Tools & Utilities
Numerous RCE related tools and utilities...
58 files
-
unDUP2 unpacker v0.3 | python to C++ port by Stingered (2026)
Usage:
Extract and dump the .dup2 and payload DLL to disk from a generated PE created by dUP 2.
The .dup2 file can be loaded into diabl2oo2's Universal Patcher tool for editing.
Sample output:
ndup2 MyPatcher.exe
unDUP2 unpacker v0.3 | python to C++ port by Stingered (2026)
original python code: https://github.com/BakasuraRCE/UNdUP2
Usage: unDUP2.exe <file name>
[+] Generated: MyPatcher.dumped.dll
[+] Generated: MyPatcher.dUP2
(2 modules)
*original python code: https://github.com/BakasuraRCE/UNdUP2
Note: As of now, this only works on Patchers, not Loaders generated by DUP2.- 48 Downloads
 StingeredUpdated
StingeredUpdated -
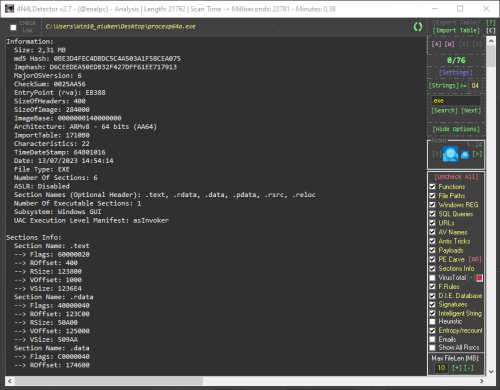
This is a scan tool for Microsoft Windows executables, libraries, drivers and mdumps. Its main objective is to collect the necessary information to facilitate the identification of malicious code within the analyzed files. This tool analyzes, among other things, the PE header and its structure, the content of the sections, the different types of strings, among many other things. It also incorporates a multitude of its own ideas to recognize anomalies in the construction of files and the detection of mechanisms used by current malware.
Using the tool is simple, just configure the options in the drop-down panel on the right and drag the samples into 4n4lDetector.
Full support:
- 32 bits (8086, x86, ARMv7)
- 64 bits (AMD64, x86-64, x64, ARMv8)
TI and ET Extraction:
Alpha AXP, ARM, ARM Thumb-2 (32-bit Thumb), ARM64, EFI Byte Code, EFI Byte Code (EBC), Hitachi SH3, Hitachi SH3, Hitachi SH4, Hitachi SH5, Intel i860, Intel Itanium (IA-64), M32R, MIPS16, MIPS16 with FPU, MIPS R3000, MIPS R4000, MIPS with FPU, MIPS little-endian, MIPS little-endian WCE v2, x64, x86, x86-64.
Buttons code:
- Buttons colored green are action buttons that open files and folders or are used to interact with the tool's utilities.
- The buttons colored in red perform reconfigurations, deletion of data or reset of functional files.
- Purple buttons announce the activation of online interactions.
- The pink buttons are shortcut buttons that the tool uses as tabs to navigate between different types of utilities.
Shortcuts:
- [A] Main analysis tab
- [W] Analysis tab in modifiable HTML format for report (WebView)
- [S] Viewer of strings extracted from the parsed file
- [V] Module with the Virustotal report using its API
Detections:
- PE Information
- Unusual Entry Point Position or Code (Algorithms, Anomalous Instructions... )
- Packers
- Compilations
- Binders/Joiners/Crypters
- Architectures
- Possible malicious functions
- Registry Keys
- Files Access
- Juicy Words
- Anti-VM/Sandbox/Debug
- URLs Extractor
- Payloads
- AV Services
- Duplicate Sections
- IP/Domains List
- Config RAT (Only In Memory Dumps)
- Call API By Name
- Unusual Chars In Description File (Polymorphic Patterns)
- Rich Signature Analyzer
- CheckSum Integrity Problem
- PE Integrity Check
- SQL Queries
- Emails
- Malicious resources
- PE Carve
- Exploits
- File Rules for Entry Points and more... 😃
Console Options (Analysis to file):
- 4n4lDetector.exe Path\App.exe -GUI (Start the graphical interface parsing a file from the console)
- 4n4lDetector.exe Path\App.exe -GREMOVE (Remove binary after scan)
- 4n4lDetector.exe Path\App.exe -TXT (Parse a file from the console and the output is written to a TXT file)
- 4n4lDetector.exe Path\App.exe -HTML (Parse a file from the console and the output is written to HTML file)
- 300 Downloads
- 5 Comments
 4n0nym0usUpdated
4n0nym0usUpdated -
============================ AT4RE Power Loader v0.1 (Release Date: 26/03/2025) ============================
[+] Console interface
[+] Loader Coded in C++ with CRT (big Size: 85 KB when compressed about 190 KB uncompressed).
[+] Supports patching single or multiple Relative Virtual Addresses (RVAs).
Root Folder Contents:
[+] ATPL.EXE (AT4RE Power Loader)
[+] Version History.txt
============================ AT4RE Power Loader v0.2 (Release Date: 16/04/2025) ============================
The most powerful loader against strong and hard protectors.
It also works with medium-level protectors, packers, compressors, and even unprotected executable files.
