UnPackMe
27 files
-
A Delphi file is protected with an old version DotFix NiceProtect (7.1)
Original Entry Point is encrypted
Just find and restore OEP, recover the IAT and unpack it- 28 Downloads
 fReestYlerSubmitted
fReestYlerSubmitted -
Two files are protected with an old version Themida (3.1.4)
Entry Point is virtualized
Just find and restore OEP, recover the IAT and unpack if it possible
Virustotal detects it as a virus, but my AV software is not
- 100 Downloads
 fReestYlerSubmitted
fReestYlerSubmitted -
I want you guys who are capable of unvirtualizing and unpacking them to upload the final ones.
These files are just the same part of the codes virtualized which are 2 lines of the original mfc source codes.
So if you can unvirtualize them and unpack them, please upload the final ones.
Any other protections are excluded absolutely.
Give it a try and improve your skills.
Best Regards.
sean.
- 64 Downloads
 lovejoy226Submitted
lovejoy226Submitted -
Hey everyone,
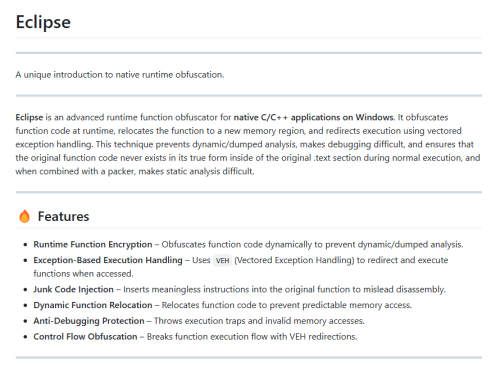
I’m sharing an UnpackMe challenge that combines VMProtect packing with runtime function obfuscation using Eclipse Runtime Obfuscator. This should be an interesting challenge for those who enjoy working with dynamic obfuscation and anti-debugging techniques.
Protection Details:
VMProtect is used for basic packing, with import protection and anti-debug enabled. Eclipse Runtime Obfuscator dynamically obfuscates function execution, making dumped analysis and debugging difficult. Function code is relocated to a new memory region at runtime and accessed through vectored exception handling (VEH) instead of direct execution. Eclipse Runtime Obfuscation Features in this UnpackMe: Exception-Based Execution Handling – Execution is redirected via VEH, preventing direct tracing. Junk Code Injection – Adds meaningless instructions to mislead disassembly and make static analysis harder. Dynamic Function Relocation – Functions are moved at runtime, disrupting predictable memory access. Control Flow Obfuscation – Execution flow is broken up and redirected via exception handling. Anti-Debugging Protection – The binary throws access violations and illegal instructions to interfere with debuggers. Goals:
Unpack the binary (remove VMProtect and restore the original imports). Defeat runtime function relocation and deobfuscate the function logic by resorting the original function code. Reconstruct a clean, runnable (optional) version of the executable with original control flow. Explain how you unpacked and fixed the program, detailing the approach to defeating VEH-based execution and restoring the function code. Bonus points if you can crack the password in the console application demo code. Notes:
VMProtect is only used for packing, not virtualization. The main challenge comes from Eclipse’s runtime function relocation and exception-based redirections. Dumping the process isn’t enough, as function code is dynamically obfuscated in memory. The obfuscated functions are exported and named "testCCode", "testCCode2", and "DemoFunction" (this function has the crackme code in it). Would love to see a write-up on defeating the VEH-based execution and restoring the original function code! More information can be found about the Eclipse Runtime Obfuscator project on GitHub.
Looking forward to seeing your approaches. Good luck and happy reversing!
- 17 Downloads
deleted1235435Updated -
The Entry Point is virtualized.
2 Parts of the codes are also virtualized.
[Your Mission]
Just unpack this file and make it run well without any errors or termination.
No devirtualiztion are necessary.
