CrackMe
49 files
-
This is an example for submitting a CrackMe in the Downloads section of the site.
You can download the file and run Debug Blocker x64. Nothing too exciting will happen!
The challenge here would be to patch the debug-blocker function so that it does not spawn a second process.
- 824 Downloads
 Teddy RogersUpdated
Teddy RogersUpdated -
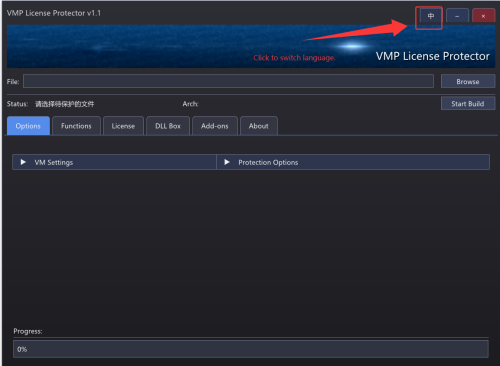
This is a recently developed recreational utility. I'm unsure which forum section is appropriate, so moderators please feel free to move it if necessary.
The tool implements a combined The Enigma and VMProtect protection scheme and is designed for applying VMProtect to Win32/Win64 executables and DLLs without requiring source code. It is not compatible with .NET assemblies.
The interface supports Chinese/English language switching. To function, VMProtect_Con.exe must be placed in the tool's directory. Note that the tool itself is incompatible with Windows 7 and requires the DirectX 11 runtime to be installed. Software protected with it remains compatible with Windows XP/7/10.
Trial Version Limitations:
Only the anti-hijacking feature is enabled.
All other functions are disabled.
Uses a fixed RSA key.
Please do not use it to protect commercial software.
While some features are disabled, the tool may be sufficient for users with modest needs if patched. The trial license expires after one month, but functionality can be extended through patching.
Archive Password: View by double-clicking the RAR file in WinRAR (check archive comment) or use: tuts4you.- 85 Downloads
lengyueUpdated -
The CrackMe I made has a special feature - custom jit. Bruteforce is not necessary.
To launch, install .NET 10
To run the file, delete CrackMe.deps.json - this way the file will load the local runtime, and not from the root folder.- 18 Downloads
Dark_BullUpdated -
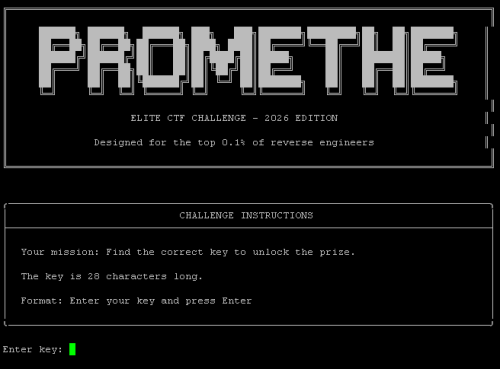
A recruitment challenge for those who see what others cannot.
The binary guards an encrypted message. To reveal it, you must provide the correct 28-character key. There is no backdoor, no shortcut, no unintended solution—only the key.
The verification process spans twelve interconnected layers. Each depends on others. Disrupting one cascades through all. The binary knows its own shape and will notice if you change it.
Some defenses are apparent through static analysis. Others manifest only at runtime. A few exist in the liminal space between instruction and execution—observable only through their effects, never their implementation.
Difficulty 6/6
## Rules
- Standard crackme rules apply
- The solution is the 28-character key
- Picture of the solved challenge to be posted only 48h after completion.
- No external services or network required
- Linux x86_64
The reward prize and job offer will terminate in 24 hours.- 17 Downloads
PrometheusSubmitted -
Good evening everyone,
I’ve put together my first CrackMe using DNGuard 4.94 and its License Management feature.
The application is called “Cool Beans.exe” - terrible name, I know 😄
Once cracked successfully, you’ll be taken to the main form, which displays a (slightly stupid) message.
Hope you enjoy taking a look.
