, bm.bmHeight, hdcMem, 0, 0, SRCCOPY); SelectObject(hdcMem, hOldBmp); DeleteDC(hdcMem); } EndPaint(hwndDlg, &ps); } return TRUE; case WM_DRAWITEM: { LPDRAWITEMSTRUCT lpdis = (LPDRAWITEMSTRUCT)lParam; if (lpdis->CtlID == BTN_CLOSE) { HDC hdcMem = CreateCompatibleDC(lpdis->hDC); HBITMAP hBmpToUse; if (lpdis->itemState & ODS_SELECTED) { hBmpToUse = hBtnCloseHover; // HOVER } else { hBmpToUse = hBtnCloseNormal; // NORMAL } if (hBmpToUse) { HBITMAP hOldBmp = (HBITMAP)SelectObject(hdcMem, hBmpToUse); BitBlt(lpdis->hDC, lpdis->rcItem.left, lpdis->rcItem.top, lpdis->rcItem.right - lpdis->rcItem.left, lpdis->rcItem.bottom - lpdis->rcItem.top, hdcMem, 0, 0, SRCCOPY); SelectObject(hdcMem, hOldBmp); } DeleteDC(hdcMem); } } return TRUE; case WM_CTLCOLORDLG: return (INT_PTR)hBrush; case WM_CTLCOLOREDIT: case WM_CTLCOLORSTATIC: { HDC hdcEdit = (HDC)wParam; int controlId = GetDlgCtrlID((HWND)lParam); if (controlId == ABOUT) { SetBkMode(hdcEdit, TRANSPARENT); SetTextColor(hdcEdit, RGB(255, 255, 255)); SetBkColor(hdcEdit, 0x00000000); SetBrushOrgEx(hdcEdit, -23, -88, NULL); return (INT_PTR)hBrush; } if (controlId == EDIT_username) { SetBkMode(hdcEdit, TRANSPARENT); SetTextColor(hdcEdit, RGB(255, 255, 255)); SetBkColor(hdcEdit, 0x00000000); SetBrushOrgEx(hdcEdit, -23, -88, NULL); return (INT_PTR)hBrush; } if (controlId == EDIT_serial) { SetBkMode(hdcEdit, TRANSPARENT); SetTextColor(hdcEdit, RGB(255, 255, 255)); SetBkColor(hdcEdit, 0x00000000); SetBrushOrgEx(hdcEdit, -23, -151, NULL); return (INT_PTR)hBrush; } break; } case WM_LBUTTONDOWN: SendMessage(hwndDlg, WM_NCLBUTTONDOWN, HTCAPTION, 0); return TRUE; case WM_COMMAND: switch (LOWORD(wParam)) { case EDIT_username: { if (HIWORD(wParam) == EN_CHANGE) { char username[256]; GetDlgItemTextA(hwndDlg, EDIT_username, username, 256); SetDlgItemTextA(hwndDlg, EDIT_serial, "OMFG-THIS-IS-A-DEMO"); } break; } case BTN_CLOSE: SendMessage(hwndDlg, WM_CLOSE, 0, 0); return TRUE; } break; case WM_CLOSE: uFMOD_StopSong(); if (hBrush) DeleteObject(hBrush); if (hBackground) DeleteObject(hBackground); if (hBtnCloseNormal) DeleteObject(hBtnCloseNormal); if (hBtnCloseHover) DeleteObject(hBtnCloseHover); EndDialog(hwndDlg, 0); return FALSE; } return FALSE; } // Entry point int WINAPI WinMain(HINSTANCE hInstance, HINSTANCE hPrevInstance, LPSTR lpCmdLine, int nCmdShow) { hInst = hInstance; DialogBox(hInstance, MAKEINTRESOURCE(IDD_DIALOG1), NULL, DialogProc); return 0; } keygen template - fix.zip1 point
-
kill a process and prevent it from being created again
 Hi @LCF-AT , DriverMonitor is an old tool that has been released for over 20 years. I am accustomed to using this app to load some Windows drivers. For learning and testing purposes, I used some leaked certificates to sign this driver. Now I will upload the signed driver here. I have set up a callback function (ProcessNotifyExRoutine_call_back) in the driver to filter specific process names in order to prevent their loading. Therefore, before uninstalling the driver, the target process cannot be started. This simple APP can kill some driver-protected antivirus software or system-level processes. For example, antivirus software such as Kaspersky and Symantec. If you terminate the system processes (e.g. winlogon.exe and dwm.exe), it will result in a BSOD. bin_v0.002.zip(Requires: 64-bit OS & >= Windows 7) DriverMonitor_EN.rar Video_2025-09-14_161309.mp4 (4.69 MB)1 point
Hi @LCF-AT , DriverMonitor is an old tool that has been released for over 20 years. I am accustomed to using this app to load some Windows drivers. For learning and testing purposes, I used some leaked certificates to sign this driver. Now I will upload the signed driver here. I have set up a callback function (ProcessNotifyExRoutine_call_back) in the driver to filter specific process names in order to prevent their loading. Therefore, before uninstalling the driver, the target process cannot be started. This simple APP can kill some driver-protected antivirus software or system-level processes. For example, antivirus software such as Kaspersky and Symantec. If you terminate the system processes (e.g. winlogon.exe and dwm.exe), it will result in a BSOD. bin_v0.002.zip(Requires: 64-bit OS & >= Windows 7) DriverMonitor_EN.rar Video_2025-09-14_161309.mp4 (4.69 MB)1 point -