- 82 Downloads
 lovejoy226Submitted
lovejoy226Submitted -
This is an example program I used to shell The Enigma 7.7. You can shell it, bypass it, PatchHWID, KeyGen to make it run normally. Of course, it would be best if the shell could be peeled off.Have fun!
https://workupload.com/file/EGgppWamMA6
Cracked:
- 159 Downloads
lengyueUpdated -
..::[FaTmiKE 2o24]::..
Welcome to my 5th crackme!
It took a long time implementing this, i hope it is hard to solve!
Sorry for the long load time of the crackme
Here are the goals:
1. The main goal is to unpack and uncrypt this crackme.
2. Find a valid serial or write a keygen.
If you only succeed in 1. or 2. it's fine, i am happy to read every solution.
(e.g. if you can find a valid serial without unpacking, please write a tutorial how you did it!)
The crackme was tested on windows 10.
Have fun!
PS:
1.) Windows Defender returns a false positive due to my custom protection. If you do not trust me, please use a VM for reversing the crackme.
2.) The crackme has to be started from explorer.exe
The crackme can also be found here:
https://crackmes.one/crackme/66ca5b91b899a3b9dd02af52
- 30 Downloads
FatmikeUpdated -
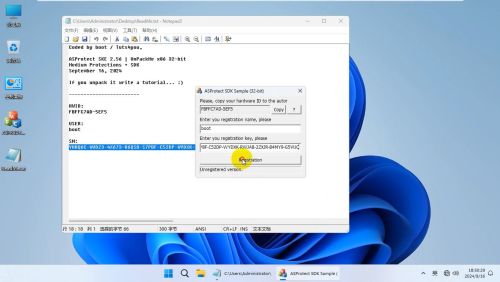
Coded by boot / Tuts4you,
ASProtect SKE 2.56 | UnPackMe x86 32-bit
Medium Protections + SDK
September 16, 2024
If you unpack it write a tutorial...
------------------------
HWID:
FBFFC7AD-5EF5
USER:
boot
SN:
YHRQ6C-WVDZ3-4X673-R6QSB-S7PBF-C52DP-WYDXK-RWJAB-2ZXJR-B4MY9-G5VUQ
- 85 Downloads
 bootSubmitted
bootSubmitted -
Example of Shell Addition for Enigma 7.60.
This is a different example from the past, interested friends please challenge.
Unpack, cracking or Patch HWID. Use your means to make it work correctly.
TheEnigma_7.6_x32&x64Example_protected.rar
- 66 Downloads
lengyueUpdated -
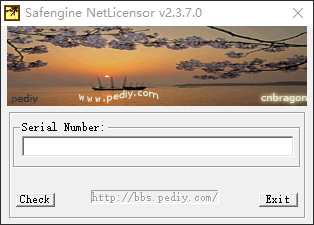
Based on Safengine Licensor with the combination of:
Safengine Code Protection (Mutation & Virtualization) Safengine Licensor Local License Verification All protection options enabled:
Anti Debug Anti Trace Anti Virtualization Anti Attach Anti Dump Anti API Hooks Self Integrity Check Code & Data Encryption Metamorphic Code Generation Branch Obfuscation Code Mutation Code Virtualization Advanced Code Replace Import Elimination API Relocation Try to unpack it.
Enjoy! ; )
所有保护选项
享受 ! ; )
Safengine NetLicensor v2.3.7.0UnpackMe.exe
- 23 Downloads
 kuazi GAUpdated
kuazi GAUpdated -
- 81 Downloads
 CodeExplorerUpdated
CodeExplorerUpdated -
Two simple Win x64 GUI applications protected using Enigma x64 v7.4.
Challenge is to;
bypass the hardware ID lock; unpack the application. Let us go together to solve this issue.
- 366 Downloads
 lovejoy226Updated
lovejoy226Updated -
I coded a simple Win x64 GUI application with a close button and protected it using Safengine Shielden v2.4.