Main Features:
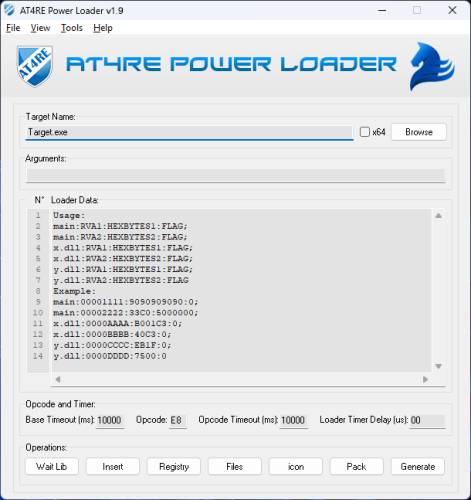
[+] GUI Coded in Borland Delphi 7
[+] From the GUI, you can browse to select the target file (maximum filename length is 255 characters).
[+] You can also copy and paste the file name into the input field.
[+] Choose between x32 and x64 loader versions.
[+] Loader data can be entered only in the format shown in filed or in the screenshot.
[+] Set a base timeout in milliseconds (Minimum: 00, Maximum: 9999 — i.e., 9.99 seconds).
[+] Set 1-byte opcodes in the Opcode field using HEX characters (Opcode is the Original First Byte of RVA1).
[+] Configure Opcode Timeout in milliseconds (Minimum: 00, Maximum: 9999 — i.e., 9.99 seconds).
[+] Set the Loader Timer Delay in microseconds (Min: 00, Max: 9,999,999 — i.e., 9.99 seconds).
[+] Configure the loader to start as Administrator.
[+] Directly pack the loader with UPX.
[+] Generate Loader.exe
[+] Save or open projects for future use from File menu.
[+] Set the GUI to "most on top" from the View menu.
[+] Access the official website, report bugs, and find more information via about in the Help menu.
Loader Details:
[+] Coded in C++ using the Windows Pure API.
[+] Loader size is 10 KB uncompressed, and 5 KB when compressed.
[+] Supports Windows 7, 8, 10, and 11 (both x32 and x64).
Features include:
[+] Anti-ASLR
[+] Anti-Anti-Debug
[+] Anti-CRC Check
[+] Automatically detects the base address.
[+] Detects when the protector unpacks code into memory.
[+] Can apply temporary patches after a specified delay in microseconds (Patch and restor original bytes).
[+] Can apply permanent patches only with 00 Flag
[+] Supports patching single or multiple Relative Virtual Addresses (RVAs).
[+] Capable of patching up to 2048 bytes.
[+] Can run as Administrator or Normal user mode.
Root Folder Contents:
[+] Project folder (Save or open projects for future use)
[+] UPX folder (includes upx32.exe and upx64.exe)
[+] ATPL.EXE (AT4RE Power Loader)
[+] Version History.txt
============================ AT4RE Power Loader v0.3 (Release Date: 10/05/2025) ============================
The most powerful loader against strong and hard protectors.
It also works with medium-level protectors, packers, compressors, and even unprotected executable files.
Main Features:
[+] Added Support Patching DLLs (Only DLLs Loaded by Target.exe).
[+] Added Drag Drop Feature: For .EXE, .REG, .ICO Files.
[+] Added Insert Loader Data feature (For Respect the Correct Format).
[+] Added Registry Keys Manager (Max size: 1 KB / 1024 characters).
[+] Added Delete Files feature (Max size: 1 KB / 1024 characters).
[+] Added Icon Changer.
[+] Added New Project option from File menu (Clears all fields).
[+] Added Commands Shortcut Ctrl+N, Ctrl+O, Ctrl+S in File menu.
[+] Added Contact Us section from Help menu.
[+] Updated About from Help menu from box to a form.
[+] Updated display fonts for Loader Data, Registry, and Files.
[-] Removed "My Target run as admin".
Loader Details:
[+] Size is now 17 KB uncompressed, 7 KB when compressed.
[+] Loader now Support Patching DLLs (Only DLLs Loaded by Target.exe).
[+] Loader can now add or delete registry keys.
[+] Loader can delete files.
[+] Automatically requests Run as Administrator when needed
(e.g.,Target need administrator privilege, modifying registry or deleting files from protected folders).
[+] Icon support added.
Root Folder Contents:
[+] Icons folder (includes 5 icons).
[+] Lib folder (includes bass.dll).
[+] Project folder (Save or open projects for future use).
[+] ResH folder (includes ResHacker.exe).
[+] UPX folder (includes upx32.exe and upx64.exe).
[+] ATPL.EXE (AT4RE Power Loader).
[+] Version History.txt
============================ AT4RE Power Loader v0.4 (Release Date: 16/05/2025) ============================
The most powerful loader against strong and hard protectors.
It also works with medium-level protectors, packers, compressors, and even unprotected executable files.
Main Features:
[+] Added Import menu.
[+] Added Support .1337 patch files exported by x64dbg.
[+] Set Opcode automatically when Load .1337 file.
[+] Added OpenDialog when Double Click on:
- Target Name field.
- Loader Data field.
- Registry field.
- Custom icon field.
Loader Details:
[+] Fixed bug with registry feature.
[+] Default icon changed.
[+] Compressed Loader with Default icon 8 KB.
Root Folder Contents:
[+] Icons folder (includes 5 icons).
