Leaderboard
-

CodeExplorer
Team Member1,194Points4,554Posts -


lovejoy226
Full Member+559Points1,437Posts -
jackyjask
Full Member+482Points1,645Posts -

whoknows
Full Member+187Points1,987Posts
Popular Content
Showing content with the highest reputation since 02/25/2025 in all areas
-
Prometheus (12 Layers of Insanity)
 11 pointshttps://dr4gan0x.github.io/dr4gan-portfolio/?post=prometheus-12-layers I hope this write up catches your interest11 points
11 pointshttps://dr4gan0x.github.io/dr4gan-portfolio/?post=prometheus-12-layers I hope this write up catches your interest11 points -
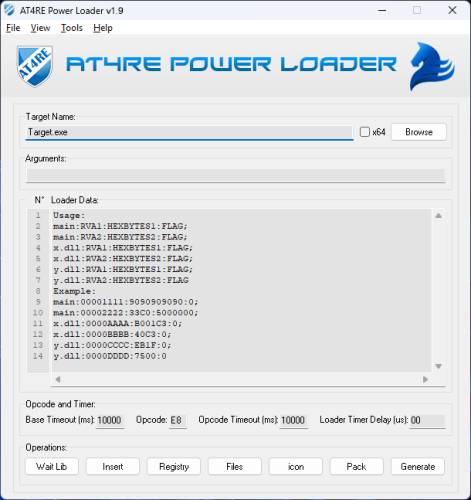
AT4RE Power Loader
 10 points
10 points- 800 downloads
- Version v1.9
============================ AT4RE Power Loader v0.1 (Release Date: 26/03/2025) ============================ [+] Console interface [+] Loader Coded in C++ with CRT (big Size: 85 KB when compressed about 190 KB uncompressed). [+] Supports patching single or multiple Relative Virtual Addresses (RVAs). Root Folder Contents: [+] ATPL.EXE (AT4RE Power Loader) [+] Version History.txt ============================ AT4RE Power Loader v0.2 (Release Date: 16/04/2025) ============================ The most powerful loader against strong and hard protectors. It also works with medium-level protectors, packers, compressors, and even unprotected executable files. Main Features: [+] GUI Coded in Borland Delphi 7 [+] From the GUI, you can browse to select the target file (maximum filename length is 255 characters). [+] You can also copy and paste the file name into the input field. [+] Choose between x32 and x64 loader versions. [+] Loader data can be entered only in the format shown in filed or in the screenshot. [+] Set a base timeout in milliseconds (Minimum: 00, Maximum: 9999 — i.e., 9.99 seconds). [+] Set 1-byte opcodes in the Opcode field using HEX characters (Opcode is the Original First Byte of RVA1). [+] Configure Opcode Timeout in milliseconds (Minimum: 00, Maximum: 9999 — i.e., 9.99 seconds). [+] Set the Loader Timer Delay in microseconds (Min: 00, Max: 9,999,999 — i.e., 9.99 seconds). [+] Configure the loader to start as Administrator. [+] Directly pack the loader with UPX. [+] Generate Loader.exe [+] Save or open projects for future use from File menu. [+] Set the GUI to "most on top" from the View menu. [+] Access the official website, report bugs, and find more information via about in the Help menu. Loader Details: [+] Coded in C++ using the Windows Pure API. [+] Loader size is 10 KB uncompressed, and 5 KB when compressed. [+] Supports Windows 7, 8, 10, and 11 (both x32 and x64). Features include: [+] Anti-ASLR [+] Anti-Anti-Debug [+] Anti-CRC Check [+] Automatically detects the base address. [+] Detects when the protector unpacks code into memory. [+] Can apply temporary patches after a specified delay in microseconds (Patch and restor original bytes). [+] Can apply permanent patches only with 00 Flag [+] Supports patching single or multiple Relative Virtual Addresses (RVAs). [+] Capable of patching up to 2048 bytes. [+] Can run as Administrator or Normal user mode. Root Folder Contents: [+] Project folder (Save or open projects for future use) [+] UPX folder (includes upx32.exe and upx64.exe) [+] ATPL.EXE (AT4RE Power Loader) [+] Version History.txt ============================ AT4RE Power Loader v0.3 (Release Date: 10/05/2025) ============================ The most powerful loader against strong and hard protectors. It also works with medium-level protectors, packers, compressors, and even unprotected executable files. Main Features: [+] Added Support Patching DLLs (Only DLLs Loaded by Target.exe). [+] Added Drag Drop Feature: For .EXE, .REG, .ICO Files. [+] Added Insert Loader Data feature (For Respect the Correct Format). [+] Added Registry Keys Manager (Max size: 1 KB / 1024 characters). [+] Added Delete Files feature (Max size: 1 KB / 1024 characters). [+] Added Icon Changer. [+] Added New Project option from File menu (Clears all fields). [+] Added Commands Shortcut Ctrl+N, Ctrl+O, Ctrl+S in File menu. [+] Added Contact Us section from Help menu. [+] Updated About from Help menu from box to a form. [+] Updated display fonts for Loader Data, Registry, and Files. [-] Removed "My Target run as admin". Loader Details: [+] Size is now 17 KB uncompressed, 7 KB when compressed. [+] Loader now Support Patching DLLs (Only DLLs Loaded by Target.exe). [+] Loader can now add or delete registry keys. [+] Loader can delete files. [+] Automatically requests Run as Administrator when needed (e.g.,Target need administrator privilege, modifying registry or deleting files from protected folders). [+] Icon support added. Root Folder Contents: [+] Icons folder (includes 5 icons). [+] Lib folder (includes bass.dll). [+] Project folder (Save or open projects for future use). [+] ResH folder (includes ResHacker.exe). [+] UPX folder (includes upx32.exe and upx64.exe). [+] ATPL.EXE (AT4RE Power Loader). [+] Version History.txt ============================ AT4RE Power Loader v0.4 (Release Date: 16/05/2025) ============================ The most powerful loader against strong and hard protectors. It also works with medium-level protectors, packers, compressors, and even unprotected executable files. Main Features: [+] Added Import menu. [+] Added Support .1337 patch files exported by x64dbg. [+] Set Opcode automatically when Load .1337 file. [+] Added OpenDialog when Double Click on: - Target Name field. - Loader Data field. - Registry field. - Custom icon field. Loader Details: [+] Fixed bug with registry feature. [+] Default icon changed. [+] Compressed Loader with Default icon 8 KB. Root Folder Contents: [+] Icons folder (includes 5 icons). [+] Lib folder (includes bass.dll). [+] Project folder (Save or open projects for future use). [+] ResH folder (includes ResHacker.exe). [+] UPX folder (includes upx32.exe and upx64.exe). [+] ATPL.EXE (AT4RE Power Loader). [+] Version History.txt10 points -
TitanHide
 10 pointsTitanHide has been updated to support the latest VMProtect v3.9.4 changes. The service name is now used as the device name, as well, so the check for \\.\TitanHide will fail if you name the service the differently. Latest version (v0019) download link10 points
10 pointsTitanHide has been updated to support the latest VMProtect v3.9.4 changes. The service name is now used as the device name, as well, so the check for \\.\TitanHide will fail if you name the service the differently. Latest version (v0019) download link10 points -
Lena's Reversing for Newbies
 9 points
9 points- 86,947 downloads