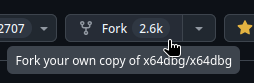
VMProtect Heaven's Gate Anti-Debug Bypass to VectorHandler
 Here are the steps to get a completely modified version of x64dbg. Go to https://github.com/x64dbg/x64dbg Press this button in the top-right corner of your screen: You can then change the code to your liking (e.g., to bypass the anti-debug problem).1 point
Here are the steps to get a completely modified version of x64dbg. Go to https://github.com/x64dbg/x64dbg Press this button in the top-right corner of your screen: You can then change the code to your liking (e.g., to bypass the anti-debug problem).1 point -
Revteam Reverse Engineering Collection
 My server is working, i just migrated to docker. (Its WebDav , https) https://eddynet.cz:9865 File list is in attached files. content_250414.7z1 point
My server is working, i just migrated to docker. (Its WebDav , https) https://eddynet.cz:9865 File list is in attached files. content_250414.7z1 point -
Searching for "The Weakness of the Windows API" by ARTeam
 @fearless Many thanks. I've forgotten the way to use "masm32" assembler. Regards. sean.1 point
@fearless Many thanks. I've forgotten the way to use "masm32" assembler. Regards. sean.1 point -
Searching for "The Weakness of the Windows API" by ARTeam
 Are there anyone who are able to build assembly dll source codes in the SRC folder? I have errors when assembling them. Many thanks in advance. Regards. sean.1 point
Are there anyone who are able to build assembly dll source codes in the SRC folder? I have errors when assembling them. Many thanks in advance. Regards. sean.1 point -
WinLicense v3.1.3.0 x86 (All Protection Options)
I admit it, I'm just showing off, you can show off if you have the ability. Unfortunately, apart from jealousy, you are useless. You only fantasize about getting someone else's knowledge without any effort. Anyone with some level of proficiency will think and search for clues based on the documents I provide. Only someone like you who only wants to get something for nothing would make these unreasonable demands? Everyone knows who the joke is. You can you up, No can no BB1 point
-
WinLicense v3.1.3.0 x86 (All Protection Options)
 😁 I'm not asking you to share your src or tuts/offer a solution. But your reply in my topic are these useful? No - absolutely not. Only one sentence, one picture, and one RAR package. Even more unfortunately, some files in your RAR package are deliberately VM some code snippets. What can the downloaders learn from your RAR package? Besides the analysis reply I provided, which downloader provided an effective analysis reply? In this topic, you're just trying to get attention by showing-off that you can do this with some deliberately modified files that don't have any useful information. We're here to learn and share knowledge. If you don't want to share, that's fine. No need to brag, but if you do, I don't mind. In addition, this topic would like to give special thanks to @TRISTAN Pro for selflessly sharing his tutorials and knowledge.1 point
😁 I'm not asking you to share your src or tuts/offer a solution. But your reply in my topic are these useful? No - absolutely not. Only one sentence, one picture, and one RAR package. Even more unfortunately, some files in your RAR package are deliberately VM some code snippets. What can the downloaders learn from your RAR package? Besides the analysis reply I provided, which downloader provided an effective analysis reply? In this topic, you're just trying to get attention by showing-off that you can do this with some deliberately modified files that don't have any useful information. We're here to learn and share knowledge. If you don't want to share, that's fine. No need to brag, but if you do, I don't mind. In addition, this topic would like to give special thanks to @TRISTAN Pro for selflessly sharing his tutorials and knowledge.1 point -
VMProtect v3.5.1