[+] Lib folder (includes bass.dll).
[+] Project folder (Save or open projects for future use).
[+] ResH folder (includes ResHacker.exe).
[+] UPX folder (includes upx32.exe and upx64.exe).
[+] ATPL.EXE (AT4RE Power Loader).
[+] Version History.txt
- 813 Downloads
- 65 Comments
 m!x0rUpdated
m!x0rUpdated -
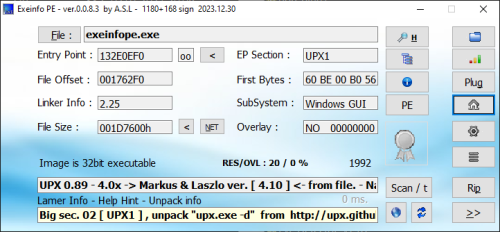
If you need to view information about various EXE files, Exeinfo PE is a small toll that does exactly that. It can analyse EXE files and acquires detailed information about their properties, offering you the possibility to save overlays and create backups.
The application is portable so you don’t need to install it, plus your Windows registry will remain unchanged.
The simple interface has a plain window where you can drag and drop an EXE or DLL file, or load it via the built-in file browser. Then the application will display the file size, file offset, entry point, linker information, EP section, sub-system and overlay. Furthermore, you can also insert HEX data to analyse BIN information.
A section viewer can be opened, where users can see every virtual offset and size, flags, name, RAW data offset and size, first bytes and section status. Header information is also available such as security, debug, exception, T:S table, size of headers, number of directories and so on.
The application can be set to perform a fast scan from the Options menu. Moreover, from the same place, you can configure Exeinfo PE to ignore EXE errors, set it to be always on top, choose the big interface or integrate it into the shell.
Plugins:
https://github.com/ExeinfoASL/plugins
Support Topic:
https://forum.tuts4you.com/topic/8412-exeinfo-pe/- 1,136 Downloads
- 8 Comments
 A.S.LUpdated
A.S.LUpdated -
Remote Process Injection allow load dll to target entry point process .
process remote injection 1.0.zip
- 47 Downloads
- 10 Comments
 TeerayootSubmitted
TeerayootSubmitted -
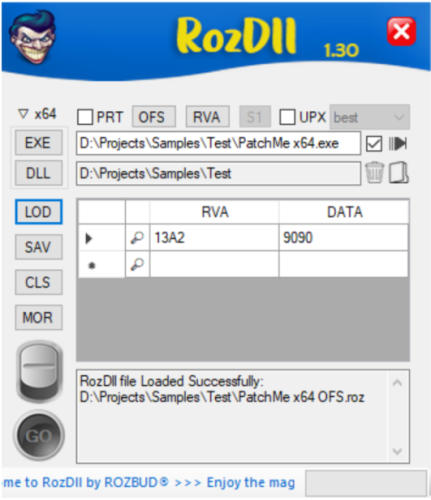
Provision:
Create a tiny Proxy DLLs for Personal researches.
RozDll Vs Fixit:
Fixit is a “Static Load Generator”. Handles Pre-Generated List of DLL's that may be work with your Executable or not (same as ByMax).
RozDll is a “Dynamic Load Generator”, runs your Executable in Memory, gets a list of Proxy DLL's which your Executable uses in Memory.
RozDll Main Features:
Generate Fast, Portable & Small Size Proxy/Hijacked DLL. Integrated with x64dbg. You can load the Patched Data directly from x64dbg exported file (*.1337). Dynamic Loading. Function Selection. Deferent Method of patch Options. Encryption: DLL Function Names are Encrypted. This will make it difficult for Anti-Virus to trace generated DLL. Startup Message: You can personalize your work by writing your name and short info/about. This message will appear only at the first run of target executable. Data Extraction: Upload Registry and other filetypes into target PC. Data Verification: Clicking on the 'Magnifier symbol' is mandatory & it will ensure that you entered the correct data. Created on Windows 10 & Visual Studio 2022. It should work on Windows 10 & Windows 11, but not guaranteed to work in Virtual Windows. Tutorial:
RozDll_Advanced.mp4
RozDll_Final_Tutorial_(v1.30).mp4
- 585 Downloads
- 1 Comments
 Teddy RogersUpdated
Teddy RogersUpdated -
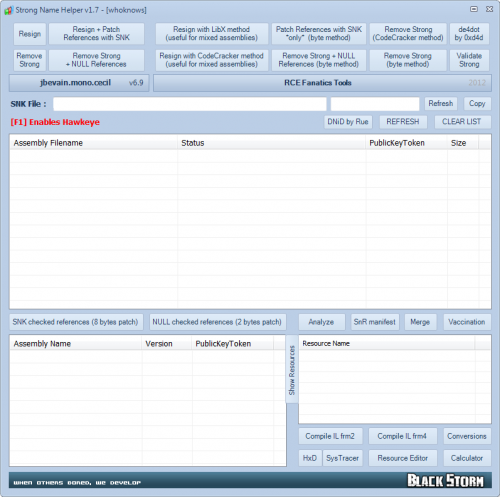
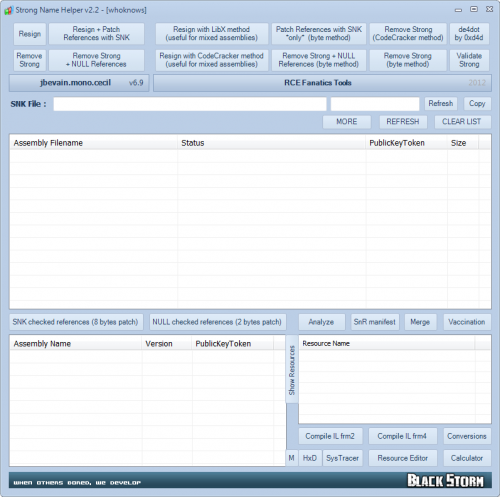
Bundle of .NET tools!
