2.xx Plugins
84 files
-
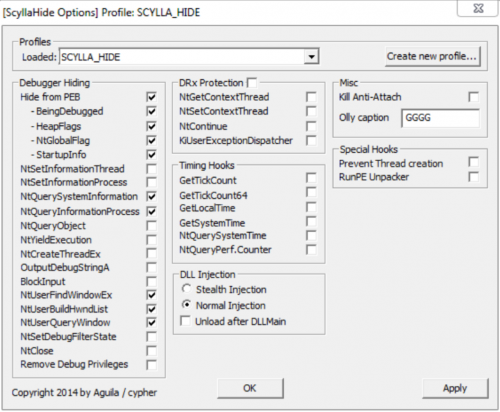
ScyllaHide is an open-source x64/x86 usermode Anti-Anti-Debug library. It hooks various functions in usermode to hide debugging. This will stay usermode! For kernelmode hooks use TitanHide.
Debugger Hiding:
PEB - BeingDebugged, NtGlobalFlag, Heap Flags NtSetInformationThread - ThreadHideFromDebugger NtQuerySystemInformation - SystemKernelDebuggerInformation, SystemProcessInformation NtQueryInformationProcess - ProcessDebugFlags, ProcessDebugObjectHandle, ProcessDebugPort, ProcessBasicInformation, ProcessBreakOnTermination, ProcessHandleTracing NtSetInformationProcess - ProcessBreakOnTermination, ProcessHandleTracing NtQueryObject - ObjectTypesInformation, ObjectTypeInformation NtYieldExecution NtSetDebugFilterState NtUserBuildHwndList - EnumWindows NtUserFindWindowEx - FindWindowA/W, FindWindowExA/W NtUserQueryWindow NtClose NtCreateThreadEx BlockInput Remove Debug Privileges OutputDebugStringA - OutputDebugStringW Timing Hooks:
GetTickCount GetTickCount64 GetLocalTime GetSystemTime NtQuerySystemTimeHook NtQueryPerformanceCounter Special functions:
Prevent Thread creation - for protectors like Execryptor. Only use if you know what you are doing ! Malware RUNPE Unpacker - Hooks NtResumeThread and terminates + dumps the process created by malware Protecting and Stealthing DRx (Hardware Breakpoints):
NtGetContextThread NtSetContextThread KiUserExceptionDispatcher (only x86) NtContinue (only x86) Hooks:
Stealth hooks for 32-bit targets (Tested against Themida/VMProtect)- 911 Downloads
 Teddy RogersSubmitted
Teddy RogersSubmitted -
It’s really annoying when you have to deal with the initialization part of a malware, most of the time a malicious executable follows the same alloc/decrypt/jump_to_decrypted_code scheme. So, I decided to write something to ease and automate the initial process investigation of a malware.
The idea behind the plugin is simple, Sequential Dumper is conceptually able to dump blocks of memory in sequence: it monitors the flow of the malware code trying to dump all the new allocated/decrypted parts in different memory areas containing code of the malware itself.
A practical example will clarify everything:
The real malware is obtained after some tedious steps: a runtime allocated buffer is used like a bridge between the original and the real malware. The original malicious file is just used to decrypt a piece of code, and then this particular code will create the real malware replacing the old original file.
A malware with this behaviour is available at VirusTotal.
Can I use Sequential Dumper with this kind of malwares? Yes you can, here is the result of the execution with the enabled plugin:
The left part of the image comes from a folder view, it shows the list of the files created by the plugin at runtime; the right part contains the logged data inside Ollydbg view. There are only two simple cryptic phrases by the plugin inside the log window, it’s pretty minimal in terms of information, but you don’t need anything else because you can understand how the code flow switches from a memory block to another. The first switch has been done from the original file to the block in memory, the other one is the jump back to the real malware. As you can see from the picture there’s a interesting message by Ollydbg “Unload C:\…”: the original malware doesn’t exist anymore, it has been overwritten by something else.
What kind of files does Sequential Dumper create?
The listed files are raw dumps taken during the execution of the malware. Every single file has a name starting with “Dump_xx” where the double ‘x’ defines the creation order sequence.
The last part of the name has two distinct forms, with or without “_on_exit” tag. I prefer to dump a block of memory before and after its execution because a decryption or a simple byte modification could happen in the middle of its code. Take in mind that a single dump will be performed if and only if the memory block has been modified.
There’s also a checksum algorithm inside the plugin because I wanted to avoid duplicated dumps, if the accessed block of memory was already dumped you’ll see the switch log message only.
Usage
Sequential Dumper is a two states plugin: enable or disable. In this first release the menu has two items only, the ‘About’ item and the other one which is used to activate the plugin. It’s not necessary to enable the plugin at the first instruction of the malware, you can activate it whenever you want.
As you might guess everything relies on Ollydbg trace system, you have to run the debuggee in trace mode otherwise it fails catching a memory switch.
Ollydbg is not allowed to trace system DLL code by default, but I would suggest you to change this setting. Why? Take a look at 1cd7fe891143415870d1e7cf12100b161d456e777dab23fe7821c53bfed87052 sample:
The malware uses CallWindowProc to run a snippet from somewhere else, in this specific case the new code resides at 0x3900060. The address is outside the original exe and if you don’t allow Ollydbg to trace into system DLL the plugin won’t catch anything from the *hidden* snippet. I think you can understand why you might need to allow Ollydbg to trace system DLL. It’s not a rule but it might help.
Final Notes
Sequential Dumper produces a sort of chronicle of the malware execution. It comes from a simple idea and it was born in few hours so don’t expect too much. Take in mind it’s the very first release and it may be exposed to bug. Just in case don’t hesitate to send a mail with detailed information about the bug.