 1 point@CodeExplorer Can it be feasible to unpack this target with your method? Regards. sean.1 point
1 point@CodeExplorer Can it be feasible to unpack this target with your method? Regards. sean.1 point -
.NET Reactor v6.9
 1 point@CreateAndInject The same nationalities that you and he is. Oh, coincidence. Thank you @CreateAndInject for notifying the forum of it and him. Regards. sean.1 point
1 point@CreateAndInject The same nationalities that you and he is. Oh, coincidence. Thank you @CreateAndInject for notifying the forum of it and him. Regards. sean.1 point -
Enigma Protector v7.5(Shell 示例)
 1 pointHello, everyone. Is this enigma x64 one still able to be bypassed? Waiting for your replies as soon as possible. Many thanks in advance. Regards. sean.1 point
1 pointHello, everyone. Is this enigma x64 one still able to be bypassed? Waiting for your replies as soon as possible. Many thanks in advance. Regards. sean.1 point -
PatchMe No.1 2024 (x86 32-Bit)
 1 point
1 point -
VMProtect v3.8.1 Ultra (Mutation + Virtualization)
 Please record the process and post it, so we can get benefit from you. Regards. sean.1 point
Please record the process and post it, so we can get benefit from you. Regards. sean.1 point -
Pass Debugger Check in VMprotect 2.x
 I have tried to add Etw Hook's source code to the source code of TitanHide.sys, but it was not effective and I am not considering it for now. I will release newly compiled plugins and drivers, using methods to bypass signatures. They will not need to disable signatures and can be loaded in normal mode.1 point
I have tried to add Etw Hook's source code to the source code of TitanHide.sys, but it was not effective and I am not considering it for now. I will release newly compiled plugins and drivers, using methods to bypass signatures. They will not need to disable signatures and can be loaded in normal mode.1 point -
WinLicense v3.1.3.0 x86 (All Protection Options)
 1 point
1 point -
Flare-On 7
1 pointAfter spending three days i m still stuck at 4th challenge now i understand what it mean to be a reverse engineer. May be i will not solve all(or may be even the half of them) the challenge but i still try my best till the last day.1 point
-
Flare-On 7
 1 point@Rurik: why the kdnet requirement? Why 2 virtual machines? I'm no kernel debugging wizard by any means, but here's a primitive setup that serves me well. WinDbg runs on my main machine, connects to VMWare guest machine via a named pipe. Pretty much everything was taken from this guide: https://www.triplefault.io/2017/07/setting-up-kernel-debugging-using.html 1) Windbg - I have a BAT file with the command-line. It's used only for kernel debugging: windbg -k com:pipe,port=\\.\pipe\com_1,resets=0,reconnect 2) VMWare guest is set up to have virtual com port that uses named pipe: 3) When necessary, I enable kernel debugging in VMWare guest using bcdedit commands from elevated command prompt: bcdedit /debug on bcdedit /dbgsettings serial debugport:1 baudrate:115200 4) Reboot the guest machine, it will freeze for ~30 seconds waiting for WinDbg to attach. 5) Run WinDbg from .BAT file, done. If you insist on running WinDbg in the other VM, you can still link 2 machines via virtual com port and named pipes. I just quickly tried, something like this: 1) set up VMWare with kernel debugging enabled just like before. 2) set up VMWare with Windbg to use com port like this: Notice "this end is the client" setting 3) Start VMWare with WinDbg, run WinDbg like this: windbg -k com:port=COM1,baud=115200 4) (re-)start VMWare with kernel debugging enabled, WinDbg should automagically attach.1 point