Main reason is to defeat strong name validation, on the other hand third party tools merged!
ACorns.Hawkeye
Is the only .Net tool that allows you to view, edit, analyze and invoke (almost) any object from a .Net application. Whenever you try to debug, test, change or understand an application, Hawkeye can help.
CFF Explorer-NTCore
Designed to make PE editing as easy as possible, but without losing sight on the portable executable's internal structure.
HwndSpy-dp0
Is an invaluable tool for developers doing maintenance on GUI applications, where they first need to understand the windows hierarchy and how the windows are structured.
HxD-Mael Horz
Is a carefully designed and fast hex editor which, additionally to raw disk editing and modifying of main memory (RAM), handles files of any size.
Mono.Cecil-Evain
Is a library to generate and inspect programs and libraries in the ECMA CIL format.
Procmon-SysInternals
Is an advanced monitoring tool for Windows that shows real-time file system, Registry and process/thread activity.
Resource2+4-fish
Is a utility to easily refresh embedded resources in a .NET assembly. ResX Schema(*.resX), Embedded Resource(*.resources), Import/Export/View/Edit/Translate embedded resources, Text/Icon/Bitmap/Cursor/String/ImageListStreamer/PinnedBufferMemoryStream (v4)...
SysTracer-blueproject
Is a system utility tool that can scan and analyze your computer to find changed (added, modified or deleted) data into registry and files.
de4dot-0xd4d
Is an open source .NET deobfuscator and unpacker written in C#.
Assembly_Resigner-CodeCracker
StrongName_Killer-CodeCracker
- 1,447 Downloads
 whoknowsUpdated
whoknowsUpdated -
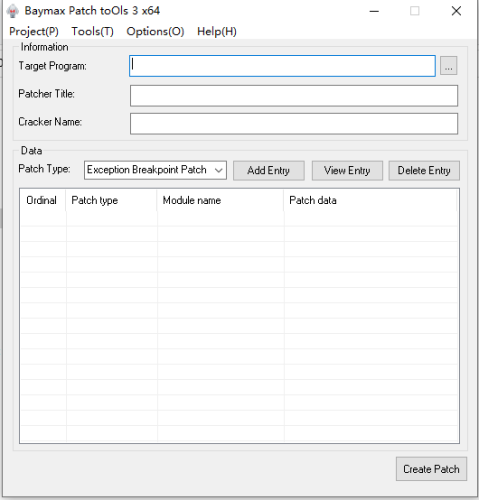
Baymax Patch Tools v3.1.0
Tool description:
Baymax Patch Tools is a hijacking patch making tool that releases a hijacking DLL for the target process to load the function module PYG. Two patching functions are supported.search and replace patch supports feature code search and replace memory data, exception breakpoint patch supports simulating the exception breakpoint function of debugger and modifying register, memory and other data after setting and triggering breakpoint to achieve the purpose of modifying program execution flow and so on.
The tool is protected, antivirus may misreport the tool and patch files! Due to the use of the shell SDK, all components of the tool (including the generated patches) do not contain networking capabilities! The generated patches will not modify any files on the system when running (except for overwriting patch files). The generated patches will not modify any files on the system when running (except for overwriting patch files). The tool itself has a verification mechanism and will load only after the module is successfully verified at startup, but for security reasons, please be sure to download and use it from the official site.
Function introduction:
. support hijacking crack, not modify the file itself
. support for patching processes with dynamic base addresses (ASLR)
. support patching multiple DLL modules of the target process
. support patching different EXEs of the same patch
. support patching the memory data of a process at a specified address
. support for patching processes using feature code matching
. support setting API HOOK decoding for shelled programs before patching data
. support patching data after setting hardware breakpoint interrupt for the process
. support setting exception breakpoints to modify the memory pointed to by registers or registers after interrupting the process
. support setting conditional breakpoints for processes to determine whether to execute Patch according to the number of interrupts, . . . . register or memory values
. support setting different conditional breakpoints for the same address to perform Patch on the interrupts that meet the conditions
. support extracting global variables from assembly instructions to store and modify them
. support for storing data and using stored data during process execution
. support patching the memory pointed to by the memory marker after interrupt
. support basic operations on data after interrupt
. support for reading patch data from ini file
. support to create memory keymaker
. support for creating debug patches to troubleshoot patch problems by yourself
Update:
2023.01.18
x86 v3.1.0
1. Support multi-language function
2. adjusted and optimized the UI, text descriptions, etc. to improve the interactive experience
Download:
https://sourceforge.net/projects/baymax-patch-tools/
- 1,816 Downloads
- 9 Comments
 wgz0001Updated
wgz0001Updated -
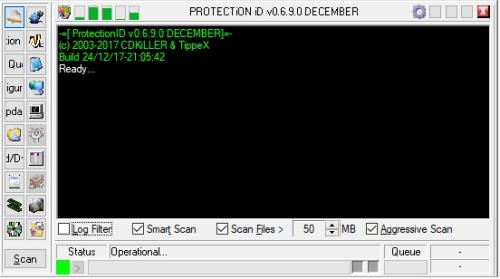
ProtectionID is a software tool commonly used in the reverse engineering and software cracking community to analyze and identify the copy protection and DRM (Digital Rights Management) schemes used in executable files. It can detect various types of protections, such as anti-debugging, anti-tampering, code obfuscation, and encryption. ProtectionID can also provide information about the file's structure, imported and exported functions, and other relevant data. The tool is useful for software developers and security researchers who need to understand how copy protection works and for those who seek to crack software and remove the copy protection. However, it should be noted that using ProtectionID for cracking purposes is illegal and violates copyright laws.