The plugin has some limitations but it could be helpful for someone, what do you think?
- 143 Downloads
 Teddy RogersSubmitted
Teddy RogersSubmitted -
SigCreator is a reproduction of "SigMaker 0.4" for the new OllyDbg version 2.xx.
SigCreator generates you all needed information for using the selected signature in your code. Furthermore it will give you a list of all occurrences of the signature in the current module.
Result:
Sig start // Start-address of signature occurrence Sig end // End-address of signature (both addresses are inclusive) // sizeOfSig = sigEnd - sigStart + 1 Modulebase // Base address of the module Offset // Offset from base address to the signature Signature // Signature in code design Mask // Mask of signature in SigMaker-Style Functions:
* Scan code for selected signature
Shows you all occurences of the selected signature.
* Get unique signature
Gives you an unique signature next to the selected address.
Note: SigCreator menu will only appear in the disassembler menu.
Note: You can copy the results by shortcur "Ctrl+C" or by popup menu.
- 430 Downloads
 Teddy RogersSubmitted
Teddy RogersSubmitted -
This simple plugin allows the main Olly2 window to be minimised and hidden, as well as restored from an icon in your system tray.
- 105 Downloads
 Teddy RogersSubmitted
Teddy RogersSubmitted -
Hello guys I have written a plugin named WeakOD to help debugging with OllyDBG 2.01h.
Auto clears debugger bit in PEB on new process creation. Allocate some memory to do small fixes for debugee. Inject DLL, so you can inject a DLL into debugee, to help changing debugee's behavior. Break on DLL, stops on DLL entry point, so you can analysis it, or find out why it's loaded.- 165 Downloads
 Teddy RogersSubmitted
Teddy RogersSubmitted -
This is a simple plugin for OllyDbg2 to keep the windows maximized. The plugin support is still in alpha so I have not converted the whole PDK yet, but full Delphi source is included.
- 142 Downloads
 Teddy RogersSubmitted
Teddy RogersSubmitted -
Swordfish is an OllyDbg 2 plugin, supports many useful features to simplify the OllyDbg use.
- 1,021 Downloads
 Insid3CodeUpdated
Insid3CodeUpdated -
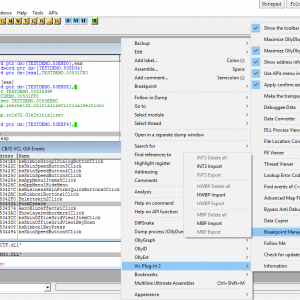
----- [ MENU ] ----- Show the toolbar in the title of OllyDbg window Maximize OllyDbg window when staring Maximize OllyDbg child windows when staring Show address info in status bar Use APIs menu in OllyDbg menu bar Apply confirm exit for OllyDbg Make the transparency for OllyDbg window Debuggee Data Delete UDD data of the current session Delete all UDD data Open UDD data list Delete recent debuggee files Data Converter DLL Process Viewer File Location Converter PE Viewer Thread Viewer Lookup Error Code Find events of C++ Builder / Delphi VCL GUI application Advanced Map File Importer Map File Importer Open Label window Open Comment window Bypass Anti Debugging Hide the PEB Data Copier VA Address RVA Address Offset Address ANSI String UNICODE String Code Ripped Breakpoint Manager INT3 Delete all INT3 Import INT3 Export HWBP Delete all HWBP Import HWBP Export MBP Delete all MBP Import MBP Export Follow Me Follow in Disassembler at <address> Follow in Dump at <address> Copy <address> to clipboard Check for update Information
- 1,879 Downloads
 VicUpdated
VicUpdated -
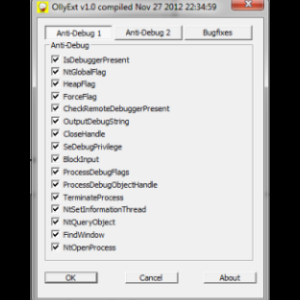
OllyExt is a plugin for Olly 2.xx debugger. The main intention of this plugin is to provide the biggest anti-anti debugging features and bug fixes for Olly 2.xx. VMProtect support!
The currently available commands are the following:
Code Rip to Clipboard Code Rip to Clipboard Recursive Data Rip to Clipboard Signature Rip to Clipboard The currently supported protections are the following:
IsDebuggerPresent NtGlobalFlag HeapFlag ForceFlag CheckRemoteDebuggerPresent OutputDebugString NtClose SeDebugPrivilege BlockInput ProcessDebugFlags ProcessDebugObjectHandle TerminateProcess NtSetInformationThread NtQueryObject FindWindow NtOpenProcess Process32First Process32Next ParentProcess GetTickCount timeGetTime QueryPerformanceCounter ZwGetContextThread NtSetContextThread KdDebuggerNotPresent KdDebuggerEnabled NtSetDebugFilterState ProtectDRX HideDRX DbgPrompt CreateThread NtSystemDebugControl Custom ( Write your own ) The currently supported bug fixes are the following:
Caption change Kill Anti-Attach ( dll integrity check ) Requirements:
Microsoft Visual C++ 2010 Redistributable Package (x86) OS support:
Windows XP Windows Server 2003 R2 Windows Server 2008 R2 Windows 7 Windows Server 2012 Windows 8 Windows Server 2012 R2 Windows 8.1 Limitations:
Because of missing PDK function data ripping is ONLY on 2.01 latest supported If you have any problem just notify me.
- 4,438 Downloads
 ferrit.rceUpdated
ferrit.rceUpdated
Download Statistics
- 2,161 Files
- 352 Comments
- 894 Reviews
-