Hey everyone,
I’m sharing an UnpackMe challenge that combines VMProtect packing with runtime function obfuscation using Eclipse Runtime Obfuscator. This should be an interesting challenge for those who enjoy working with dynamic obfuscation and anti-debugging techniques.
Protection Details:
- VMProtect is used for basic packing, with import protection and anti-debug enabled.
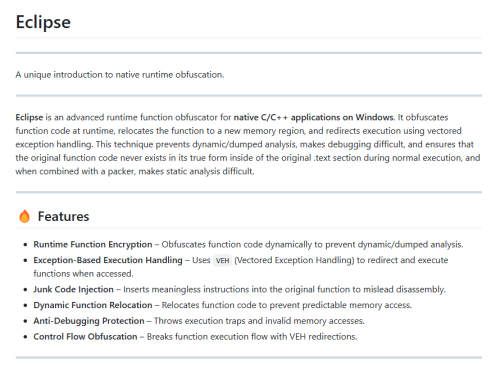
- Eclipse Runtime Obfuscator dynamically obfuscates function execution, making dumped analysis and debugging difficult.
- Function code is relocated to a new memory region at runtime and accessed through vectored exception handling (VEH) instead of direct execution.
-
Eclipse Runtime Obfuscation Features in this UnpackMe:
- Exception-Based Execution Handling – Execution is redirected via VEH, preventing direct tracing.
- Junk Code Injection – Adds meaningless instructions to mislead disassembly and make static analysis harder.
- Dynamic Function Relocation – Functions are moved at runtime, disrupting predictable memory access.
- Control Flow Obfuscation – Execution flow is broken up and redirected via exception handling.
- Anti-Debugging Protection – The binary throws access violations and illegal instructions to interfere with debuggers.
Goals:
- Unpack the binary (remove VMProtect and restore the original imports).
- Defeat runtime function relocation and deobfuscate the function logic by resorting the original function code.
- Reconstruct a clean, runnable (optional) version of the executable with original control flow.
- Explain how you unpacked and fixed the program, detailing the approach to defeating VEH-based execution and restoring the function code.
- Bonus points if you can crack the password in the console application demo code.
Notes:
- VMProtect is only used for packing, not virtualization.
- The main challenge comes from Eclipse’s runtime function relocation and exception-based redirections.
- Dumping the process isn’t enough, as function code is dynamically obfuscated in memory.
- The obfuscated functions are exported and named "testCCode", "testCCode2", and "DemoFunction" (this function has the crackme code in it).
- Would love to see a write-up on defeating the VEH-based execution and restoring the original function code!
More information can be found about the Eclipse Runtime Obfuscator project on GitHub.
Looking forward to seeing your approaches. Good luck and happy reversing!
Edited by C5Hackr
added a "explain how you unpacked it" to the goals, added some extra information on obfuscated code

Recommended Comments