Challenge is to;
bypass the hardware ID lock; unpack the application. Let us go together to solve this issue.
- 134 Downloads
 lovejoy226Updated
lovejoy226Updated -
This is an encryption example using The Enigma Protector 7.50 encryption.
Enigma 7.5_x64_DEMO.rar TEP_7.5x32_DEMO.rar
- 30 Downloads
lengyueUpdated -
过程式编程语言,所以IAT和资源很少
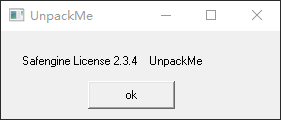
Safengine License 2.3.4 with medium protection options enabled.
Program is written in assembly language so there are very few IAT and resources.
- 140 Downloads
 kuazi GAUpdated
kuazi GAUpdated -
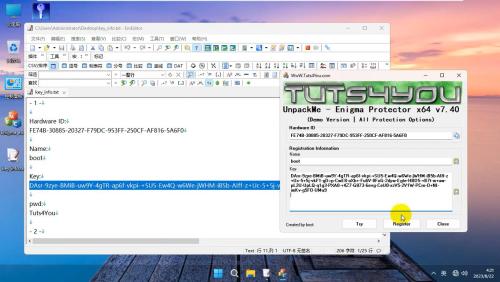
Unpackme x64 - Enigma Protector 7.40
(Demo Version | All Protection Options)
Enigma x64 + SDK +HWID Lock + etc...
https://forum.tuts4you.com/
If you unpack it, please make tutorial(s)... I will mark the answers with tutorials as a solution.
The compressed package includes a simple MP4 display, please pay attention to check...
Created by boot / From Tuts4you
2023.08.21
- 600 Downloads
 bootSubmitted
bootSubmitted -
Please debug/unpack in the virtual machine This target is protected by a specially modified version of VMP, with some simple protection measures added It only supports running on x64 operating systems, such as Win7 x64 or Win10 x64, which may also support most Win11 x64 If you unpack it, please make tutorial(s)... I will mark the answers with tutorial(s) as solution.
- 252 Downloads
 bootSubmitted
bootSubmitted -
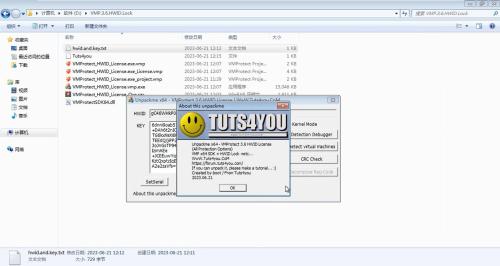
Unpackme x64 - VMProtect 3.6 HWID License
(All Protection Options)
VMP x64 SDK + HWID Lock +etc...
WwW.Tuts4you.CoM
https://forum.tuts4you.com/
If you can unpack it, please make a tutorial... I will mark the answers with tutorials as a solution.
The compressed package includes a simple MP4 display, please pay attention to check...
Created by boot / From Tuts4you
2023.06.21
- 731 Downloads
 bootSubmitted
bootSubmitted -
Unpackme - Armadillo x64 v9.64 | WwW.Tuts4You.CoM
General/Default Protection Options = HWID Lock + etc...
If you can unpack it, please make a tutorial...
The compressed package includes a simple MP4 display, please pay attention to check...
HWID:87DF-0E78
NAME:boot
KEY:000016-M9KY7Y-1PM436-8JKH7H-G8QXCH-3ACEGN-Y5ND6B-TY4VJ2-5FX1WY-WGJBFB
After seeing the dynamic screen, please click the LEFT MOUSE button to exit OR press the "ESC" button once to exit.
Created by boot / From Tuts4you
2023.06.19
- 203 Downloads
 bootSubmitted
bootSubmitted -
..::[FaTmiKE 2o23]::..
After a little break i decided to program another little crackme (This is my 4th crackme).