1 point@Rurik: why the kdnet requirement? Why 2 virtual machines? I'm no kernel debugging wizard by any means, but here's a primitive setup that serves me well. WinDbg runs on my main machine, connects to VMWare guest machine via a named pipe. Pretty much everything was taken from this guide: https://www.triplefault.io/2017/07/setting-up-kernel-debugging-using.html 1) Windbg - I have a BAT file with the command-line. It's used only for kernel debugging: windbg -k com:pipe,port=\\.\pipe\com_1,resets=0,reconnect 2) VMWare guest is set up to have virtual com port that uses named pipe: 3) When necessary, I enable kernel debugging in VMWare guest using bcdedit commands from elevated command prompt: bcdedit /debug on bcdedit /dbgsettings serial debugport:1 baudrate:115200 4) Reboot the guest machine, it will freeze for ~30 seconds waiting for WinDbg to attach. 5) Run WinDbg from .BAT file, done. If you insist on running WinDbg in the other VM, you can still link 2 machines via virtual com port and named pipes. I just quickly tried, something like this: 1) set up VMWare with kernel debugging enabled just like before. 2) set up VMWare with Windbg to use com port like this: Notice "this end is the client" setting 3) Start VMWare with WinDbg, run WinDbg like this: windbg -k com:port=COM1,baud=115200 4) (re-)start VMWare with kernel debugging enabled, WinDbg should automagically attach.1 point -
HASP HL Envelope 1.x (Unpacking)
 1 point
1 point- 1,035 downloads
This document explains how to unpack the HASP HL Envelope.1 point -
[DevirtualizeMe] Themida 2.4.6.0
1 pointI do not release the decoder but the code optimizer (not immediately), this is not specific to the oream vm, it is only far more effective than others. What do you say about angr or miasm or optimice or codedoctor ?? do we eliminate them all the tools for binary code analysis ?? I do not issue the decoder code because my hobby is a hobby and I do not want to give anybody a damn but reversing is sharing (I unfortunately belong to the old old reverser school). If I spoke good English I would probably share a lot more info and would not like others who just write for self-celebration. Do you know Scherzo or Softworm ?? I'm an old man who now deals with reversing and my only good luck is that the day they will all program in python or javascript I will not be there anymore..hahahahaha1 point
-
[DevirtualizeMe] Themida 2.4.6.0
1 pointHi, I'm beginning not to ask for the program because I will not make it public, I do not want to harm anybody. Instead I will release the source code of the deobfuscator as soon as I have time to fix some points. @miraculix The deobfuser completely rebuilds the CFG (remove fake Jcc, Opaque Predicates etc .. etc ..) apply PeepHole (pattern recognition) remove DeadCode and Constant Folding and call analyzer and more. Thanks to the suggestions of @fvrmatteo I could try different peepHole solutions than the pattern recognition but the result was never as efficient as the use of pattern recognition so I use this solution at the moment (I reverse, not a conference at MIT code needs to work well .. hahahaha). I only use Pascal. As a disassembler engine use Capstone and as Emulator (for small portions of code) use Unicorn Engine.Not use Virtual Machines Symbolic Execution Phyton script etc .. etc .. Place a small video to give an idea. deob.rar1 point
-
VMProtect vs Themida
 1 pointFirst you say Themida is trashtier, then you pick a far inferior packer and state that it is better..? People need to start realizing, that if you have no clue what you're talking about, you should either start your sentence with "I assume" or you shouldn't say anything at all. Silence is bliss. VMProtect is actually rather bad, as the virtual machine in VMProtect is really easy to crack. If you have to choose between Themida and VMProtect, you should always pick Themida. Why? Because Themidas virtual machines are much more advanced and much harder to crack than VMProtect. Themida was initially known for their CISC VM which was (at the time) very strong. It has since been defeated (by Deathway) and is now considered weak (since it's actually rather simple once you start to understand it). VMProtect's virtual machine is almost an exact replica of the Themida CISC VM featuring stronger obfuscation, and as such it works in the exact same way, which makes it (almost) equally weak. Since then, Themida developed the RISC machine (RISC64 and RISC128), which was against defeated by Deathway. They then proceeded to develop