A collection of tutorials aimed particularly for newbie reverse engineers. 01. Olly + assembler + patching a basic reverseme 02. Keyfiling the reverseme + assembler 03. Basic nag removal + header problems 04. Basic + aesthetic patching 05. Comparing on changes in cond jumps, animate over/in, breakpoints 06. "The plain stupid patching method", searching for textstrings 07. Intermediate level patching, Kanal in PEiD 08. Debugging with W32Dasm, RVA, VA and offset, using LordPE as a hexeditor 09. Explaining the Visual Basic concept, introduction to SmartCheck and configuration 10. Continued reversing techniques in VB, use of decompilers and a basic anti-anti-trick 11. Intermediate patching using Olly's "pane window" 12. Guiding a program by multiple patching. 13. The use of API's in software, avoiding doublechecking tricks 14. More difficult schemes and an introduction to inline patching 15. How to study behaviour in the code, continued inlining using a pointer 16. Reversing using resources 17. Insights and practice in basic (self)keygenning 18. Diversion code, encryption/decryption, selfmodifying code and polymorphism 19. Debugger detected and anti-anti-techniques 20. Packers and protectors : an introduction 21. Imports rebuilding 22. API Redirection 23. Stolen bytes 24. Patching at runtime using loaders from lena151 original 25. Continued patching at runtime & unpacking armadillo standard protection 26. Machine specific loaders, unpacking & debugging armadillo 27. tElock + advanced patching 28. Bypassing & killing server checks 29. Killing & inlining a more difficult server check 30. SFX, Run Trace & more advanced string searching 31. Delphi in Olly & DeDe 32. Author tricks, HIEW & approaches in inline patching 33. The FPU, integrity checks & loader versus patcher 34. Reversing techniques in packed software & a S&R loader for ASProtect 35. Inlining inside polymorphic code 36. Keygenning 37. In-depth unpacking & anti-anti-debugging a combination packer / protector 38. Unpacking continued & debugger detection by DLL's and TLS 39. Inlining a blowfish scheme in a packed & CRC protected dll + unpacking Asprotect SKE 2.2 40. Obfuscation and algorithm hiding9 points -
[Technical Paper] GanDiao.sys (ancient kernel driver based malware)
 Hi all, this is my analysis of GanDiao.sys, an ancient kernel driver based malware. It only works in WinXP as it is unsigned. This driver was used by various malware families and it allowed any userland application to kill other protected processes. This doc also includes a custom userland app source code to use GanDiao and test its capabilities. ENGLiSH VERSiON: http://lucadamico.dev/papers/malware_analysis/GanDiao.pdf iTALiAN VERSiON: https://www.lucadamico.dev/papers/malware_analysis/GanDiao_ITA.pdf As usual, I'm also attaching both PDF files here, just in case. Enjoy. GanDiao.pdf GanDiao_ITA.pdf8 points
Hi all, this is my analysis of GanDiao.sys, an ancient kernel driver based malware. It only works in WinXP as it is unsigned. This driver was used by various malware families and it allowed any userland application to kill other protected processes. This doc also includes a custom userland app source code to use GanDiao and test its capabilities. ENGLiSH VERSiON: http://lucadamico.dev/papers/malware_analysis/GanDiao.pdf iTALiAN VERSiON: https://www.lucadamico.dev/papers/malware_analysis/GanDiao_ITA.pdf As usual, I'm also attaching both PDF files here, just in case. Enjoy. GanDiao.pdf GanDiao_ITA.pdf8 points -
Prometheus (12 Layers of Insanity)
 7 pointsThrew this into Binary Ninja, turned out to be Rust-compiled ELF64 PIE not C as DiE claims, debug strings like src/main.rs src/vm/dispatcher.rs src/crypto/sbox.rs give it away, main at 0x41bea0 is just the lang_start trampoline real logic sits in sub_41a0c0 which drops into the verification orchestrator sub_418a10 running all 12 layers with bitwise AND accumulation no early exits, layers 1-3 are RDTSC delta and clock_gettime CLOCK_MONOTONIC anti-debug gates, 4-5-6 enforce the 28-char [A-Z0-9_] format with underscores pinned at positions 10/15/23 last 4 digits only and ASCII sum exactly 1901, identified the core hash at sub_433b80 as SipHash-2-4 from the init vectors 0x736f6d6570736575 0x646f72616e646f6d 0x6c7967656e657261 0x7465646279746573 aka "somepseudorandomlygeneratedbytes" with rotation constants 13/32/16/21/17/32 two rounds per block four at finalization, the actual crack comes from Layer 10 which splits the key into four 7-byte segments each hashed with independent k0/k1 pairs reducing the search space from 36^24 down to 4x36^6 roughly 2^33 which is the single architectural weakness in the design, brute-forced the last 4 digits first against Layer 6s YEARHASH/KEY01020 keys in 10K iterations got 2026 then segment 4 in 1.3K then segments 2 and 3 each in ~2.2B iterations then segment 1 with sum-constraint pruning total 55 seconds single core, validated against all remaining layers including the full-key SipHash triplet layers 7/8/9 with three different key pairs and the polynomial evaluation through MurmurHash3 fmix64 at five prime evaluation points all passed clean, key is PR0M3TH3U5_F1R3_ST34L3R_2026, I have a full writeup sitting around too lazy to format it properly but if anyone wants I can publish it7 points
7 pointsThrew this into Binary Ninja, turned out to be Rust-compiled ELF64 PIE not C as DiE claims, debug strings like src/main.rs src/vm/dispatcher.rs src/crypto/sbox.rs give it away, main at 0x41bea0 is just the lang_start trampoline real logic sits in sub_41a0c0 which drops into the verification orchestrator sub_418a10 running all 12 layers with bitwise AND accumulation no early exits, layers 1-3 are RDTSC delta and clock_gettime CLOCK_MONOTONIC anti-debug gates, 4-5-6 enforce the 28-char [A-Z0-9_] format with underscores pinned at positions 10/15/23 last 4 digits only and ASCII sum exactly 1901, identified the core hash at sub_433b80 as SipHash-2-4 from the init vectors 0x736f6d6570736575 0x646f72616e646f6d 0x6c7967656e657261 0x7465646279746573 aka "somepseudorandomlygeneratedbytes" with rotation constants 13/32/16/21/17/32 two rounds per block four at finalization, the actual crack comes from Layer 10 which splits the key into four 7-byte segments each hashed with independent k0/k1 pairs reducing the search space from 36^24 down to 4x36^6 roughly 2^33 which is the single architectural weakness in the design, brute-forced the last 4 digits first against Layer 6s YEARHASH/KEY01020 keys in 10K iterations got 2026 then segment 4 in 1.3K then segments 2 and 3 each in ~2.2B iterations then segment 1 with sum-constraint pruning total 55 seconds single core, validated against all remaining layers including the full-key SipHash triplet layers 7/8/9 with three different key pairs and the polynomial evaluation through MurmurHash3 fmix64 at five prime evaluation points all passed clean, key is PR0M3TH3U5_F1R3_ST34L3R_2026, I have a full writeup sitting around too lazy to format it properly but if anyone wants I can publish it7 points -