- 2,035 Downloads
CyborgUpdated -
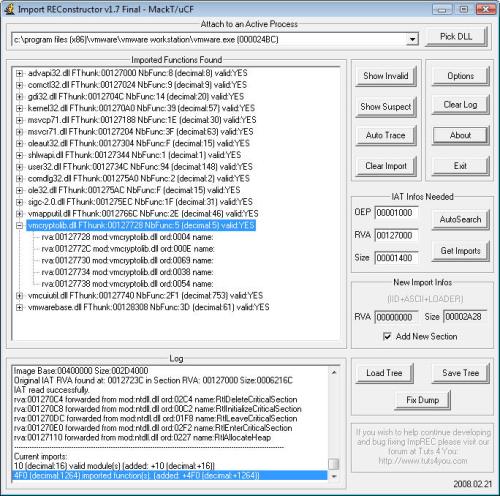
This tool is designed to rebuild imports for protected/packed Win32 executables. It reconstructs a new Image Import Descriptor (IID), Import Array Table (IAT) and all ASCII module and function names. It can also inject into your output executable, a loader which is able to fill the IAT with real pointers to API or a ripped code from the protector/packer (very useful against emulated API in a thunk).
Sorry but this tool is not designed for newbies, you should be familiar a bit with manual unpacking first (some tutorials are easy to find on internet).
- 2,921 Downloads
 Teddy RogersUpdated
Teddy RogersUpdated -
Convert ollydbg,x64dbg binary copy code format to c++ ,c format
CppCLR_WinformsProjekt1.exe- 356 Downloads
- 2 Comments
 SuperJackAbcdUpdated
SuperJackAbcdUpdated -
PinMe! allows setting individual windows to TopMost (window always on top) with the following additional features;
Setting windows to TopMost / NoTopMost Changing window transparency levels Window captures and region captures Desktop captures (foreground and background) Basic window statistics Window information; dimensions, sizes, styles, etc. Installation
As of version 0.8.9 PinMe! runs on Windows 10 (Build 14393) and later, including Windows 11.
Extract PinMe! from the archive and copy to a directory from where it can be run.
If you want to have PinMe! run at each startup click on the "Run at Start-Up" option in the menu. A copy of PinMe! will be saved to the Windows "Startup" folder.
TopMost / NoTopMost
A list of all open and visible windows are shown in Z-Order from the click of the tray icon. Selecting a window positions that window to TopMost (always on top/pinned) and now the highest in Z-Order. If you select a window that has already been given TopMost it will set it to NoTopMost (normal).
When more than one window is TopMost, the TopMost windows will take hierarchy in the order which you selected them. The first TopMost window will go to the bottom and recent to the top. TopMost windows will show up with a locked icon next to them in the menu. Normal windows will have their default window or system icon.
If a window you want to set to TopMost or NoTopMost is not shown in the menu list of windows you can use customised shortcut keys, found in Preferences menu, whilst the window is active.
Window Monitor
As of version 0.9.3 PinMe! contains a frequently requested feature to "Monitor" certain windows and automagically set them to TopMost.
When a window is being monitored PinMe! will remember the window(s) and, for example, after a restart set those windows to TopMost again.
One of the caveats with this feature is if you were to monitor a Notepad window all subsequent opened Notepad windows will be set with TopMost.
Feedback on this feature is warmly welcome.
Window Transparency
There are two ways to change the transparency of a window. The first it to find the window in the menu list and from the, "Window Transparency", submenu set the desired level of transparency between 10% to 100% viewable.
If the window you want to set the transparency level of is not in the window menu list use the second method. From "Tools Menu..." menu select, "Enable Window Transparency". Once the setting has been activated you should see the same menu option now listed as, "Disable Window Transparency". Move the mouse cursor over the window you would like to change the transparency level of and scroll the mouse wheel until the transparency is at the desired level. Moving the mouse to other windows and scrolling the mouse wheel will change the transparency level of those windows until you go back to the tools menu to disable the feature.
Whilst this option is activated mouse scroll wheel messages are not passed to the window until this option is disabled, scrolling through a page in a browser or document for example will not be possible.
Capturing Windows
You can capture the contents of a window in each windows submenu. PinMe! will try to capture the window image even if it is located behind other windows. If it is unable to do so PinMe! will attempt to bring that window to the front before capturing.