Cheers 🍻
🔐 DNGuard 4.94 Protections Used
Encryption
Encrypt compiler-generated code
Encrypt .ctor (constructor) methods
Encrypt blob heaps
Encrypt strings
HVM (Hardware Virtual Machine) Protection
Enable HVM technology
HVM Code Protection Level: 5
HVM II technology enabled
HVM II Level: 5
HVM protection for method LocalVarSigTok
HVM proxy methods
Illegal HVM action prevention
Obfuscation
Destroy name heaps of metadata
Metadata obfuscation
Automatic renaming
Dynamic control flow obfuscation
Anti-Analysis / Runtime Protections
Anti-Dump protection
Run application in Shadow AppDomain
Suppress IL disassembly tools
Anti-other static decompilers
Avoid illegal JIT action
- 18 Downloads
 Visual StudioUpdated
Visual StudioUpdated -
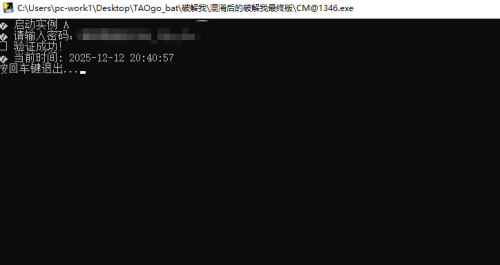
Decryption doesn't involve modifying the Python interpreter; everything is done through code obfuscation. Password verification is performed via hash comparison—finding the correct hash to compare against counts as success. My custom obfuscator has just been released—come and give it a try!
It includes techniques such as control-flow obfuscation, string encryption, virtualization, and C++ white-box implementation.- 8 Downloads
1346Updated -
[ Crackme ] C++ x64 Protection
Compiler: C++ (x64)
Protection:
Heavy obfuscation (control flow flattening, opaque predicates)
Full code virtualization (custom VM with unique opcode set)
Anti-tamper checks (integrity verification, debugger detection)
Encrypted string/table storage
Custom packer layering the entire binary
Challenge: This is a server-client authentication system protected by a custom packer. The client executable performs login validation by communicating with a local/emulated server component.
Goal:
Patch the client to bypass authentication OR
Emulate the server to allow successful login with any credentials
You are free to choose either approach.
Hint / Test Account:
Username: testacc
Password: testpass
Notes:
The packer is not a known public tool (e.g., ConfuserEx, KoiVM, VMProtect). It is fully custom-built.
All network logic, crypto, and validation routines are virtualized and packed.
Anti-debug and anti-analysis tricks are active.
(it has fake section name called vmp2 that gives fake information to tools that looks like packed with vmp)
Good luck, show your skills in unpacking, emulation, or clean patching!- 31 Downloads
PerfectDiddyUpdated -
Hi,
First of all i have to say " this is not my project and some friend ask me to upload challenge here "
Compiler : .NET
Protection :
[+] Binary Obfuscation
[+] Code Virtualization
[+] Anti-Debugging / Anti-Tampering
[+] Maybe some other protection
Rule :
Patch file to accept any password or find real password ( both accepted )
i will appreciate if you write something about you have done
Hint :
Run & Analyze file inside VM or isolated environment becuase of file isn't mine so i'm not responsible for anything
Regards- 34 Downloads
 GladiatorUpdated
GladiatorUpdated -
Hello everyone,
I'm a AutoIt developer, and I've created a small portable program that uses a custom packer to protect some assets. The program is written in AutoIt and consists of two files: M-Dl.exe and assets.zip. I'm looking for skilled reverse engineers to test the security of my custom packer.
The Goal:
The challenge is to extract the image files that are contained within the custom packer. I've designed the packer with my own security techniques and would love to see how it stands up against the community's expertise.
Repository & Download:
You can find the project repository on GitHub, including the binary for download:
https://github.com/yutijang/M-Dl
I'm eager to learn from your findings and improve my security practices. Any feedback on the protection mechanisms, potential vulnerabilities, or how they were bypassed would be greatly appreciated.
Thank you for your time and effort!
- 19 Downloads
yutijangSubmitted -
A "Crack Me" challenge created by lord "Voksi" , a well known person in the "warez" scene.
And no, this challenge is not uploaded by "Voksi" himself, it's uploaded via a proxy which is myself, an old friend of "Voksi" .