Flare-On 12
 7 pointsIt's that time of the year again. It seems we're starting September 26 8PM EST again with a return to Web3 and YARA as well. Four weeks instead of six this year... I wonder what the reason for this is. 🤔 https://flare-on.com/7 points
7 pointsIt's that time of the year again. It seems we're starting September 26 8PM EST again with a return to Web3 and YARA as well. Four weeks instead of six this year... I wonder what the reason for this is. 🤔 https://flare-on.com/7 points -
Reverse Engineering Denuvo in Hogwarts Legacy
 Reverse Engineering Denuvo in Hogwarts Legacy Slides Sogen Emulator Source Ted.7 points
Reverse Engineering Denuvo in Hogwarts Legacy Slides Sogen Emulator Source Ted.7 points -
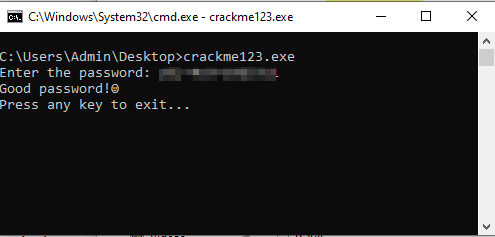
crackme123
 7 pointsYour crackme seems to have multiple solutions. Not sure if this was intended: Some example passwords: Approach:7 points
7 pointsYour crackme seems to have multiple solutions. Not sure if this was intended: Some example passwords: Approach:7 points -
VMProtect HWID CrackMe
 6 pointsHey guys! I’m iced, a passionate student from Bosnia who’s really into reverse engineering. I decided to join Tuts4You to expand my knowledge and trade insights with people who are way better than me.Im also a friend of @0xret2win and he suggested me to join site and try to tackle couple of nice crackmes posted here. Also i dont think the guy who made this applied full protection settings. Anyways upon investigating this target i found two interesting calls: ( Not entierly sure if i should do step-by-step since if you follow "MessageBoxA" in ret and stack you will eventually get to same place i got ) "vmp-licensing-test.vmp.exe"+A19CAE - E8 B9CB60FF - call "vmp-licensing-test.vmp.exe"+2686C This is upon hitting "VMProtectGetCurrentHWID". RAX => 29 "vmp-licensing-test.vmp.exe"+A19C9C - E8 2550ABFF - call "vmp-licensing-test.vmp.exe"+4CECC6 This is upon hitting on "VMProtectSetSerialNumber". RAX => 20 Using x64dbg : 00007FF665759CAE | E8 B9CB60FF | call vmp-licensing-test.vmp.7FF664D6686C | -> VMProtectGetCurrentHWID 00007FF665759C9C | E8 2550ABFF | call vmp-licensing-test.vmp.7FF66520ECC6 | -> VMProtectSetSerialNumber6 points
6 pointsHey guys! I’m iced, a passionate student from Bosnia who’s really into reverse engineering. I decided to join Tuts4You to expand my knowledge and trade insights with people who are way better than me.Im also a friend of @0xret2win and he suggested me to join site and try to tackle couple of nice crackmes posted here. Also i dont think the guy who made this applied full protection settings. Anyways upon investigating this target i found two interesting calls: ( Not entierly sure if i should do step-by-step since if you follow "MessageBoxA" in ret and stack you will eventually get to same place i got ) "vmp-licensing-test.vmp.exe"+A19CAE - E8 B9CB60FF - call "vmp-licensing-test.vmp.exe"+2686C This is upon hitting "VMProtectGetCurrentHWID". RAX => 29 "vmp-licensing-test.vmp.exe"+A19C9C - E8 2550ABFF - call "vmp-licensing-test.vmp.exe"+4CECC6 This is upon hitting on "VMProtectSetSerialNumber". RAX => 20 Using x64dbg : 00007FF665759CAE | E8 B9CB60FF | call vmp-licensing-test.vmp.7FF664D6686C | -> VMProtectGetCurrentHWID 00007FF665759C9C | E8 2550ABFF | call vmp-licensing-test.vmp.7FF66520ECC6 | -> VMProtectSetSerialNumber6 points -
AT4RE Power Loader
 6 pointsThe tool created with love for all RCE community. If you have any feedback bug repport share it here...6 points
6 pointsThe tool created with love for all RCE community. If you have any feedback bug repport share it here...6 points -
Polymorphic Parasite (x86) WriteUp
6 pointsi may banter a lil in the opening, but that is how i was taught when i was in highschool learning ASM from the ukranians and russians, bootkits from the chinese You give a short shoutout or point to be made and ya write and code Here, i use the LCRN (LCG) from the GiantBlack Book of Viruses (Physicist Dr. Mark Ludwig) and his 16-bit many hoops and recreated it for x86 (32 bit) VXWriteUp.pdf6 points
-
WinLicense v3.2.2 (Window Function Through an External Plugin)
Among the anti-debug techniques, there's an interesting one worth noting. A dummy thread is created and then it calls Sleep(0x32). (The goal is for the created thread to be detected by tools like x64dbg.) Then, it calls NtQueryObject with the ObjectBasicInformation class using the thread handle. If the returned HandleCount is greater than 1, it determines that debugging is in progress. void dummy() { Sleep(8000); } bool CheckCreateThreadHandleCount() { HANDLE hThread = CreateThread(NULL, 0, (LPTHREAD_START_ROUTINE)dummy, NULL, 0, NULL); if (hThread == NULL) { return false; } Sleep(0x32); PUBLIC_OBJECT_BASIC_INFORMATION objInfo; NTSTATUS status = NtQueryObject(hThread, ObjectBasicInformation, &objInfo, sizeof(objInfo), NULL); if (!NT_SUCCESS(status)) { CloseHandle(hThread); return false; } std::cout << "Handle Count: " << objInfo.HandleCount << std::endl; if (objInfo.HandleCount > 1) { CloseHandle(hThread); return true; } CloseHandle(hThread); return false; }6 points
-
.NET KeyGenMe by Freddy #1
6 pointsSince @Washi provided the solution first, you may mark his answer as solved. However, I’d like to share my approach as well for reference. 1) Polynomial Coefficients and Matrix 1. Username - Polynomial Coeffs The code has a function that folds ASCII values into 8 coefficients ( size = 7 ). For "CHESSKING" , we take each character's ASCII and add it to slot in the array. 2. Matrix Build We then build 5 x 5 integer matrix from these 7 coefficients. Each entry is computed via this formula : mat(r,c) = ( coeffs ( r mod 7 ) x ( c + 1)) + ( r + 1 ) ---> All in paranthesses from start has to be to the power of 2. 3. Determinant ( mod 65521 ) We do a row-reduction to find the matrix's determinant, and then take /bmod 65521. 2) Toy Elliptic-Curve Step The code defines a small curve: y2 ≡ x3 +Ax+B (modp), p=1201, A=1,B =1. ( x3 here is actually x to the power of 3 ) We have a base point G = ( 5,116 ) this goes : finalPoint= ECSM (G,detMod) That is, we "add" G to itself ( detMod ) times in elliptic-curve arithmetic. The result is ( X , Y ) . Then we define it with this formula : curveSecret= X+ (Y≪16) 3) LFSR Shuffle We take 64 bits (lowest bits) from curveSecret and feed them into a Linear Feedback Shift Register for 64 rounds, producing a new 64-bit integer lfsrOutput. This step effectively scrambles the bits further. 