Hello,
Since the use of vm's is quite popular in .net obfuscation I thought it would be interesting to make one in Python. Hereby I release my first crackme using my VM. It's a very simple VM so it shouldn't be that hard to reverse with the right knowledge.
This is purely experimental to see if it would be useful somehow. I also used my own protector that adds cflow, so expect to see a lot of jumps.
Goal: Patch it (ultimately devirtualize it, but that's not necessary)
EDIT: This is now updated. I tried to make sure it isn't possible to patch with 1 or 2 jumps.
Edited by svenskithesource
Update
What's New in Version 05/23/2022 04:23 PM
Released
No changelog available for this version.
_ =621573266
while True :
if _ ==-451749950 :
b =a .split ("0x")[-2161194422 ^ (0b1010011110111010011101011101001 % -0b111101100100001001010011001011 - 0o13143243410) :]
_ =0b1010110111110000010100000000
continue
if _ ==-0o6341741624 :
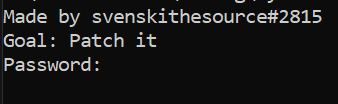
k =re ("test",c ,["Made by svenskithesource#2815\nGoal: Patch it\nPassword: ","yougottapatchit",-41241624687927234 ^(-251732549 %-0o5531324745 *0o1160756515 ),"Success","Wrong", 2],[])
_ =0o15776202751
continue
if _ ==621573266 :
a ="0x50x40x60x40x10x40x50x60x50x10x00x40x90x170x50x60x50x60x00x40x40x170x50x50x00x40x40x150x50x70x60x40x70x40x50x00x60x40x70x4"
_ =-451749950
continue
if _ ==0b1010110111110000010100000000 :
c =[(int (b [i ],544144375 ^ (-0b1011001100000100010000110110100 % 0x337c3495 ^ 756595857) )^(-687239312 ^ (687239306 ^ 0b10100010001111100011001100 // -0o15716756455) ),int (b [i +(1563341570 ^ (1483681242 % 0x1ddc2ca2 + 0o10035757155) )],393866838490878992 ^ (-0x7a5003f7 & 283415444 * 0x52d5603c) )^(-1745991605 ^ (1230286518 ^ -0o4121214407 % -0o7001231102) ))for i in range (-1065277910 ^ (-189868881 % -1821520260 ^ 875557509) ,len (b ),-1262523306 ^ (0o7714673530 // -0o2413002433 & -0x4b4093aa) )]
_ =-0o6341741624
continue
break
Recommended Comments