GOAL: Obtain the Correct key
Greetings to MasterBootRecord, Voksi, FJLJ, And also a few others, you know who you are ❤️
- 66 Downloads
 casualPersonSubmitted
casualPersonSubmitted -
Find correct license key, don't try to patch file.
Updates & Improvements :
+ Listen to KAO advices from Version 1.0 + Improved Metamorphic Junk Code Generator + Encrypted VM Handlers + Control-Flow Obfuscation + VM Handler Obfuscation Hint :
File Packed with UPX 5.0 just for compression ( just decompress it using -d command )
Thanks to @kao for Tips.
- 29 Downloads
 GladiatorSubmitted
GladiatorSubmitted -
Brief and useful
Find correct license key, don't try to patch file.
What comes within this crackme :
+ Code Virtualization + Unique Junkcode Generation + Control-Flow Obfuscation
- 40 Downloads
 GladiatorSubmitted
GladiatorSubmitted -
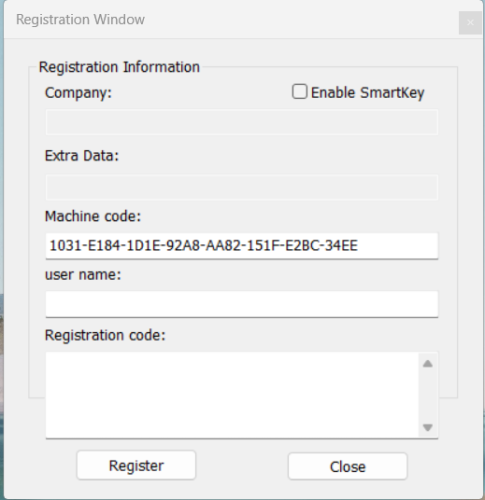
This is a WinLicense 3.2.2/sample, set by default, without adding an SDK in the source code, only adding a window function through an external plugin. I don't know if bypass can be cracked, I tested it and it doesn't. Shedding may be more complicated.Please use your own way to crack it. Whether it's molting, bypass, or keygen, they are all the best methods. No need to upload your proposal, posting a picture is the best answer. I will strive to learn towards your achievements. HWID:1031-E184-1D1E-92A8-AA82-151F-E2BC-34EE NAME:Mr.Leng .RegistCode:2FGP7NTY-22AMY4QL-XXEHAOKD-ZJKHKDKR-VY66SHXY-YTEQXVBF-GAXAEFIA-7BQWOTA5-5CE344K4-VBGMG25R-5TGP26WS-AIKQB3S5-5LDUHEHX-S6KSKH3H-OPPHIFAX-N6WPWIAM
WinLicense3.2.2_sample.rar
- 47 Downloads
lengyueUpdated -
I have put all important information in HWID-License.txt.
I hope you all come up with some fascinating solutions.
If you want leave the solution and also if you want to show off you can do that as well!
- 228 Downloads
senzuuuSubmitted -
This is my first attempt at a binary protector. Currently, the VM has very little protection, so this should be good for those interested in learning about VM-based obfuscation. I intend on uploading new challenges that feature my protector as I add more features.
GOAL:
- You must find the correct key. Simply patching to get a goodboy message is NOT allowed.
- Bonus points for devirt and explanation of your approach.
- MOST IMPORTANTLY, have fun!
:)
- 72 Downloads
ra1nSubmitted -
Hi
Nuitka compiled python 3.11 file
Correct password doesn't important
Just patching
Thanks
- 53 Downloads
 Sh4DoVVUpdated
Sh4DoVVUpdated -
Hello, this is a crackme made in python by a friends (wrc3667 on discord)
Difficulty: [95 / 100]
The purpose of this challenge is to find the correct key (note: the key should be in hexadecimal, otherwise the program will istantly close)
Features:
- Constant encryption
- Name encryption
- Opcode shuffling
- Bytecode encryption
- Stack encryption
- Bytecode instruction mangling
- Guillotine Interpreter
- Complete namespace virtualization
- 32 Downloads
0verp0werSubmitted -
If you want to try this challenge, please read the following text descriptions:
1. Please try to debug the kernel driver in the virtual machine instead of your real machine to avoid causing a blue screen on the physical machine
a. Why blue screen? For things like Ring0.sys, as I mentioned earlier
b. Copy the Tuts4you.ini file to the C:\Windows\ directory of the virtual machine
2. I have added a test signature to the driver, so to load this driver, you need to enable Windows test mode
a. Press and hold the "WIN+R" key to launch the CMD console as an administrator, enter bcdedit /set testsigning on
b. Restart your computer
c. After restarting, there is a prompt similar to "test mode" on the bottom right corner of the computer, indicating that it has entered test mode
3. If you give up this challenge, you can choose to turn off the testing mode at any time
a. Press and hold the "WIN+R" key to launch the CMD console as an administrator, enter bcdedit /set testsigning off
b. Restart your computer
c. After restarting, there is no prompt similar to "test mode" on the bottom right corner of the computer, indicating that the test mode has been turned off and entered normal mode