Here are the rules:
1. The main goal is to unpack this crackme or write a loader.
2. If you like, find a valid serial or write a keygen.
The crackme was tested on windows 10.
Have fun!
- 90 Downloads
FatmikeUpdated -
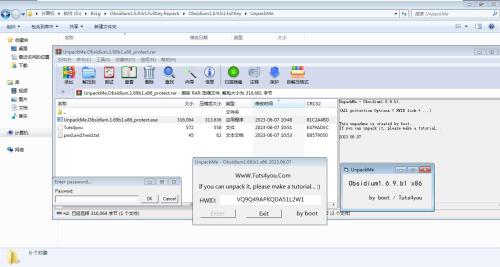
Obsidium v1.6.9.b1 x86 = All Protection Options = HWID lock + etc.
This unpackme (VB6.0) is created by me.
If you can unpack it, please make a tutorial...
2023.06.07
- 156 Downloads
 bootUpdated
bootUpdated -
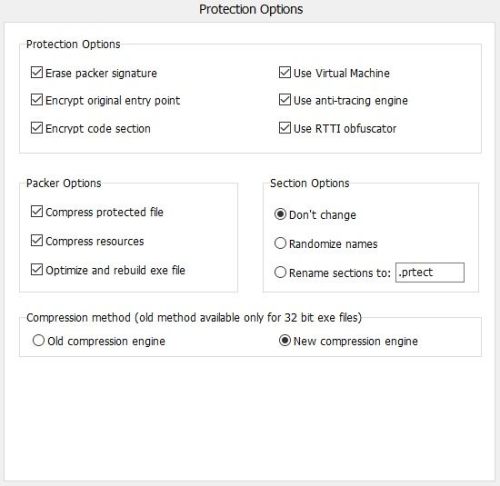
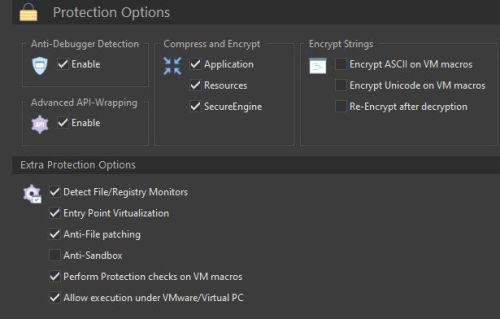
The target is an old software (from 2010) coded in c++, I just apply the VMP protection without any special code as I show in the two screenshots. All available protection features in VMProtect were used with this unpackme. Refer to the attached images for the specific protection settings used.
Challenge is to unpack the file, providing an explanation and details on your methodology.
- 1,265 Downloads
 X0rbyUpdated
X0rbyUpdated -
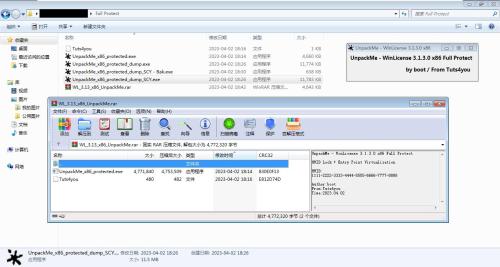
UnpackMe - WinLicense 3.1.3.0 x86 Full Protect
HWID Lock + Entry Point Virtualization + Etc...
HWID:
1111-2222-3333-4444-5555-6666-7777-8888
Author:boot
From:Tuts4you
Time:2023.04.02
- 1,147 Downloads
 bootSubmitted
bootSubmitted -
- 489 Downloads
 CodeExplorerUpdated
CodeExplorerUpdated -
It's a PELock'ed file. Try to unpack it if you have time, if you are a skilled code reverser or the author, you maybe can do it.
Thank you for your effort in advance.
- 258 Downloads
 lovejoy226Updated
lovejoy226Updated
Download Statistics
- 2,163 Files
- 354 Comments
- 894 Reviews
-