This is a scan tool for Microsoft Windows executables, libraries, drivers and mdumps. Its main objective is to collect the necessary information to facilitate the identification of malicious code within the analyzed files. This tool analyzes, among other things, the PE header and its structure, the content of the sections, the different types of strings, among many other things. It also incorporates a multitude of its own ideas to recognize anomalies in the construction of files and the detection of mechanisms used by current malware.
Using the tool is simple, just configure the options in the drop-down panel on the right and drag the samples into 4n4lDetector.
Full support:
- 32 bits (8086, x86, ARMv7)
- 64 bits (AMD64, x86-64, x64, ARMv8)
TI and ET Extraction:
Alpha AXP, ARM, ARM Thumb-2 (32-bit Thumb), ARM64, EFI Byte Code, EFI Byte Code (EBC), Hitachi SH3, Hitachi SH3, Hitachi SH4, Hitachi SH5, Intel i860, Intel Itanium (IA-64), M32R, MIPS16, MIPS16 with FPU, MIPS R3000, MIPS R4000, MIPS with FPU, MIPS little-endian, MIPS little-endian WCE v2, x64, x86, x86-64.
Buttons code:
- Buttons colored green are action buttons that open files and folders or are used to interact with the tool's utilities.
- The buttons colored in red perform reconfigurations, deletion of data or reset of functional files.
- Purple buttons announce the activation of online interactions.
- The pink buttons are shortcut buttons that the tool uses as tabs to navigate between different types of utilities.
Shortcuts:
- [A] Main analysis tab
- [W] Analysis tab in modifiable HTML format for report (WebView)
- [S] Viewer of strings extracted from the parsed file
- [V] Module with the Virustotal report using its API
Detections:
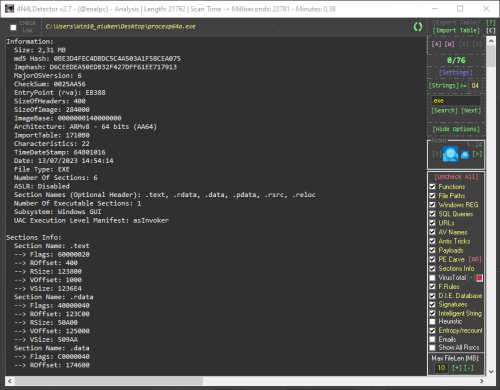
- PE Information
- Unusual Entry Point Position or Code (Algorithms, Anomalous Instructions... )
- Packers
- Compilations
- Binders/Joiners/Crypters
- Architectures
- Possible malicious functions
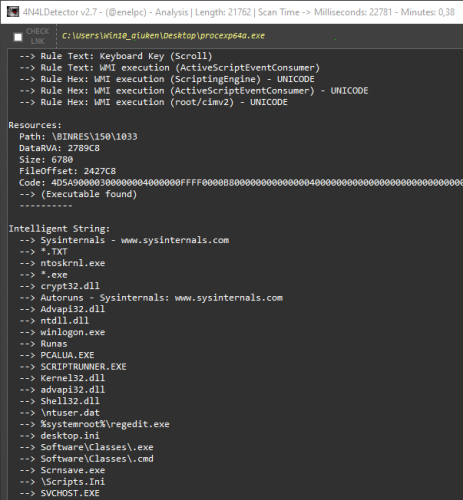
- Registry Keys
- Files Access
- Juicy Words
- Anti-VM/Sandbox/Debug
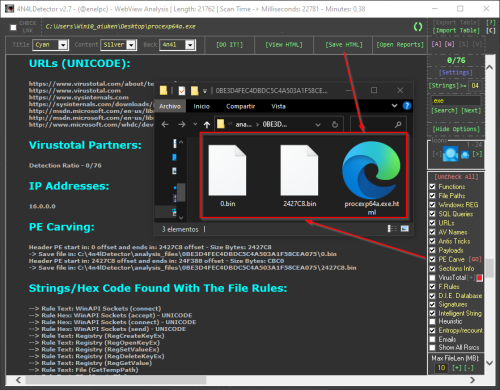
- URLs Extractor
- Payloads
- AV Services
- Duplicate Sections
- IP/Domains List
- Config RAT (Only In Memory Dumps)
- Call API By Name
- Unusual Chars In Description File (Polymorphic Patterns)
- Rich Signature Analyzer
- CheckSum Integrity Problem
- PE Integrity Check
- SQL Queries
- Emails
- Malicious resources
- PE Carve
- Exploits
- File Rules for Entry Points and more... 😃
Console Options (Analysis to file):
- 4n4lDetector.exe Path\App.exe -GUI (Start the graphical interface parsing a file from the console)
- 4n4lDetector.exe Path\App.exe -GREMOVE (Remove binary after scan)
- 4n4lDetector.exe Path\App.exe -TXT (Parse a file from the console and the output is written to a TXT file)
- 4n4lDetector.exe Path\App.exe -HTML (Parse a file from the console and the output is written to HTML file)
Edited by 4n0nym0us
What's New in Version 3.4.0
Released
Changelog v3.4:
Optimization of the string cleaner, improving overall analysis speed.
Security review of the File Access execution extraction section.
Fixed a bug that could affect reading sections from the DIE library.
Improved handling of errors related to the number of corrupted sections.
Enhanced error handling when opening malformed files.
Replaced some RVAs with “N/A” where necessary.
Filled detection of empty or out-of-range resource fragments with “N/A”.
Fixed duplication of IPs found in the IP Addresses module.
Increased detection of multiple TLS callbacks, 32/64-bit support, pointer/indirection support, controlled heuristics, and complete RVA, VA, and section information.
The string search functionality has been reviewed and optimized from the “Strings” button in the right panel.
Speed optimization and security control for Intelligent Strings.
Improved buffer cleanup used in exported function carving.
Optimization for ASCII and NullByte character counting in the “Entropy/recount” section.
Added a general optimization review and new features to the Flow Anomalies module:
Added new detection of anomalous executable sections to the heuristic section.
Added new detection of Exception Hooks to the heuristic section.
Reduced the minimum extraction in the indirect jumps and calls section to 100.
Highlighting with search functionality and a color scale based on criticality:
Yellow: Important but non-critical findings; serve as warnings.
Orange: Potential anomalies or suspicious behavior requiring investigation.
Red: Evidence of malicious activity; requires priority review and in-depth analysis.

-Analysis_Length_4219_ScanTime-_Milliseco.thumb.png.adb594106f8376141771eaee5ba34ea7.png)


Recommended Comments
Create an account or sign in to comment