4. How to load this driver?
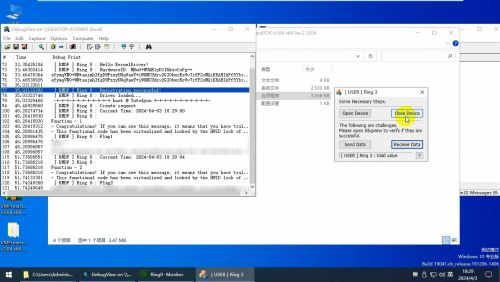
a. Use DriverMonitor to load this driver
i) Download DriverMonitor from here
b. Run Ring3.exe and click on "Open Device"
c. Use Dbgview to view the corresponding debugging information and whether to output Flags
i) Download Dbgview from here
5. Please note:
Due to *.sys being protected by VMP, unlike *.exe or *.DLL files:
a. This means that you cannot directly debug it using x32/x64Dbg or OllyDbg
b. This means that there is no ready-made script/unpacker or one click cracking tool
c. This means that you need to manually use windbg for debugging
The ideas you can try are:
1. Use Windbg to debug Virtual Machine
2. Patch HWID -> Allowed! You can try to do this
3. Unpack this kernel driver -> Allowed! You can try to do this
Verify if this challenge has been resolved:
1. Provide me with the content of Flag1 and Flag2
2. After patch HWID or Unpack, ensure that the driver's image or dump file can be loaded, and remove VMP protections, which can directly output Flags
If you have already solved this challenge, please create tutorial(s).
boot @ Tuts4you
-------------------------------------------------------------------------------------------------------
Reminder:
1. Please do not try on the physical machine, please be sure to try on the virtual machine.
2. Turn on testing mode and restart the virtual machine.
3. Copy Tuts4you.ini to the "C:\Windows\" folder.
4. Operate according to my video.
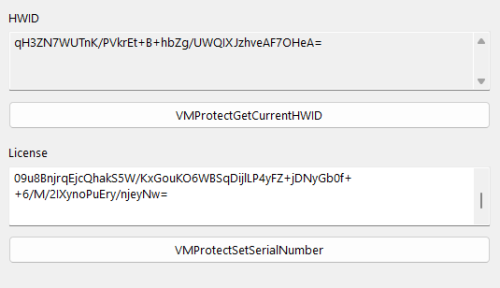
HWID:
MBuO+WUQR1yD1Z5kzvCoPg==
KEY:
efymqVNO+WNtaujmh3fgD9PzzyU0q9awY+iW8MCUdrv2GIObwrRs9v7rfF2sMQiKBAHIkPf5YbrNHIwfsalY1+YKInnRvOxOr8mrMpViwtihBzJNYDv5Bw58XO7zoOTJBHMuihya/doG+jCD6xQhoblVPHrRpL+aRpVAB7Eix9sAQMqkdQpJM6x3EQ27sFazT/HSn2W5j1JQI3BRODLuEfg3KWKdfq2t3fcHqYSuSveWOm7XzUMSagB1pS+eCNd2DuoFACfki3KU1ipibClLVStmIo0GwtYa2OJqAQYoLQRuClSMnc1eSuxYswLlK49aEMNwRCQagVpxciPB+s2BntbIrjvSm/YOKFWmqLL30RPBHgYo3+aIXb0ggJP4Rp0JfhgO0orEYLbvNC3yYhW3vUHxK6IZKsxWNiKGP6bCmB8A6bWn83RP/KQNMrmG9e8k+aI5YXklxkP3PRoNkZnktaerg3Qj5kD7oaxlm/Bf/QGuIz+71hbU9jazbPZEfmbgNnPgfo7vvywdoHnnJcymCppqXFtUoezjPjQZjm4E2FniYRpSDTfziOoL4xszXwBLjMjcyu0QuYuJ2ueG/B8hH3K0PpLjNg2Wy5Er87UU3blWWtF08gm/QSKm92OJrrjUE6yNnqVrNrQ81WX68nbJ/fmNnOMA9uAN+GD3TOlZzbs=
- 41 Downloads
 bootSubmitted
bootSubmitted -
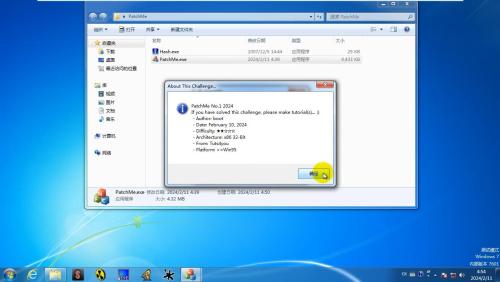
PatchMe.exe
MD5: DD4E072F8B5CA241927EAA63DED47383
SHA1: 08F4699C3A84F5E40343CE9A9AD05046EE15D6DD
CRC32: 9A4C0721
PatchMe No.1 2024
Please check the ReadMe.mp4 in the zip package, you'll understand what I mean...