4) BFS-Based Knight Path The code starts at square E5 on a 10×10 board labeled A..J (files) and 1..10 (ranks). Internally, E5 is (4,4) in 0-based coordinates. For each character in the username, we do: steps= (ASCII of char) mod 5 , then run a BFS for that many expansions. The BFS uses Knight moves (like (2,1), (1,2), etc.) with wrapping if we go off the board. We capture the last enqueued square after those BFS expansions, add that to our path, and repeat for the next character in the username. 5) “Check to the King” There is a King placed on G10 → (6,9) in 0-based coordinates. We look at the final square in our BFS path. If that final square is one knight’s move away from (6,9), we do an extra step: lfsrOutput = lfsrOutput⊕0xA5A5A5A5 For "CHESSKING" , the BFS path’s last square does or does not cause this XOR. In our run, it does cause the XOR (i.e., it’s in position to “check the King”). 6) Nibble → Weird SAN Moves We take the final integer (lfsrOutput) and break it into 12 consecutive 4-bit nibbles. For each nibble, we pick a “weird” standard algebraic notation (SAN) chess move from the code’s move table. This yields moves like e2e4, Na3xb5, Qd1h5, etc. 7) Final Serial Part A: The BFS squares (space-separated). A dash ( - ) Part B: The 12 SAN moves from the nibble-based table. Verifying everythin we gathered so far : For "CHESSKING" : E5 I3 C1 A7 G4 C1 C1 I8 E5 G4 After the code determines the King is in check, it XORs the LFSR output with 0xA5A5A5A5 Extract 12 nibbles → map to the weird SAN table. They all turned out to be mostly e2e4, with a couple of different ones in the middle (Bf1c4, d2d4) My final answer which is my Username and Serial Key is :6 points
-
Compiling Unlicense
 5 pointsThis is a very bad thing to add! Grabbing this personal information from a user without mentioning that is a terrible act to do !! Now you have ip @ of @CodeExplorer did you ask him if he agreed to that or not?? No! So that's why everyone must run any garbage from the internet on an isolated machine!5 points
5 pointsThis is a very bad thing to add! Grabbing this personal information from a user without mentioning that is a terrible act to do !! Now you have ip @ of @CodeExplorer did you ask him if he agreed to that or not?? No! So that's why everyone must run any garbage from the internet on an isolated machine!5 points -
.NET Reactor v7.3 (Embedded DLL's)
 5 pointsHere is unpacked folder, all tools included. https://limewire.com/d/PWsfv#C32mVemS40 https://fileroy.com/2WVGr1E9zkx7/file https://zippyshare.day/YPGm89uDHMSpeoC/file Final unpacked exe is called drr_msil_Slayed2cleaned_.exe5 points
5 pointsHere is unpacked folder, all tools included. https://limewire.com/d/PWsfv#C32mVemS40 https://fileroy.com/2WVGr1E9zkx7/file https://zippyshare.day/YPGm89uDHMSpeoC/file Final unpacked exe is called drr_msil_Slayed2cleaned_.exe5 points -
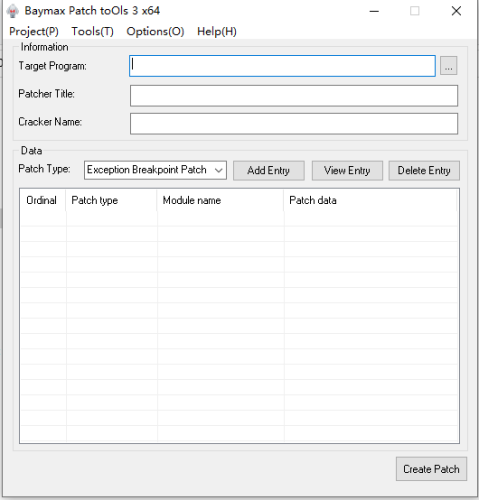
Baymax Patch toOls
 5 points2025.10.15 — x86/x64 v3.5.1.3 1.Patch customization: added a batch of hijack DLLs and you can configure hijack modules on the "Custom Patch Settings" page. Patches can now bundle custom files — non-PE files will be extracted to the target directory together with the patch, while other files can be optionally extracted. Patch data in the cracking modules PYG/PYG64 now supports dynamic expansion. 2.Added a small utility: “Process Hijack DLL Detector” — provides a closed loop from detecting usable hijack DLLs → generating a hijack DLL project → adding that custom hijack module into a patch. 3.The hijack code generator is now compatible with the latest VS2022; fixed intermediate directory settings. 4.When the patch logo popup is closed, the target application's main window is brought to the foreground. 5.The main program now generates a dump file when it crashes. 6.Fixed compatibility issues with VMP 3.x and several bugs — thanks to csjwaman and 真小白 for their bug reports. 7.Added tooltip (tip bubble) support on UI controls so full text can be displayed. 8.Thanks to KuNgBiM and 红豆 for providing multilingual files and proofreading copy. 9.Improved data protection, compatibility, and anti-debugging; thanks to kxoe for the suggestions. 10.Minor UX/details optimizations in the main program — for example, improved prompts when saving bpt projects. Baymax Patch Tools v3.5.1.3.zip Baymax Patch Tools x64 v3.5.1.3.zip Baymax toOls for x64dbg v1.9.5 1. Add replacement function for search data 2. Add feature code option with real-time effect 3. Add more language files Baymax toOls for x64dbg v1.9.5.zip5 points
5 points2025.10.15 — x86/x64 v3.5.1.3 1.Patch customization: added a batch of hijack DLLs and you can configure hijack modules on the "Custom Patch Settings" page. Patches can now bundle custom files — non-PE files will be extracted to the target directory together with the patch, while other files can be optionally extracted. Patch data in the cracking modules PYG/PYG64 now supports dynamic expansion. 2.Added a small utility: “Process Hijack DLL Detector” — provides a closed loop from detecting usable hijack DLLs → generating a hijack DLL project → adding that custom hijack module into a patch. 3.The hijack code generator is now compatible with the latest VS2022; fixed intermediate directory settings. 4.When the patch logo popup is closed, the target application's main window is brought to the foreground. 5.The main program now generates a dump file when it crashes. 6.Fixed compatibility issues with VMP 3.x and several bugs — thanks to csjwaman and 真小白 for their bug reports. 7.Added tooltip (tip bubble) support on UI controls so full text can be displayed. 8.Thanks to KuNgBiM and 红豆 for providing multilingual files and proofreading copy. 9.Improved data protection, compatibility, and anti-debugging; thanks to kxoe for the suggestions. 10.Minor UX/details optimizations in the main program — for example, improved prompts when saving bpt projects. Baymax Patch Tools v3.5.1.3.zip Baymax Patch Tools x64 v3.5.1.3.zip Baymax toOls for x64dbg v1.9.5 1. Add replacement function for search data 2. Add feature code option with real-time effect 3. Add more language files Baymax toOls for x64dbg v1.9.5.zip5 points -
Need some Tips for this keygen template I made
