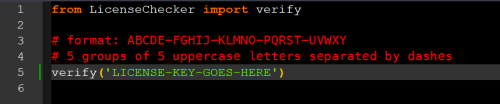
I have provided a zip archive which contains two .py files, as seen in the screenshot. In LicenseChecker.py there is a validation function invoked by main.py where you put the key in the given format.
The python code is obfuscated using a obfuscator I'm currently working on. If you solved the challenge, or have any feedback to give, or need hints/help with reversing without spoiling, please let me know. Thanks.
You can see original source code and the solution in the 'Authors Code' and 'Authors Solution', if you wish.
Good luck!
from sys import exit, gettrace, stdout
def encode(x):
out = 0
for i in (isinstance(x, str) and (x := bytearray(x, 'ansi')) or x):
out |= i
out <<= 8
return out >> 8
def decode(num):
out = bytearray()
while num:
out.append(num & 0xFF)
num >>= 8
return out[::-1]
def __exit(reason=0x4c6963656e736520636865636b206661696c65642120506c656173652074727920616761696e2e0a):
stdout.write(decode(reason).decode())
exit(1)
def verify(license_key='xd'):
import hashlib
import time
gettrace() is not None and __exit(0x536f7272792c206e6f2064656275676765727320616c6c6f7765642e0a)
try:
a1 = time.time()
len(license_key) == 29 or __exit()
len(p := license_key.split('-')) == 5 or __exit()
all(len(i) == 5 for i in p) or __exit()
a2 = time.time()
a2 - a1 < 0.5 or __exit()
hashlib.md5(p[0].encode()).digest() == b"\xfde\xbe'\n\x8b\xed\xb5\xf8\x16\xfb\x8aVqt4" or __exit()
p[1][1] == 'T' or __exit()
p[2][4] == 'S' or __exit()
p[3][1] == 'O' or __exit()
p[1][4] == 'A' or __exit()
p[1][2] == 'U' or __exit()
p[3][2] == 'H' or __exit()
p[2][0] == 'T' or __exit()
p[3][3] == 'F' or __exit()
p[1][0] == 'A' or __exit()
p[2][1] == 'I' or __exit()
p[3][4] == 'A' or __exit()
p[2][2] == 'O' or __exit()
p[1][3] == 'L' or __exit()
p[2][3] == 'N' or __exit()
p[3][0] == 'Q' or __exit()
(p[4] * 707)[::14][:5] == 'BHZQB' or __exit()
except SystemExit:
exit(1)
except:
__exit()
stdout.write(decode(0x4c6963656e736520636865636b2073756363657373212057656c636f6d65210a).decode())
stdout.write(decode((((((((16869737 << 25) + (13763846)) << (50)) + (((32403084) << (25)) + (22611992))) << (99)) + (((((20746294) << (25)) + (24474465)) << (49)) + (((15516350) << (24)) + (14996164)))) << (199)) + (((((((27626884) << (25)) + (17005425)) << (50)) + (16005976712847)) << (99)) + (((((24081710) << (24)) + (6516589)) << (48)) + (((4217434) << (23)) + (2957322))))).decode())
globals()['verify'] = verify
Correct license key is: CONGR-ATULA-TIONS-QOHFA-BBQZH
First part, CONGR is hashed with md5, which can be easily reversed by online crackers
Parts two, three and four are equality checked
The last part is shifted a bit and then verified.

Recommended Comments