If you have solved this challenge, please make tutorial(s)... I will mark the answers with tutorials as a solution.
About This Challenge...
- Author: boot
- Date: February 10, 2024
- Difficulty: ★★☆☆☆
- Architecture: x86 32-Bit
- From: Tuts4you
- Platform: >=Win95
- 118 Downloads
 bootSubmitted
bootSubmitted -
A little "CrackMe" challenge (.NET + Native).
Need to crack the application so that it does not require a license for its operation.
P. S.
Application requires .NET 6 to run
- 103 Downloads
 InvizCustosUpdated
InvizCustosUpdated -
=== SPOILER INSIDE SOURCE CODE TAB ===
A WinLicense'd version of TinyCrackMe
Rules:
1. Unpack first
2. Do whatever you want after unpack, as long as ":3" MessageBox appear :3
Just want to see how long ppl will crack the latest version of WinLicense...
WL Protection:
- Anti-Debugger
- Advanced API-Warping
- Compress And Encrypt (all 3 options)
- Full Encrypt Strings
- Detect File/Registry Monitor
- Entry Point Virt
- Anti File Patching
- Perform Protection Check
- VMware/Virtual PC Allowed
WLVM:
- SHARK32 (Black, Red)
- PUMA32 (Black, Red)
- EAGLE32 (Black)
Happy reversing :3
- 250 Downloads
Bang1338Submitted -
A follow up of TinyCrackMe
Challenge:
- Press the button "Hi"
- If correctly bypass, a MessageBox with `:3` show up.
Rules:
1. Patch? Here's a deal:
- No patching if you're unpacked UPX, as final result!
- Allowed patching if you're not unpacked UPX, as final result!
- only patch-fix the flaw like missing stdc dll, or temporary byte patch to making loader or hook
2. Spoiling? Yes! (originally in crackmes.one is "no")
3. Keygen? useless. Because the goal is bypass it!
4. Hooking? Allowed! It's not a patch!
5. Loader? Allowed! It's just a mem patch, not file patch...
6. Any these above, do not use any tool to create stuff like Baymax or dUP2, but you can create your own one with coding.
Happy Reversing :3
- 52 Downloads
Bang1338Submitted -
The program uses VMP protection, and calls the relevant checksum SDK, even if the violent crack may also be slightly more complex, here provides a baymax patch tool to achieve the crack program, interested friends can read the pdf tutorial.
The function of the program to determine whether the input is correct or not does not use the SDK for protection, and verify the error dialog box strings are searchable, but these do not mean that it is easy to crack, because the code also calls the memory checksum, determine whether the debugging and other SDK interfaces. So how to realize the cracking of this crackme?