Images can be saved in either .PNG, .JPG and .BMP., the image is also copied to the clipboard if you have the option enabled in Preferences.
Capturing Screens & Desktops
You can capture whole screens, desktop foreground and background. By going to, "Tools Menu...", you will find a submenu titled, "Capture Display Devices...". The submenu will contain a list of all the display devices currently connected and active including two options titled, "Capture Desktop Background", and, "Capture Desktop Foreground". To capture a screenshot simply select the appropriate display device and a save dialogue will appear to allow you to save the captured image to a folder.
The following options capture the entire desktop across all monitors/displays:
Capture Desktop Background, captures all of the desktop background across all display devices without any of the windows on top. Capture Desktop Foreground, captures all windows on top of the desktop across all display devices. Images can be saved in either .PNG, .JPG and .BMP., the image is also copied to the clipboard if you have the option enabled in Preferences.
Region Captures
Region capture can be activated by selecting, "Tools Menu...", then, "Enable Region Capture". Once you are in region capture the display will turn a slightly different colour and the mouse cursor will change to a cross hair with a square magnified window next to it.
There are two methods for selecting the capture points. The first is to click and hold down the mouse pointer at the start position and drag the mouse pointer to draw a rectangle over the area of screen you would like to capture. You will notice a coloured rectangular box will be created, this is the region that will be captured. The second method is to left mouse click at the first capture point then left mouse click at the second capture point. You will notice the cross hair will stay active at the first location, this helps you correctly size the corners of the rectangle you wish to capture.
To help you capture the correct region a magnify window is available. Inside the magnify window information will display the x and y coordinates of the cross hair position. A colour picker in the top right hand corner is displayed. The top left hand side shows the zoom factor which, you can change by scrolling the mouse wheel to zoom in and out of the image.
After selecting a capture region the save dialogue automatically appears. Images can be saved in either .PNG, .JPG and .BMP., the image is also copied to the clipboard if you have the option enabled in Preferences.
Exiting from region capture can be done by pressing the right mouse button.
Depressing the wheel mouse button at any time during a capture will cause the mouse to move at slow speed. This may help in correctly aligning the capture cross hairs.
Pressing the "SHIFT" key after the first cross hair has been set will delete it.
Power Management
There are three settings in the power management menu, these are to prevent the monitor or system from sleeping;
1) Prevent Display Sleeping
2) Prevent System Sleeping
3) Enable Away Mode
Window List
Window List displays all the windows on the current desktop including child windows in tree like hierarchy. There are options to filter for certain types of windows; Top-Level, Immersive, Store Apps, Children, Threads. Each entry is listed using its window handle and classname.
Double clicking on a window allows you to open the Window Information window to view its details.
Window Information
Provides information on the window details including dimensions and certain capabilities. For Store Apps there is a separate tab detailing basic package information.
There is a menu option here that allows you to point at a window using the mouse cursor to view its details.
Window Controls
Under each windows menu there are options to send messages to the window to; Close Gracefully, Close Forcibly, Restore, Zero, Maximise, Minimise.
Shortcut Keys
In the Preferences menu you will find two options for customising shortcut keys to start region capture and set an active window between TopMost and NoTopMost. To configure this click in one of the shortcut fields and then select the key combinations you would like to use. If the key combination was successful the shortcut description will be set. An error message will prompt you if PinMe! was unable to do this, likely because the key combination has already been registered by another application.
Run At Startup
You will only see this menu option if PinMe! is not already running from the Windows startup folder.
When selected PinMe! will be copied to:
C:\Users\Username\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup To update either;
manually copy a new version to the startup folder or, whilst the new version of PinMe! is running (from another folder) select this option to overwrite the existing file. Run As Administrator
Introduced in Windows Vista and used with subsequent editions, the Windows OS comes with a security feature called User Account Control - or UAC for short. UAC prevents programs and applications running with elevated (Administrator) privileges to help protect the operating system from being compromised by malicious software. By default PinMe! does not request elevated privileges. Because of this PinMe! may not by able to send messages to communicate a change of window state to a program that is running with higher privileges than PinMe!. This is due to another security technology called User Interface Privilege Isolation (UIPI).
If you find that PinMe! is not changing the state of a particular window you can request PinMe! to run in Administrator mode by going to, "Tools Menu...", menu and selecting, "Run As Administrator", which will let PinMe! run with high integrity. Once activated Windows will prompt you with a User Account Control dialogue asking if you want to allow PinMe! to make changes to the computer. Click yes if you do. Once PinMe! is running with high integrity in Administrator mode PinMe! will be able to send messages and communicate with those windows.
Preferences
Here is a quick overview of other available options, not mentioned above, in the Preferences menu that allow you to enable or disable features:
Sounds sound prompts and warnings. Clipboard saving of captures to the clipboard. Save Dialogue save dialogue prompt after captures. Repeat Capture continue to the next region capture after saving. Magnify Window enable or disable the magnify window. Language Files
Upon startup PinMe! will try to determine the users interface language then search for that regions language file in the "Language" subfolder where PinMe! executable is located. All language files begin with, "lang_", suffixed by a three letter ISO language name for the region. E.g. for a user in Thailand using Thai language PinMe! will search for, "lang_tha.txt". If a language file is unable to be located PinMe! defaults to it's built in English language. PinMe! conforms to ISO 639-2 three-letter code for the language file suffix name. If you wish to create a language file for your region you can find your language prefix listed at Wikipedia:
https://en.wikipedia.org/wiki/List_of_ISO_639-2_codes
The language file must be saved in UTF-8. If for some reason your language is displayed incorrectly within PinMe! please try saving the file as UTF-8 with BOM (byte order mark).