I commented out that portion of code because transparency works correctly, but if you look closely, it generates artifacts, especially when selecting text. However, I solved the problem just last night by looking at some templates on the forum in asm x86 and making the appropriate changes. Below, I show all the updated code. In attachment you will find image resource and the exe file. #include <windows.h> #include <wingdi.h> #include "ufmod.h" #include "resource.h" #include "song.h" #pragma comment(lib, "Msimg32.lib") #pragma comment(lib, "ufmod.lib") #pragma comment(lib, "winmm.lib") HINSTANCE hInst; HBITMAP hBackground = NULL; HBRUSH hBrushBackground = NULL; HBRUSH hBrush; COLORREF transparentColor = RGB(255, 0, 255); // Magenta color key // Bitmap per il pulsante di chiusura HBITMAP hBtnCloseNormal = NULL; HBITMAP hBtnCloseHover = NULL; // Procedura finestra del dialogo INT_PTR CALLBACK DialogProc(HWND hwndDlg, UINT uMsg, WPARAM wParam, LPARAM lParam) { switch (uMsg) { case WM_INITDIALOG: { HICON hIcon = LoadIcon(hInst, MAKEINTRESOURCE(IDI_ICON1)); SendMessage(hwndDlg, WM_SETICON, ICON_BIG, (LPARAM)hIcon); SetWindowText(hwndDlg, L"Keygen Template by jNe"); // Imposta il testo predefinito SetDlgItemText(hwndDlg, EDIT_username, L"Enter Username"); // play chip-tune <3 uFMOD_SetVolume(20); uFMOD_PlaySong(songData, (void*)sizeof(songData), XM_MEMORY); // BMP in background hBackground = LoadBitmap(GetModuleHandle(NULL), MAKEINTRESOURCE(BMP_form)); hBrush = CreatePatternBrush(hBackground); // set magenta color key SetLayeredWindowAttributes(hwndDlg, transparentColor, 0, LWA_COLORKEY); // --- FINE --- // BMP close hBtnCloseNormal = LoadBitmap(GetModuleHandle(NULL), MAKEINTRESOURCE(BMP_close)); hBtnCloseHover = LoadBitmap(GetModuleHandle(NULL), MAKEINTRESOURCE(BMP_close_hover)); if (hBtnCloseNormal) { HWND hBtnClose = GetDlgItem(hwndDlg, BTN_CLOSE); if (hBtnClose) { BITMAP bm; GetObject(hBtnCloseNormal, sizeof(bm), &bm); SetWindowPos(hBtnClose, NULL, 0, 0, bm.bmWidth, bm.bmHeight, SWP_NOMOVE | SWP_NOZORDER); } } } return TRUE; case WM_ERASEBKGND: return TRUE; case WM_PAINT: { PAINTSTRUCT ps; HDC hdc = BeginPaint(hwndDlg, &ps); if (hBackground) { HDC hdcMem = CreateCompatibleDC(hdc); HBITMAP hOldBmp = (HBITMAP)SelectObject(hdcMem, hBackground); BITMAP bm; GetObject(hBackground, sizeof(bm), &bm); BitBlt(hdc, 0, 0, bm.bmWidth, bm.bmHeight, hdcMem, 0, 0, SRCCOPY); SelectObject(hdcMem, hOldBmp); DeleteDC(hdcMem); } EndPaint(hwndDlg, &ps); } return TRUE; case WM_DRAWITEM: { LPDRAWITEMSTRUCT lpdis = (LPDRAWITEMSTRUCT)lParam; if (lpdis->CtlID == BTN_CLOSE) { HDC hdcMem = CreateCompatibleDC(lpdis->hDC); HBITMAP hBmpToUse; if (lpdis->itemState & ODS_SELECTED) { hBmpToUse = hBtnCloseHover; // HOVER } else { hBmpToUse = hBtnCloseNormal; // NORMAL } if (hBmpToUse) { HBITMAP hOldBmp = (HBITMAP)SelectObject(hdcMem, hBmpToUse); BitBlt(lpdis->hDC, lpdis->rcItem.left, lpdis->rcItem.top, lpdis->rcItem.right - lpdis->rcItem.left, lpdis->rcItem.bottom - lpdis->rcItem.top, hdcMem, 0, 0, SRCCOPY); SelectObject(hdcMem, hOldBmp); } DeleteDC(hdcMem); } } return TRUE; case WM_CTLCOLORDLG: return (INT_PTR)hBrush; case WM_CTLCOLOREDIT: case WM_CTLCOLORSTATIC: { HDC hdcEdit = (HDC)wParam; int controlId = GetDlgCtrlID((HWND)lParam); if (controlId == ABOUT) { SetBkMode(hdcEdit, TRANSPARENT); SetTextColor(hdcEdit, RGB(255, 255, 255)); SetBkColor(hdcEdit, 0x00000000); SetBrushOrgEx(hdcEdit, -23, -88, NULL); return (INT_PTR)hBrush; } if (controlId == EDIT_username) { SetBkMode(hdcEdit, TRANSPARENT); SetTextColor(hdcEdit, RGB(255, 255, 255)); SetBkColor(hdcEdit, 0x00000000); SetBrushOrgEx(hdcEdit, -23, -88, NULL); return (INT_PTR)hBrush; } if (controlId == EDIT_serial) { SetBkMode(hdcEdit, TRANSPARENT); SetTextColor(hdcEdit, RGB(255, 255, 255)); SetBkColor(hdcEdit, 0x00000000); SetBrushOrgEx(hdcEdit, -23, -151, NULL); return (INT_PTR)hBrush; } break; } case WM_LBUTTONDOWN: SendMessage(hwndDlg, WM_NCLBUTTONDOWN, HTCAPTION, 0); return TRUE; case WM_COMMAND: switch (LOWORD(wParam)) { case EDIT_username: { if (HIWORD(wParam) == EN_CHANGE) { char username[256]; GetDlgItemTextA(hwndDlg, EDIT_username, username, 256); SetDlgItemTextA(hwndDlg, EDIT_serial, "OMFG-THIS-IS-A-DEMO"); } break; } case BTN_CLOSE: SendMessage(hwndDlg, WM_CLOSE, 0, 0); return TRUE; } break; case WM_CLOSE: uFMOD_StopSong(); if (hBrush) DeleteObject(hBrush); if (hBackground) DeleteObject(hBackground); if (hBtnCloseNormal) DeleteObject(hBtnCloseNormal); if (hBtnCloseHover) DeleteObject(hBtnCloseHover); EndDialog(hwndDlg, 0); return FALSE; } return FALSE; } // Entry point int WINAPI WinMain(HINSTANCE hInstance, HINSTANCE hPrevInstance, LPSTR lpCmdLine, int nCmdShow) { hInst = hInstance; DialogBox(hInstance, MAKEINTRESOURCE(IDD_DIALOG1), NULL, DialogProc); return 0; } keygen template - fix.zip5 points
-
kill a process and prevent it from being created again
 Hi @LCF-AT , DriverMonitor is an old tool that has been released for over 20 years. I am accustomed to using this app to load some Windows drivers. For learning and testing purposes, I used some leaked certificates to sign this driver. Now I will upload the signed driver here. I have set up a callback function (ProcessNotifyExRoutine_call_back) in the driver to filter specific process names in order to prevent their loading. Therefore, before uninstalling the driver, the target process cannot be started. This simple APP can kill some driver-protected antivirus software or system-level processes. For example, antivirus software such as Kaspersky and Symantec. If you terminate the system processes (e.g. winlogon.exe and dwm.exe), it will result in a BSOD. bin_v0.002.zip(Requires: 64-bit OS & >= Windows 7) DriverMonitor_EN.rar Video_2025-09-14_161309.mp4 (4.69 MB)5 points
Hi @LCF-AT , DriverMonitor is an old tool that has been released for over 20 years. I am accustomed to using this app to load some Windows drivers. For learning and testing purposes, I used some leaked certificates to sign this driver. Now I will upload the signed driver here. I have set up a callback function (ProcessNotifyExRoutine_call_back) in the driver to filter specific process names in order to prevent their loading. Therefore, before uninstalling the driver, the target process cannot be started. This simple APP can kill some driver-protected antivirus software or system-level processes. For example, antivirus software such as Kaspersky and Symantec. If you terminate the system processes (e.g. winlogon.exe and dwm.exe), it will result in a BSOD. bin_v0.002.zip(Requires: 64-bit OS & >= Windows 7) DriverMonitor_EN.rar Video_2025-09-14_161309.mp4 (4.69 MB)5 points -
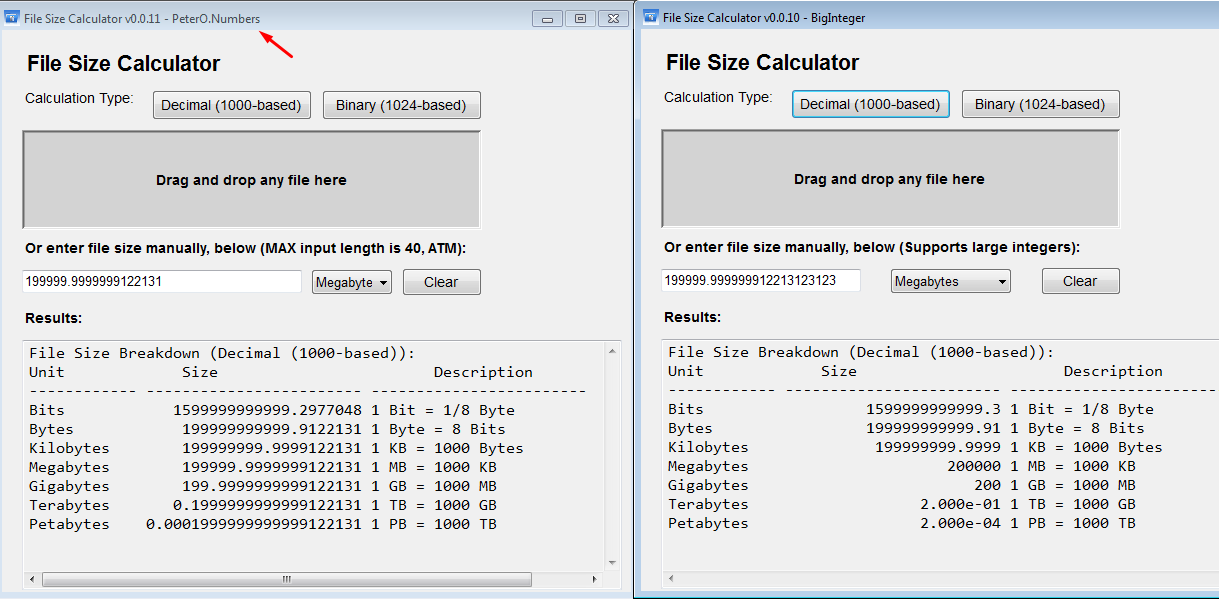
Do you know any file size info & calculation tools?