the FISH and TIGER machines, which features very new tricks such as complex combined handlers (FISH) doing multiple operations each instead of a handler for each operation like CISC had, and also internal (yet simple) cryptography. The TIGER VM is very similar to the FISH VM (since it is built on the same engine), but doesn't utilize the cryptographic internal registers, etc. Themida also features hybrid virtual machines, such as SHARK, which is FISH virtualized by TIGER, or PUMA, which is TIGER virtualized by FISH. The newest machine(s) from Themida is the DOLPHIN machine, which is yet another layer of complexity upon the newer FISH/TIGER engine, while also supplying a hybrid VM called EAGLE, which is FISH virtualized by DOLPHIN (if memory serves right). If you want to compare the complexity of the newer Themida VMs (e.g. EAGLE) vs. VMProtect's VM, you're probably looking at a complexity scale saying 15:1 or something like that. TL;DR Don't listen to the guys above, as they are completely clueless on the topic. Pick Themida if you have to choose between the two of them.1 point
1 pointFirst you say Themida is trashtier, then you pick a far inferior packer and state that it is better..? People need to start realizing, that if you have no clue what you're talking about, you should either start your sentence with "I assume" or you shouldn't say anything at all. Silence is bliss. VMProtect is actually rather bad, as the virtual machine in VMProtect is really easy to crack. If you have to choose between Themida and VMProtect, you should always pick Themida. Why? Because Themidas virtual machines are much more advanced and much harder to crack than VMProtect. Themida was initially known for their CISC VM which was (at the time) very strong. It has since been defeated (by Deathway) and is now considered weak (since it's actually rather simple once you start to understand it). VMProtect's virtual machine is almost an exact replica of the Themida CISC VM featuring stronger obfuscation, and as such it works in the exact same way, which makes it (almost) equally weak. Since then, Themida developed the RISC machine (RISC64 and RISC128), which was against defeated by Deathway. They then proceeded to develop the FISH and TIGER machines, which features very new tricks such as complex combined handlers (FISH) doing multiple operations each instead of a handler for each operation like CISC had, and also internal (yet simple) cryptography. The TIGER VM is very similar to the FISH VM (since it is built on the same engine), but doesn't utilize the cryptographic internal registers, etc. Themida also features hybrid virtual machines, such as SHARK, which is FISH virtualized by TIGER, or PUMA, which is TIGER virtualized by FISH. The newest machine(s) from Themida is the DOLPHIN machine, which is yet another layer of complexity upon the newer FISH/TIGER engine, while also supplying a hybrid VM called EAGLE, which is FISH virtualized by DOLPHIN (if memory serves right). If you want to compare the complexity of the newer Themida VMs (e.g. EAGLE) vs. VMProtect's VM, you're probably looking at a complexity scale saying 15:1 or something like that. TL;DR Don't listen to the guys above, as they are completely clueless on the topic. Pick Themida if you have to choose between the two of them.1 point -
[DevirtualizeMe] Themida 2.4.6.0
1 pointHaven't touched this project for a long time. So I worked this weekend on updating the script and catching up with all the changes that they did in the last 1-2 years. Everything works right now except for TIGER. They added a new weird "push" handler, which is very different from any other TIGER handler. (the offset for the push isn't from a parameter, but from a call to another function that return an internal state value, usually that internal state value is used with a parameter to get the wanted real value, but this time it is used just with a constant number... in your binary for example one such handler is at 0x0562AC9). Nothing too bad, but I ran out of time for this weekend. I will do it during this week and