- 4,724 Downloads
 Teddy RogersUpdated
Teddy RogersUpdated -
SmartCheck is a run-time debugging tool that addresses the most problematic conditions encountered by Visual Basic developers:
Fatal run-time errors that are cryptic and hard-to-solve Problems that result from a sequence of events Incorrect Windows API Usage from Visual Basic Bad values passed to built-in Visual Basic functions Problematic value coercions Errors in components, such as ActiveX controls, used by your program How SmartCheck Works
As you run a program (EXE), SmartCheck runs in the background monitoring it continuously, and capturing program events and errors. During program execution, you have the option to disable and enable event reporting at will. This allows you to capture information relevant to testing your program, while eliminating the overhead of unnecessary event reporting.
The information captured by SmartCheck can be viewed in a Program Results window, either during or after running a program. You can also save a session’s log file for later review.
SmartCheck automatically searches for errors in your program executable as well as the dynamic-link libraries (DLLs), third-party modules, and OLE components used by your program. It can also find errors in programs for which you do not have source code, though we recommend that you have source code with debugging information to maximize error detection and diagnosis.
SmartCheck checks all API calls, memory allocations and deallocations, Windows messages, and other significant program events for errors such as:
Common memory errors, including memory overruns and memory leaks Resource leaks, including Windows-specific handles Windows-specific errors in Win32APIs, ODBC, DirectX, and COM/OLE APIs- 2,126 Downloads
- 2 Comments
 Teddy RogersUpdated
Teddy RogersUpdated -
This is a complete collection of public and private builds of Imports Fixer (mainly a collection of private builds). I am uploading all of these for posterity reasons before they are deleted and for those people who like to look over this stuff.
Most of these old builds will not work on modern Windows OS's and IF is no longer being developed so do not expect them to function correctly.
If you need to use an imports fixer I suggest turning to a publically accessible imports builder such as Scylla. It is more feature complete, supports modern OS builds and is open source - so you can fix any bugs.
In advance of questions regarding IFv1.7, this version was never completed and no private builds were released. Version 1.6 is where all the fun ended...
Ted.
- 1,526 Downloads
 Teddy RogersUpdated
Teddy RogersUpdated -
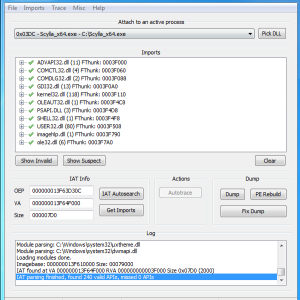
Scylla - x64/x86 Imports Reconstruction
ImpREC, CHimpREC, Imports Fixer... this are all great tools to rebuild an import table, but they all have some major disadvantages, so I decided to create my own tool for this job.
Scylla's key benefits are:
x64 and x86 support full unicode support written in C/C++ plugin support works great with Windows 7 This tool was designed to be used with Windows 7 x64, so it is recommend to use this operating system. But it may work with XP and Vista, too.
Source code is licensed under GNU GENERAL PUBLIC LICENSE v3.0
https://github.com/NtQuery/Scylla
https://github.com/x64dbg/Scylla
- 5,499 Downloads
- 1 Comments
AguilaUpdated -
This is a professional PE file explorer that lets you dig into all data directories available in the PE/PE64 file and edit them.
Export, Import, Resource, Exception, Certificate(Relies on Windows API), Base Relocation, Debug, TLS, Load Config, Bound Import, IAT, Delay Import and CLR are supported.
Two companion plugins are also provided. FileInfo, to query the file in the well-known malware repositories and take one-click technical information about the file such as its size, entropy, attributes, hashes, version info and so on. YaraPlugin, to test Yara rules against opened file.
Puppy is robust against malformed and crafted PE files which makes it handy for reversers, malware researchers and those who want to inspect PE files in more details.
Puppy is free and tries to be small, fast, nimble and friendly as your puppy!
Website: https://www.mzrst.com/
- 2,213 Downloads
ZaderostamUpdated -
Bundle of .NET tools!
The development ended @ 2012 with v1.7. Main reason is to defeat strong name validation, on the other hand third party tools merged!
ACorns.Hawkeye
Is the only .Net tool that allows you to view, edit, analyze and invoke (almost) any object from a .Net application. Whenever you try to debug, test, change or understand an application, Hawkeye can help.
CFF Explorer-NTCore
Designed to make PE editing as easy as possible, but without losing sight on the portable executable's internal structure.
HwndSpy-dp0
Is an invaluable tool for developers doing maintenance on GUI applications, where they first need to understand the windows hierarchy and how the windows are structured.
HxD-Mael Horz
Is a carefully designed and fast hex editor which, additionally to raw disk editing and modifying of main memory (RAM), handles files of any size.
Mono.Cecil-Evain
Is a library to generate and inspect programs and libraries in the ECMA CIL format.
Procmon-SysInternals
Is an advanced monitoring tool for Windows that shows real-time file system, Registry and process/thread activity.