damn it! this is GENIOUS! (instead of WinAPI old dirty crap!!!) easy! just read the docs :) built a binary using that multi-precision lib: (left vs last build fom @Stuttered ) FileSizeCALC_0.0.11.zip5 points
-
VMProtect Heaven's Gate Anti-Debug Bypass to VectorHandler
 Here are the steps to get a completely modified version of x64dbg. Go to https://github.com/x64dbg/x64dbg Press this button in the top-right corner of your screen: You can then change the code to your liking (e.g., to bypass the anti-debug problem).5 points
Here are the steps to get a completely modified version of x64dbg. Go to https://github.com/x64dbg/x64dbg Press this button in the top-right corner of your screen: You can then change the code to your liking (e.g., to bypass the anti-debug problem).5 points -
VMProtect x64 v3.6 HWID Lock (All Protection Options)
 For some reason, when I press VMCode, nothing happens. No badboy or goodboy message. But for now, I’ve managed to get any key to register successfully. I’ll still take a look at the VMCode routine—just out of curiosity—and if I manage to figure it out, I’ll definitely write a tutorial. Btw whats up with your x86 with your anti-anti tricks? It wont even start on my machine for some reason. Could you please take a look at it?5 points
For some reason, when I press VMCode, nothing happens. No badboy or goodboy message. But for now, I’ve managed to get any key to register successfully. I’ll still take a look at the VMCode routine—just out of curiosity—and if I manage to figure it out, I’ll definitely write a tutorial. Btw whats up with your x86 with your anti-anti tricks? It wont even start on my machine for some reason. Could you please take a look at it?5 points -
Leaked VMProtect sources
 5 points...because cloning git repo, or just clicking on anonfiles.com_d1D7M7q9z4_vmpsrc.zip is so f*ing complicated. You don't need VMProtect sources. What you need is a basic understanding of this magical thing called "the internet".5 points
5 points...because cloning git repo, or just clicking on anonfiles.com_d1D7M7q9z4_vmpsrc.zip is so f*ing complicated. You don't need VMProtect sources. What you need is a basic understanding of this magical thing called "the internet".5 points -
help for macOs protector
 5 points
5 points -
Blackett
5 pointsHi! I took a look at it and shame that no one tried to solve it,here is my approach. Basic things i pulled: All four keys must differ. If any two keys are the same string, it shows “All keys must be different.” No key can contain "0@0". If you type a key like "0@0@something", it rejects it. “Erjey” can be used at most once, and if it appears, the fourth chunk of that key must be less than 6. That is, if a key has the substring "erjey", its format is X@Y@erjey@W, and W<6W < 6W<6. The third chunk in each key can be one of three strings: erjey kao tuts4you If you use something else, you get badboy error message. 2.2. Internally, a Linear Solver Digging deeper, i discovered a set of classes (d, e, j, etc.) that build a system of linear equations or inequalities. Each key of the form X@Y@{erjey|kao|tuts4you}@W is taken to mean X⋅x+Y⋅yRELWX , where the “relation” REL depends on the keyword: erjey → equality (=). kao → some inequality (≥ or ≤) depending on puzzle logic. tuts4you → the other inequality. From hints in the code and trial tests, we saw that: erjey is effectively “=”. For this puzzle’s code, kao ended up being “≥” and tuts4you was “≤” (the code flips them). Finally, after the solver ensures a feasible solution for (x, y), it calculates an “objective value” from the Name field, which must also be in the format A@B (two doubles). The code uses: objective=A×x+B×y If that objective is exactly 44 000, it shows: MessageBox.Show("Valid combination!"); That is the central condition: Ax+By=44000. 3. Constructing a Solution To guarantee the solver yields 44,000, we needed to pick (x, y) and (A,B) so that: A×x+B×y=44000. Additionally, we had exactly four constraints (the “Keys”) to pin down x and y. 3.1. The Simplest Trick: Set x=y One common approach: force x=y=c for some integer c < 6 (because the puzzle disallows “erjey@W” if W >= 6). Then we just need: (A+B)×c=44000 then this becomes A+B = 44000 / c Hence, pick any c in [1..5], and pick A + B = 44000 / c. 3.3. Example Name Then to satisfy (A+B) c=44000, choose a Name that splits as A@B with A+B=44000/c. For instance: Let c = 4. Then A+B must be 11000. We pick A = 5500 and B = 5500. So Name = "5500@5500". 3.4. Putting It All Together And if im right and if this is the keygen you have asked for : keygen.py5 points
-
practicing firmware reverse engineering, having trouble
 I was not able to download your firmware completely (Catbox seems to be having problems today) but I can give you some tips anyway. Step 1: It's unlikely that you've encountered a very unique hardware that has no existing tooling or documentation. Also a lot of hardware is made by the same OEM manufacturer in China and just sold under different brand names. So, use Google. Seriously. :) First few kilobytes of your firmware contain plenty of interesting and unique strings. Search for each one separately, or some combination of them. You're basically looking for the information about your hardware - CPU and system board manufacturer, addon boards, sensor information, and so on. You'll be amazed how much information a single search can provide. You could also search for the hardware make/model (which unfortunately you didn't tell us) or FCC ID. Step 2: Once you know the basic hardware information, use Google again. Look for tools and SDKs for the specific manufacturer/CPU. Use Google Translate to browse Chinese and Russian sites - they are a goldmine when it comes to hardware hacking and documentation. You should be able to find this github project. too. I didn't run the tool but a quick look at the source code tells me it should unpack your firmware with little to no modifications. Step 3: Load the unpacked firmware in Ghidra/IDA and start the actual reverse engineering process. :)4 points
I was not able to download your firmware completely (Catbox seems to be having problems today) but I can give you some tips anyway. Step 1: It's unlikely that you've encountered a very unique hardware that has no existing tooling or documentation. Also a lot of hardware is made by the same OEM manufacturer in China and just sold under different brand names. So, use Google. Seriously. :) First few kilobytes of your firmware contain plenty of interesting and unique strings. Search for each one separately, or some combination of them. You're basically looking for the information about your hardware - CPU and system board manufacturer, addon boards, sensor information, and so on. You'll be amazed how much information a single search can provide. You could also search for the hardware make/model (which unfortunately you didn't tell us) or FCC ID. Step 2: Once you know the basic hardware information, use Google again. Look for tools and SDKs for the specific manufacturer/CPU. Use Google Translate to browse Chinese and Russian sites - they are a goldmine when it comes to hardware hacking and documentation. You should be able to find this github project. too. I didn't run the tool but a quick look at the source code tells me it should unpack your firmware with little to no modifications. Step 3: Load the unpacked firmware in Ghidra/IDA and start the actual reverse engineering process. :)4 points -