update this comment with the devirtualized tiger when it is done. Except for that most of the changes were small. Some of them are fixing bugged handlers, other are adding some small protection templates to the handlers. One change that they did was not reseting the state when re-entering the vm after external instruction execution. (instructions that they don't virtualize). Another change was changing the start of the vm. Until now the start of the vm was something like that: (They push all the registers to the stack before they enter the vm) pop VM_REG_1 pop VM_REG_2 pop VM_REG_3 .. They changed it to: (in a random order) mov VM_REG_1, [esp] mov VM_REG_2, [esp+4] mov VM_REG_3, [esp+8] ... add esp, ... Another change is obfuscating the ending of some of the FISH and TIGER handlers. The FISH(32/64) BLACK is probably the most annoying vm. since the handlers are heavily obfuscated, with fake conditional jumps and all of that shit. One big handler can be 100000+ instructions. So even a small bug when handling it can fornication up everything. It is probably the safest vm because of that but also really really slow. oh, and in 64-bit my compiled devirtualized code isn't the same size as the original code, I am not sure why is that, which of the compiled opcodes take more space than the original . But I still had enough space for the devirtualized code in the original address because of the surrounding macros. devirtualizeme_tmd_2.4.6.0_fish32.devirtualize.clean.exe.7z devirtualizeme_tmd_2.4.6.0_fish64.devirtualize.clean.exe.7z1 point
-
Exit process without api
 1 pointPress the reset button on your PC. XOR EDX,EDX SYSENTER 4 Bytes only and bye bye. greetz1 point
1 pointPress the reset button on your PC. XOR EDX,EDX SYSENTER 4 Bytes only and bye bye. greetz1 point -
Driver Rootkit Analysis
 1 pointChances are that first packet, because your on a TCP/IP network is a broadcast for the MAC address if its not already been found and cached? But you should be able to confirm this by pinging the device and sniffing the packets... Ted.1 point
1 pointChances are that first packet, because your on a TCP/IP network is a broadcast for the MAC address if its not already been found and cached? But you should be able to confirm this by pinging the device and sniffing the packets... Ted.1 point -
[Delphi] Add Imports problem
 1 pointWell, you found the line where it crashes but the problem is much deeper. It's caused by pointers and memory reallocation. Something like this: Line 117: if FileToBytes(szFilePath, bFile) then // allocates a memory for TByteArray Line 134: IID := @bFile[dwIATPos]; // IID is a pointer into current TByteArray Line 145: SetLength(bFile, Length(bFile) + dwSize); // resizes TByteArray, memory is not reallocated yet Line 148: CopyMemory(@bFile[dwPos], @Imports.szLibName[1], Length(Imports.szLibName)); // first write into resized array, Delphi memory manager reallocates memory. IID is a pointer into garbage now. Line 149: IID.Name := OffsetToRVA(dwPos, ISH.VirtualAddress, ISH.PointerToRawData); // crash! Your code is quite a mess, so it's hard to give a suggestion how to fix it properly. I'd try avoid using pointers into bFile at all costs. Cheers, kao.1 point
1 pointWell, you found the line where it crashes but the problem is much deeper. It's caused by pointers and memory reallocation. Something like this: Line 117: if FileToBytes(szFilePath, bFile) then // allocates a memory for TByteArray Line 134: IID := @bFile[dwIATPos]; // IID is a pointer into current TByteArray Line 145: SetLength(bFile, Length(bFile) + dwSize); // resizes TByteArray, memory is not reallocated yet Line 148: CopyMemory(@bFile[dwPos], @Imports.szLibName[1], Length(Imports.szLibName)); // first write into resized array, Delphi memory manager reallocates memory. IID is a pointer into garbage now. Line 149: IID.Name := OffsetToRVA(dwPos, ISH.VirtualAddress, ISH.PointerToRawData); // crash! Your code is quite a mess, so it's hard to give a suggestion how to fix it properly. I'd try avoid using pointers into bFile at all costs. Cheers, kao.1 point