Resource2+4-fish
Is a utility to easily refresh embedded resources in a .NET assembly. ResX Schema(*.resX), Embedded Resource(*.resources), Import/Export/View/Edit/Translate embedded resources, Text/Icon/Bitmap/Cursor/String/ImageListStreamer/PinnedBufferMemoryStream (v4)...
SysTracer-blueproject
Is a system utility tool that can scan and analyze your computer to find changed (added, modified or deleted) data into registry and files.
de4dot-0xd4d
Is an open source .NET deobfuscator and unpacker written in C#.
Assembly_Resigner-CodeCracker
HeaderFixer-CodeCracker
NR_Bad_Net_Opcode_Remover-CodeCracker
StrongName_Killer-CodeCracker
Password to extract is bs
- 3,262 Downloads
 whoknowsUpdated
whoknowsUpdated -
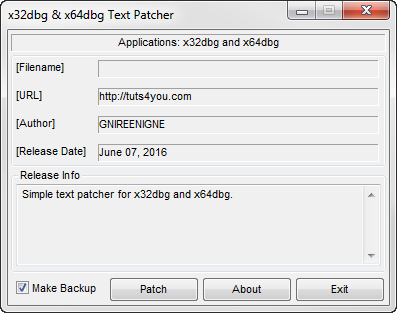
I was bored and tired of being reminded that I was wasting my life.
Here is a simple text patcher for x32dbg and x64dbg. Just drop the patcher in your x32 and x64 folders and run it.
Thanks!
- 630 Downloads
GNIREENIGNEUpdated -
- 583 Downloads
 Ali.DbgSubmitted
Ali.DbgSubmitted -
- 1,508 Downloads
- 1 Comments
 Ali.DbgSubmitted
Ali.DbgSubmitted -
Scylla Imports Reconstruction
ImpREC, CHimpREC, Imports Fixer... this are all great tools to rebuild an import table, but they all have some major disadvantages, so I decided to create my own tool for this job.
Scylla's key benefits are:
x64 and x86 support
full unicode support
written in C/C++
plugin support (ImpREC plugins are supported)
works great with Windows 7
Currently there are only 2 plugins (PECompact, PESpin x64) in this release, full sourcecode for both is included.
- 15,498 Downloads
- 1 Comments
AguilaUpdated -
hey guys
i create a program for serial sniff by vb6
esc features :
check crc(automatic)
unicode string
small size
background music
bypass packers
and .....
sorry for my english (im persian)
enjoy it
- 1,778 Downloads
 unknown021Updated
unknown021Updated -
snr.dup.search.and.replace.patchengine.sourcecode
ASM Code
- 723 Downloads
 Ali.DbgSubmitted
Ali.DbgSubmitted -
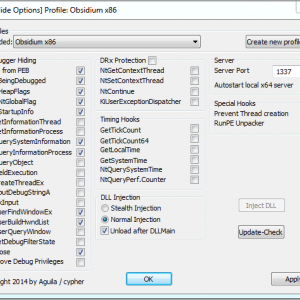
ScyllaHide is an advanced open-source x64/x86 usermode Anti-Anti-Debug library. It hooks various functions in usermode to hide debugging. This tool is intended to stay in usermode (ring3). If you need kernelmode (ring0) Anti-Anti-Debug please see TitanHide https://bitbucket.org/mrexodia/titanhide.
ScyllaHide supports various debuggers with plugins:
- OllyDbg v1 and v2 http://www.ollydbg.de
- x64_dbg http://x64dbg.com or https://bitbucket.org/mrexodia/x64_dbg
- Hex-Rays IDA v6+ https://www.hex-rays.com/products/ida/
- TitanEngine v2 https://bitbucket.org/mrexodia/titanengine-update and http://www.reversinglabs.com/open-source/titanengine.html
PE x64 debugging is fully supported with plugins for x64_dbg and IDA.
Please note: ScyllaHide is not limited to these debuggers. You can use the standalone commandline version of ScyllaHide. You can inject ScyllaHide in any process debugged by any debugger.
More information is available in the documentation: https://bitbucket.org/NtQuery/scyllahide/downloads/ScyllaHide.pdf
Source code license:
GNU General Public License v3 https://www.gnu.org/licenses/gpl-3.0.en.html
Special thanks to:
- What for his POISON Assembler source code https://tuts4you.com/download.php?view.2281
- waliedassar for his blog posts http://waleedassar.blogspot.de
- Peter Ferrie for his PDFs http://pferrie.host22.com
- MaRKuS-DJM for OllyAdvanced assembler source code
- MS Spy++ style Window Finder http://www.codeproject.com/Articles/1698/MS-Spy-style-Window-Finder
- 6,826 Downloads
AguilaUpdated -
This is my own coded jump calculator...
Coded specially for our team site but i will share it the members on this board.
It's simple as it is and nothing special. It's a simple jump calculator.
Fill the fields for "Jump From:" and "Jump To:" with a hex address and press the button "Calculate". Thats all...
Simple eh?
grEEtZ iNvIcTUs oRCuS
- 1,035 Downloads
- 2 Comments
 mAStEr pAInSubmitted
mAStEr pAInSubmitted
Download Statistics
- 2,165 Files
- 355 Comments
- 894 Reviews
-
.thumb.jpg.e41d4991c184d8bb48d24fc4610d7926.jpg)