crackmes.one CTF 2026
4 pointsThe crackmes.one CTF is officially live, built by the RE community, for the RE community. https://crackmesone.ctfd.io/ Start at: Sat 14 February 2026 00:00:00 UTC Enter the matrix and prove your skills. See you there!4 points
-
Prometheus (12 Layers of Insanity)
 4 pointsHello. I have organised it in two different formats. I also added the modified solver.c file as an extra. Thank you. Link: drive4 points
4 pointsHello. I have organised it in two different formats. I also added the modified solver.c file as an extra. Thank you. Link: drive4 points -
Themida v3.1.4 (x32 & x64) - Impossible
This one is an interesting sample. Code is really small, so it was stolen completely, thus it's hard to tell app code from protector code. Functional code is quite simple, just MessageBoxA. And that's it, it does nothing more. After showing the message box it starts freeing memory that definitely isn't app code. But for the sake of completeness let's get to the bottom of this. We have 8 more code bytes. And we have 1 reloc pointing there, meaning ExitProcess should perfectly fit in. Unpacked file attached with code, import and relocs restored and sections cut. unpacked.exe4 points
-
Themida & VMProtect (Same Virtualized Code Sections)
(1) I never accused you of lying (2) I don't care about your "tools" My point is crystal clear: this site will continue to die if we allow such "solutions" (which are 9/10 just people using public tooling and therefore can't provide any novel contributions). Go ahead, feel free to discuss the "internals", which was arguably the bare minimum you should have provided in the original response to this challenge.4 points
-
TX-02 Berkeley Mono Fontface
 4 pointsDear friends Berkeley Mono Font face is updated to version2. They included ligatures (nerd glyphs) directly in this build. The font face is 75$ for developer use only (no commercial use.) I have included this fontface so you can try them. Enjoy! Homepage hxxps://usgraphics[.]com/products/berkeley-mono Archive Pass: Download tx-02-berkeley-mono-pass=SCT.7z4 points
4 pointsDear friends Berkeley Mono Font face is updated to version2. They included ligatures (nerd glyphs) directly in this build. The font face is 75$ for developer use only (no commercial use.) I have included this fontface so you can try them. Enjoy! Homepage hxxps://usgraphics[.]com/products/berkeley-mono Archive Pass: Download tx-02-berkeley-mono-pass=SCT.7z4 points -
.NET Reactor v7.3 (Embedded DLL's)
 4 pointsHere we go, after the above step with slayer - Decrypt Methods unckecked; // Token: 0x0600081D RID: 2077 RVA: 0x0006E2E8 File Offset: 0x0006C4E8 [MethodImpl(MethodImplOptions.NoInlining)] internal unsafe static void qp1d5IbOJ() { Just fill at 006C4E8 with 062A so will change the body of method qp1d5IbOJ to a simple ret. after that we have a working file and we can deobfuscate with BabelDeobfuscator. Here is working unpacked file: https://workupload.com/file/3JqMck9ZtYR4 points
4 pointsHere we go, after the above step with slayer - Decrypt Methods unckecked; // Token: 0x0600081D RID: 2077 RVA: 0x0006E2E8 File Offset: 0x0006C4E8 [MethodImpl(MethodImplOptions.NoInlining)] internal unsafe static void qp1d5IbOJ() { Just fill at 006C4E8 with 062A so will change the body of method qp1d5IbOJ to a simple ret. after that we have a working file and we can deobfuscate with BabelDeobfuscator. Here is working unpacked file: https://workupload.com/file/3JqMck9ZtYR4 points -
StrongName tools - source code C#
 4 pointsStrongName tools: - added SamePKT tool - added 64 bits support for all tools StrongName2.rar4 points
4 pointsStrongName tools: - added SamePKT tool - added 64 bits support for all tools StrongName2.rar4 points -
Compiling Unlicense
4 pointsHere compiled unlicense with codeexplorer's fixes: unlicense compiled With pyton 3.09 and 3.11 versions.4 points
-
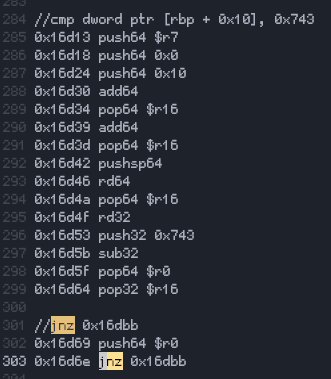
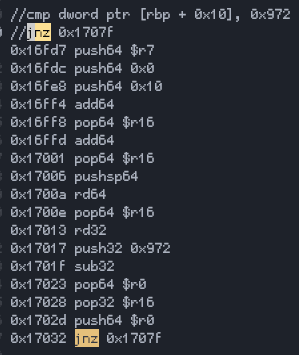
BinaryShield (Custom VM)
 4 pointsI wanted to devirtualize it manually so I made a disassembler for it using the new yara-x to locate the handlers and the bytecode. Probably going to turn it into a full devirtualizer from binaryshield bytecode straight to x86_64. I saw these values(the one in the cmp comment) put them as input since it was valid I didn't go further. You can find my work at https://github.com/xlatbx59/Bshld, the file with the disassembly is at https://github.com/xlatbx59/Bshld/blob/master/binshield.txt. It was fun to reverse4 points
4 pointsI wanted to devirtualize it manually so I made a disassembler for it using the new yara-x to locate the handlers and the bytecode. Probably going to turn it into a full devirtualizer from binaryshield bytecode straight to x86_64. I saw these values(the one in the cmp comment) put them as input since it was valid I didn't go further. You can find my work at https://github.com/xlatbx59/Bshld, the file with the disassembly is at https://github.com/xlatbx59/Bshld/blob/master/binshield.txt. It was fun to reverse4 points -
Compiling Unlicense
 4 pointsNo, the above script won't work due to Themida anti-debug tricks, even if program starts with the debugger. I got to say: Themida is great protector. Too bad about antivirus detections like https://www.malwarebytes.com/blog/detections/riskware-patcher-themida I made some new updates to Unlicense: - fixed winlicense v3 detection for the above https://storage.custos.dev/ResourceCryptor_latest.7z - fixed imports for winlicense v3 x64 OEP still needs to be fixed as currently stops before real OEP; You could try --force_oep: --force_oep=0x0115E 0x0115E = OEP rva; as long as you know OEP rva. unlicenseFixed2.rar4 points
4 pointsNo, the above script won't work due to Themida anti-debug tricks, even if program starts with the debugger. I got to say: Themida is great protector. Too bad about antivirus detections like https://www.malwarebytes.com/blog/detections/riskware-patcher-themida I made some new updates to Unlicense: - fixed winlicense v3 detection for the above https://storage.custos.dev/ResourceCryptor_latest.7z - fixed imports for winlicense v3 x64 OEP still needs to be fixed as currently stops before real OEP; You could try --force_oep: --force_oep=0x0115E 0x0115E = OEP rva; as long as you know OEP rva. unlicenseFixed2.rar4 points -
Nuitka 2.1.5 (Python 3.11)