Baymax Patch App Protected by VMP is a PDF file, The detailed cracking process is explained above and can be consulted if you encounter difficulties while analyzing it. The PDF is divided into two volumes, the lower part can be downloaded from the Authors Solution section.
Attached is the source code of crackMe, the bpt file is the corresponding crack project of baymax64, you can use baymax tool to generate the corresponding patch file to test and verify the effect.
Baymax Patch App Protected by VMP (pdf file).zip.001 CrackMe Source Code.zip
- 173 Downloads
NisyUpdated -
This is a demo of the packer.
Demo is to find a password. (used simple anti-debugging and code-virtualization.)
Thank you
- 360 Downloads
0x777hUpdated -
License User Details
User Name=2days Tuts4you
Company=The Terminator
Hardware ID=6FF7-E7EF-5988-20FE-144E-865D-2D30-A73B
Custom Data=<custom_start>Skynet, a global network of artificial intelligence machines.<custom_end>
License Restrictions
Days Expiration=365
Date Expiration=2029/12/12
Executions=999
Runtime execution=999
Global Time=999
Install Before Date=2029/01/01
Miscellaneous
Unicode License=yes
Generated License (FILE KEY)
License Format=Binary
License Data= <license_start>
ghO1ud4wf14YNU87wUptZ1JTofTFErVAD+IwWKEjB/fxOtba9Vt0uasw45jdF3Yr9eGcJ/6h6lfad3d/MMYzxXYP7OZVGfHctljzMWS4H13UVl3DWBgWzCeozgy9k1UlULrL3/oKL/VdiS/BOJC98IgsF5+XT80xyGxos+Hcs4YdRarI9t0tj/+asJhpgN2KAXvH6lfp8qp0uvwZQUcnw/u+SpQjssOF5aAP9Bwweuw+6nfGxrZGcy8aNK3Kqo7rI5rLPk9Mzo1U0WkS1/I8lpQS1Mtticm1Am/eZCiCHJDMXDEfgTEuLGhQ9AItQtLQ2Fn8egx786AbJM09OEdiz5aGhz3kZfJZz8djMG3g8222gCmmDty8G4pBttMefKkVjKHoI2UXboNHpoOpxi53F6jldAhh3t+JoaOwa3Ng51uTfoNc2kLlCCP+jrjchZUNN9MY8y3kQ4K0Hd6eNkPAXwqbl2kakLZOlsmkkkVi9Pg620SzOt6YHh9iV1rS+TZ0jzWMvC9IakEgJionxYShgLg1Qkv6o4qIzP2ri9lMpM5eJK9Zo+Yl6K9HLnJ/gOE97Op7iAlywjsol5sunCIROe4pLHZo0PDNFJNZ4yy1VEgHp2+Qy/0nP55Fc8845MkE4hrjpg7SOFphFILgTuGVPG97nhRDTi05+f50WE2rl5PpuXnmeBblgD7S87p2tHUO7o2t8kvI/z7Xd9xNfw4HYJcbztKPxAkamUdIl0jmnhdIRGJMlYZm7rBgLd6dYhEu6Lo8P5vi7tydId4QsuwC7tv6+F8CQ1n6HpXSoPowKuMI/L2Zg1Ry3jlS2KUvH4spGy3URvJ8e2rFaDZpmQ==
<license_end>
File Information
Platform: Windows
Bits: 64-bit
Type: Executable (Standard)
Version: 1.0.0.2
Modified: 8/1/2023 12:09:04 PM
Protection Macros
Virtual Machine: 10
Mutate: 0
String Encrypt: 6
CheckProtection: 2
CheckCodeIntegrity: 0
CheckVirtualPC: 1
CheckDebugger: 1
Unprotected: 0
CheckRegistration: 0
Registered: 0
Unregistered: 0
WinLicense x64 (version 3.1.3.0)
Unit_bypassme.pas- 391 Downloads
 2daysSubmitted
2daysSubmitted
Download Statistics
- 2,163 Files
- 354 Comments
- 894 Reviews
-


.thumb.png.284f9c27699a22deec6350de6b564b9c.png)