4 pointsYou can look for HydraDragonAntivirus/AutoNuitkaDecompiler: Get malware payload without dynamic analysis with this auto decompiler or my main project. I did with that. If you want dynamic analysis then Is Nuitka No Longer Secure? A Reverse Engineering Tool for Nuitka/Cython-Packed Applications — pymodhook | by qfcy | Medium (There more advanced special python code for pymodhook but it's closed source for vxnet and not made by me so I can't make it public) If you want both dynamic and static: Siradankullanici/nuitka-helper: Symbol Recovery Tool for Nuitka Binaries I did extract with stage1.py or nuitka-extractor extremecoders-re/nuitka-extractor: Tool to extract nuitka compiled executables (or just do dynamic analysis for extract and sometimes it can't extract or Nuitka compiles executable as dll so you need dll loader It seems like it becoming obsolete · Issue #15 · extremecoders-re/nuitka-extractor) my main project not stable but if he is become stable then he can detect is he nuitka and do auto extract with auto decompile and you get source code. Nuitka is actually hiding data in resources section in specia bytecode format. Actual source code starts from (u)python.exe or /python.exe (generally in broken executables) then you need look for <modulecode part for import recovery and Nuitka compiles with everything for obfuscation. So too many comment lines from file exists. You can detect junks by that line contains no u word. Which means this line is junk because u means go to next line in Nuitka bytecode. Nuitka is not obfuscated if he doesn't compile with everything otherwise it's obfuscated. You can improve my script by looking Nuitka bytecode source code. You can post to ay AI to recover code but Gemini is currently best for very long codes. Compared to other obfuscators you need pyarmor with Nuitka to make him more secure (or guardshield with pip install guardshield), otherwise it's easy task if there no too many imports. Rarely user disables compile everything even if the docs then your task much easier but in default Nuitka compiles everything. Nuitka clearly worser than Rust for some reason. 1) Antiviruses flags as malware because malware analysts can't understand Nuitka (even if they are too experinced they really don't know how to solve Nuitka) so you get false positives. 2) It's not good obfuscator and it's not creating millions of line hello world code via normal cython. I don't recommend python to use for avoid reverse engineering but you can still use it. If you want I can give all details which I know with tutorial or I can release my main project for auto Nuitka decomplication. My last words are don't use pyoxidizer, pyinstaller, cx_freeze if you want obfuscate your code because Nuitka is still best open source option for python. Nuitka can't remove python.h so the code must be pseudo python (Cython like style)4 points
-
Do you know any file size info & calculation tools?
 Update v0.0.10. Thx @jackyjask for pointing to the BigNumber library and assist. See attached. FileSizeCALC_v0.0.10.rar4 points
Update v0.0.10. Thx @jackyjask for pointing to the BigNumber library and assist. See attached. FileSizeCALC_v0.0.10.rar4 points -
Board Update: Invision Community 5
 4 pointsThose with keen eyes may have already noticed there has been a change to the board, it has now been updated to Invision Community 5. If you see an issue somewhere please let me know and I'll have a look at fixing it up... Ted.4 points
4 pointsThose with keen eyes may have already noticed there has been a change to the board, it has now been updated to Invision Community 5. If you see an issue somewhere please let me know and I'll have a look at fixing it up... Ted.4 points -
Eazfuscator.NET v2025.01
 4 points
4 points -
de4dot deobfuscation problems
4 pointsIt is not hard to update dnlib, maybe 8/10 fixes on de4dot and it will work. Tomorrow I will share my updated de4dot-cex with you.4 points
-
AT4RE Power Loader
 4 points
4 points -
.NET Reactor v7.3 (Embedded DLL's)
 4 points
4 points -
.NET Reactor v7.3
 4 points> WindowsFormsApplication37_Slayed.exe!WindowsFormsApplication37.Internal.PolicyFinalizer.VisualContainerPolicy.CombineTransaction(WindowsFormsApplication37.Internal.PolicyFinalizer.ArgumentViewer instance) (IL=0x2260, Native=0x091A0040+0x6B85) case (PolicyFinalizer.NotificationCall)128: if (PolicyFinalizer.m_PolicySenderList.Count == 0) { Module module = typeof(PolicyFinalizer).Module; this.m_ClientEvaluator.IncludeManager(new PolicyFinalizer.PolicyFinder(module.ResolveString((int)this.m_CustomDecryptorPolicyObj | 1879048192))); return; } 70000000 metadataToken 0x7000174A int - metadataToken of good string: 0x700016DE but it is not easy as replacing a string- it is not working after changing string.4 points
4 points> WindowsFormsApplication37_Slayed.exe!WindowsFormsApplication37.Internal.PolicyFinalizer.VisualContainerPolicy.CombineTransaction(WindowsFormsApplication37.Internal.PolicyFinalizer.ArgumentViewer instance) (IL=0x2260, Native=0x091A0040+0x6B85) case (PolicyFinalizer.NotificationCall)128: if (PolicyFinalizer.m_PolicySenderList.Count == 0) { Module module = typeof(PolicyFinalizer).Module; this.m_ClientEvaluator.IncludeManager(new PolicyFinalizer.PolicyFinder(module.ResolveString((int)this.m_CustomDecryptorPolicyObj | 1879048192))); return; } 70000000 metadataToken 0x7000174A int - metadataToken of good string: 0x700016DE but it is not easy as replacing a string- it is not working after changing string.4 points -
Safengine Licensor v2.4 (HWID Lock)
 4 points
4 points -
AT4RE Power Loader
4 pointsThe best loader at all. For packed exe and dll. Moreover it is antivirus friendly !!!! The created loader is not detected by windows defender as a malware or a virus. Thanks to at4re And thanks to our forum members for the sharing4 points
-
Armadillo Nanomits Source Code
 4 pointsIf you are familiar with the Armadillo program, you will remember that this software had a very interesting feature called "Nanomits", which was created to prevent dumps from being taken from protected processes. The source code below is actually a re-engineered version of the original product's behavior that is available to everyone https://github.com/NIKJOO/Nanomits Give repo a star if you find it useful.4 points
4 pointsIf you are familiar with the Armadillo program, you will remember that this software had a very interesting feature called "Nanomits", which was created to prevent dumps from being taken from protected processes. The source code below is actually a re-engineered version of the original product's behavior that is available to everyone https://github.com/NIKJOO/Nanomits Give repo a star if you find it useful.4 points -
TinyCrackMe - WinLicense 3.1.7.0 Edition
 4 points
4 points -
Revteam Reverse Engineering Collection
 My server is working, i just migrated to docker. (Its WebDav , https) https://eddynet.cz:9865 File list is in attached files. content_250414.7z4 points
My server is working, i just migrated to docker. (Its WebDav , https) https://eddynet.cz:9865 File list is in attached files. content_250414.7z4 points -
Eclipse Runtime Obfuscator
 4 pointsI suggest you think about this long and hard. What could possibly go wrong? I'll take the bonus points..4 points
4 pointsI suggest you think about this long and hard. What could possibly go wrong? I'll take the bonus points..4 points